Cloudflare reports surge in sophisticated DDoS attacks
Hacking groups — many based in Russia — pummeled companies in the second quarter of this year with well-planned distributed denial-of-service (DDoS) attacks, according to new research.
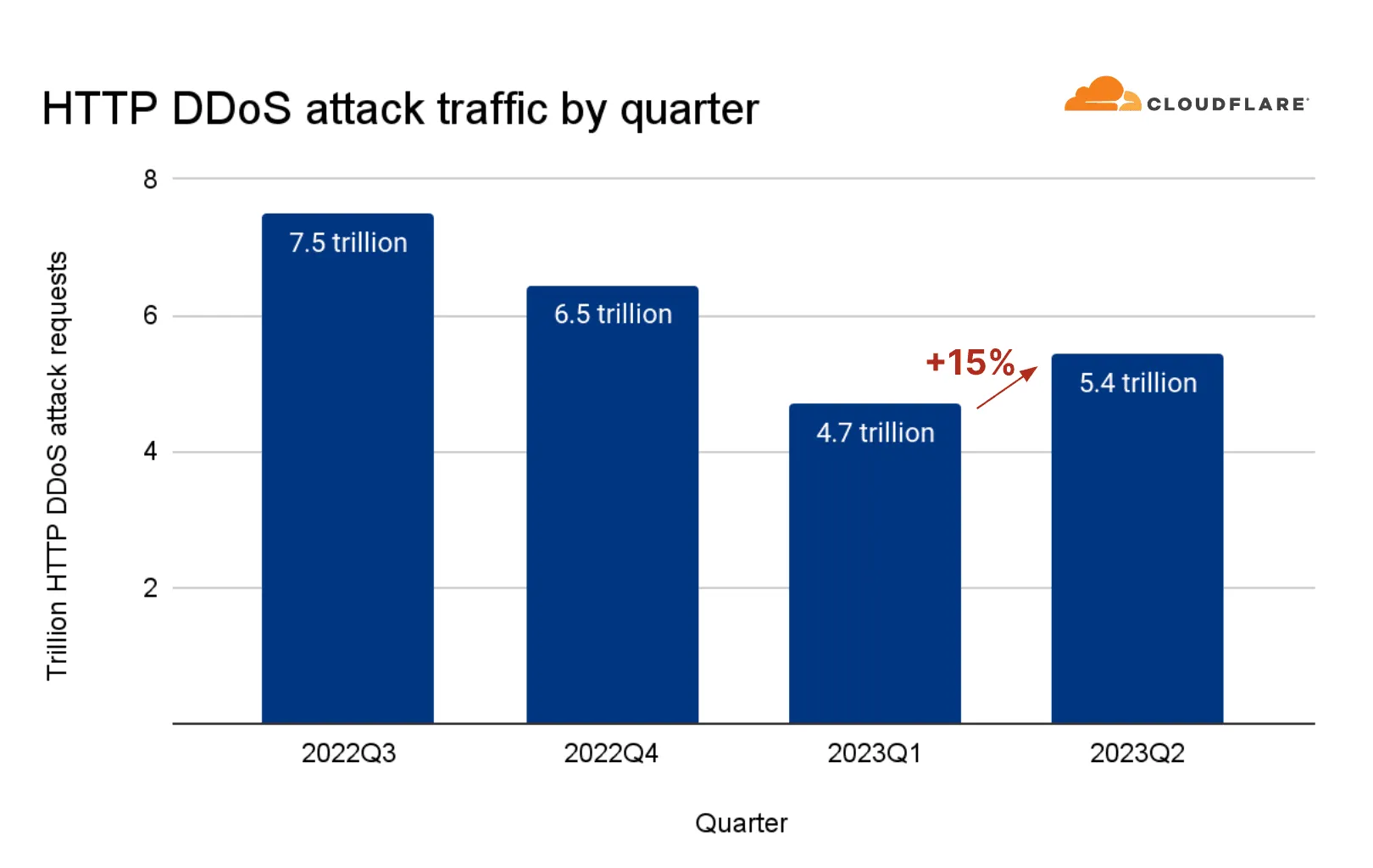
A Tuesday report from content delivery network provider Cloudflare found that the total number of DDoS requests from April to June reached 5.4 trillion — 15% more than in the first quarter of this year.
Although there has been an uptick in attacks in 2023, DDoS incidents are down compared to the second quarter of 2022, when Cloudflare recorded 8.3 trillion requests, the company told Recorded Future News. The amount of requests doesn’t indicate the number of "unique" attacks — rather the total volume of DDoS attacks, according to Cloudflare.
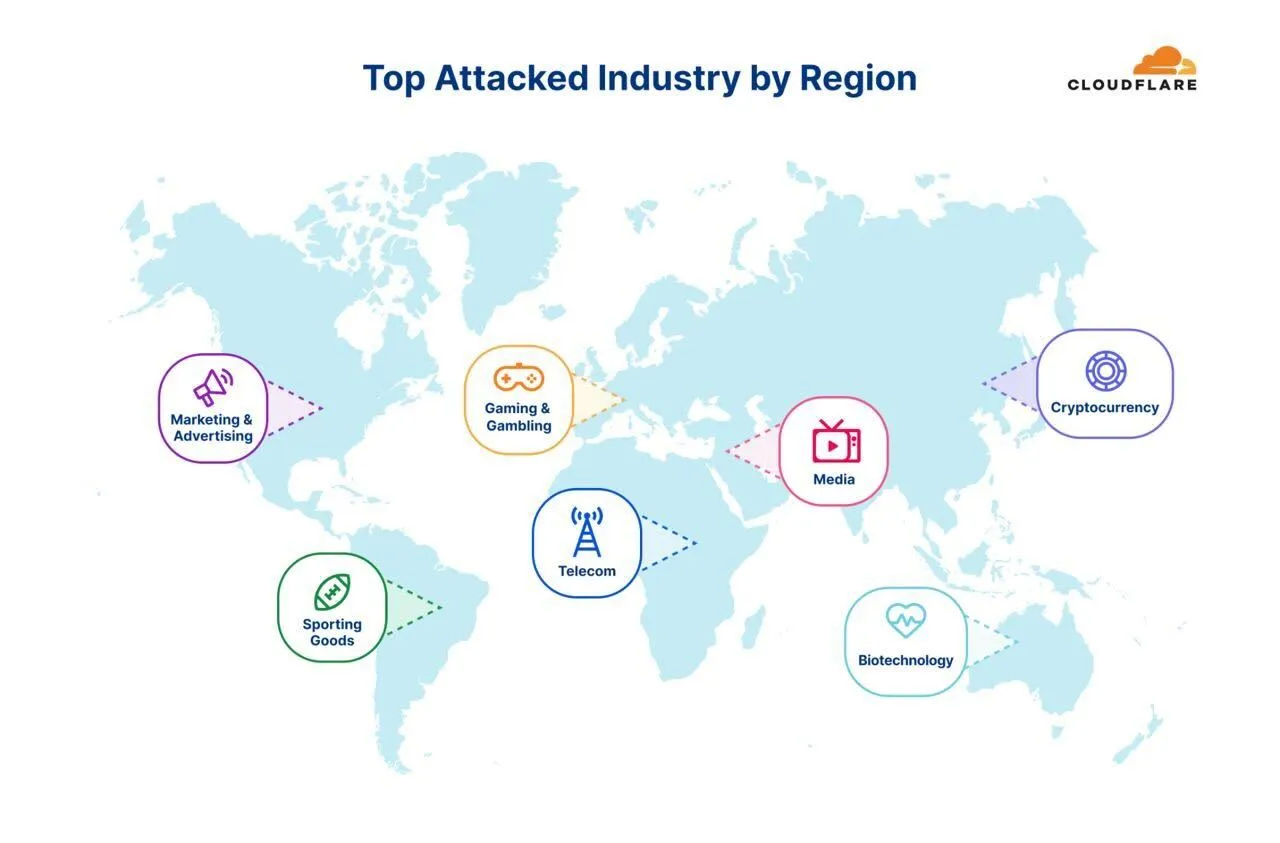
The industries hit hardest by DDoS attacks in recent months were cryptocurrency, gaming and gambling — cryptocurrency companies alone saw a 600% increase in DDoS attacks, Cloudflare said. DDoS attacks work by flooding victim sites with junk traffic, making their services unreachable.
While the largest and most sophisticated DDoS attacks can last only for a few minutes or even seconds, recovering from such attacks can be a lengthy process, Cloudflare said.
Cloudflare said there are several factors contributing to the increase in DDoS attacks globally, including pro-Russia hacktivists targeting Western nations amid the war in Ukraine, the rise of virtual machine botnets, and the exploitation of a zero-day vulnerability in the Mitel business phone system, which has made some attacks more powerful.
In early June, Pro-Russia hacktivist groups including Killnet, REvil, and Anonymous Sudan announced that they would carry out "massive" coordinated DDoS attacks on U.S. and European financial organizations. Other targets included companies involved in computer software, gambling, gaming, telecom, and media.
Over the past few weeks, these hackers launched a minimum of 10,000 DDoS attacks against websites protected by Cloudflare.
Another threat came from the rise in virtual machine botnets, which are up to 5,000 times stronger than those comprised of infected smart devices. A virtual machine (VM) is a software imitation of a physical computer — it allows users to run multiple operating systems or software applications on a single machine. The result is that hackers can launch large-scale DDoS attacks using a relatively small number of computers.
According to Cloudflare, a VM-based botnet executed a 71 million request-per-second DDoS attack in February, the largest on record. Multiple organizations, including an unidentified gaming platform provider, have already been targeted by this new generation of botnets.
The third factor Cloudflare highlighted in its report was a vulnerability identified in March affecting the Mitel MiCollab business phone system, which exposed the technology to be used in DDoS attacks.
The vulnerability — referred to as CVE-2022-26143 — arises when an unsecured UDP port is accessible from the internet. This allows attackers to send a "startblast" command without authentication, essentially flooding the system with simulated calls to test its resilience.
Cloudflare said that the U.S. was the largest source of DDoS attacks, followed by China and Germany. However, the researchers cautioned that the data is skewed by various factors including market size. When researchers compared the attack traffic to all traffic within a given country, they found that Mozambique, Egypt and Finland take the lead as the greatest sources of DDoS attacks relative to their traffic footprint.
Daryna Antoniuk
is a reporter for Recorded Future News based in Ukraine. She writes about cybersecurity startups, cyberattacks in Eastern Europe and the state of the cyberwar between Ukraine and Russia. She previously was a tech reporter for Forbes Ukraine. Her work has also been published at Sifted, The Kyiv Independent and The Kyiv Post.