Chinese espionage tool exploits vulnerabilities in 58 widely used websites
A security researcher has discovered a web attack framework developed by a suspected Chinese government hacking group and used to exploit vulnerabilities in 58 popular websites to collect data on possible Chinese dissidents.
Fifty-seven of the sites are popular Chinese portals, while the last is the site for US newspaper, the New York Times.
In addition, the tool also abused legitimate browser features in attempts to collect user keystrokes, a large swath of operating system details, geolocation data, and even webcam snapshots of a target's face—although many of these capabilities weren't as silent as the exploits targeting third-party websites, since they also tended to trigger a browser notification prompt.
Tetris is a complex web-based spying tool
Named Tetris, the tool was found secretly uploaded on two websites with a Chinese readership.
"The sites both appear to be independent newsblogs," said a security researcher going online under the pseudonym of Imp0rtp3, who analyzed the Tetris attack framework for the first time in a blog post earlier this month.
"Both [sites] are focused on China, one site [is focused on China's] actions against Taiwan and Hong-Kong written in Chinese and still updated and the other about general atrocities done by the Chinese government, written in Swedish and last updated [in] 2016," the researcher said.
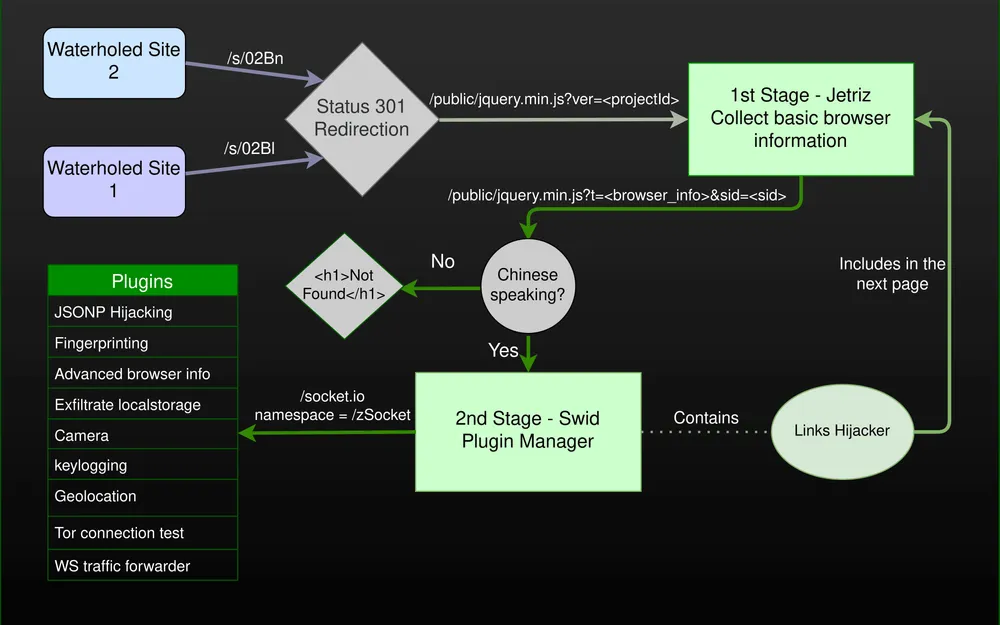
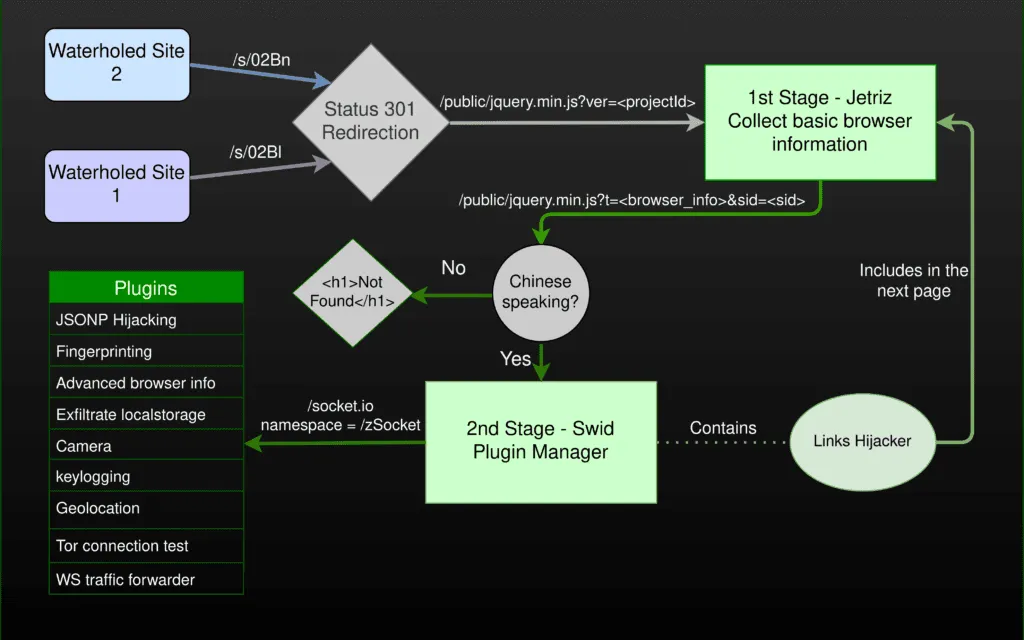
According to Imp0rtp3, users who landed on these two websites were first greeted by Jetriz, the first of Tetris' two components, which would gather and read basic information about a visitor's browser.
If the user had the browser set to use the Chinese language, the would-be victim would be redirected to the second Tetris component.
Named Swid, this component would load 15 different plugins (JavaScript files) inside the victim's browser in order to perform various actions.
Eight of the plugins would abuse a technique called JSON hijacking to open connections to popular websites and retrieve public data about the user on those sites.
While this technique didn't include passwords or authentication cookies, Imp0rtp3 said the attacker could collect information such as usernames, phone numbers, or real names, which could be sometimes used to link a visitor to one of their public personas.
The behavior to scrape data from the 58 third-party websites was completely silent. However, if the attackers couldn't collect enough information to unmask a user, they also had additional plugins at their disposal that, while noisier, could be used as a last-ditch attempt to unmask users.
An inventory of all the Tetris Swid plugins is available below:
- Eight plugins to collect data from remote websites via JSONP hijacking.
- One plugin to collect geolocation data via the user's browser. A permission request would be shown to the user in this case, making the attack easy to spot.
- One plugin to collect the user's internal network IP address via the WebRTC API.
- One plugin to attempt to take a photo of the user via the local webcam. This plugin would also trigger a browser permission request.
- One plugin to log the user's keystrokes on the watering hole domain (but not on third party sites).
- One plugin to determine if the user is using Tor.
- One plugin to connect to the user's system via a websocket and steal local secrets via this technique.
- One plugin to collect extensive technical data about the user's system.
According to Imp0rtp3, data that the attackers could collect through Tetris from third-party websites included:
| Domain | Attributes | Global Alexa Rank | Chinese Rank |
|---|---|---|---|
| tmall.com | isLogin | 3 | 1 |
| qq.com | userId,nickName,headURL,userHome | 4 | 2 |
| baidu.com | userId,userName | 5 | 3 |
| sohu.com | nickName,headURL,userHome,profile,userName | 6 | 4 |
| taobao.com | isLogin | 8 | 5 |
| jd.com | userName,headURL | 10 | 7 |
| weibo.com | userId | 14 | 8 |
| tianya.cn | userName | 42 | 17 |
| aliexpress.com | isLogin | 44 | – |
| gome.com.cn | userId,nickName,headURL | 89 | 26 |
| 163.com | nickName,headURL | 97 | 27 |
| nytimes.com | uid,subscriptions | 113 | – |
| zol.com.cn | userId | 310 | 50 |
| iqiyi.com | userinfo,qiyi_vip_info | 390 | 53 |
| outbrain.com | userName | 419 | – |
| 58.com | userName,userId,phone | 468 | 58 |
| zhibo8.cc | userId,nickName,background,headURL | 482 | 69 |
| dianping.com | userId,nickName | 619 | 93 |
| renren.com | userId,nickName,userName,headURL,birth | 696 | 94 |
| youku.com | userId,userName,sex,headURL | 710 | 104 |
| dangdang.com | ddoy,loginTime | 799 | 109 |
| anjuke.com | userId,userName,lastUser,profileURL | 844 | 119 |
| smzdm.com | userId,nickName,headURL | 1489 | 207 |
| ifeng.com | isLogin,isLogin | 1607 | 218 |
| 7k7k.com | userId,userName,nickName,headURL,level | 1902 | 216 |
| zhaopin.com | userName | 2587 | 289 |
| 4399.com | isLogin,gameInfos | 2764 | 254 |
| ctrip.com | userName,level | 3185 | 346 |
| 10086.cn | userName | 4047 | 383 |
| hupu.com | userId,userName | 4440 | 543 |
| vip.com | level,lastLogin | 6074 | 1519 |
| pconline.com.cn | userId,nickName | 7303 | 773 |
| xunlei.com | nickName,payName,userName | 8680 | 2126 |
| xcar.com.cn | headURL,userName,userName | 10868 | 1157 |
| qunar.com | isLogin | 11185 | 1708 |
| pcauto.com.cn | userId | 11410 | 2117 |
| jumei.com | nickName,userId | 14264 | 1726 |
| 37.com | userName,lastLoginIP,lastLoginTime | 14905 | 1548 |
| hexun.com | userId,userName,headURL,sex | 20653 | 2480 |
| suning.com | phone,headURL,level | 28883 | 2845 |
| lu.com | userId,sex,realName,userName,mobile | 29184 | 2985 |
| tiexue.net | userId,userName | 31430 | 3235 |
| baihe.com | userId,nickName,gender,age,headURL,cityID | 36791 | – |
| bbs.360safe.com | userName,userId,email,adminId,lastVisit,group | 39660 | – |
| qyer.com | username,userid | 43347 | – |
| 56.com | userHome | 48982 | – |
| zongheng.com | level,headURL | 59346 | – |
| ziroom.com | userName | 74364 | 3702 |
| bitauto.com | userId,userName | 84849 | – |
| chinaiiss.com | userName | 119808 | – |
| 2144.cn | userId,userName,nickName | 199953 | – |
| yhd.com | userName,headURL | 343737 | – |
| letv.com | userId | 671069 | – |
| readnovel.com | userName,headURL | 1167917 | – |
| duoshuo.com | userId,userName,userHome,headURL,social_uid,email | – | – |
| aliyun.com | userId | – | – |
| huihui.com | uid,userName | – | – |
| daijun.com | userName | – | – |
Tetris framework usage linked to a Chinese threat actor
But while analyzing the technical intricacies of cyber-espionage tools is all fine and dandy, knowing who uses these tools and against who is also of importance when it comes to warning and protecting their victims.
On this front, the researcher assessed with high confidence that the group using the framework was working on behalf of the Chinese government.
This assessment is backed by the threat actor's attempts to limit the attack to a very narrow category of users who use Chinese keyboards and are accustomed to reading news articles critical of the Chinese government—and most likely part of the Chinese opposition movement, activists, and dissidents.
The researcher also noted that the abuse of the JSONP hijacking technique to retrieve user details from third-party sites when a user visits a "watering hole" portal has also been seen before in 2015. During that campaign, a Chinese threat actor used what appears to be a simpler version of the Swid plugins against Chinese visitors of NGO, Uyghur, and Islamic websites.
While web-based attack tools like Tetris aren't a common sight in cybersecurity reports these days, as most threat actors like to rely on spear-phishing and malware, they are still useful for attackers as they can be used to identify possible targets of interest that can be arrested in the real world or targeted at a later day with malware.
Imp0rtp3 said that users who'd like to protect themselves against such tools are recommended to use the NoScript browser add-on or to visit sites using Incognito (Private Browsing) Mode.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.