British cyber agency issues warning over Russian and Iranian espionage campaigns
Two separate but similar espionage campaigns from Russian and Iranian-linked groups have prompted a warning from Britain’s National Cyber Security Centre.
In a document published on Thursday local time the NCSC warned how instead of sending surprise phishing emails, the hacking groups – identified as "Russia-based" SEABORGIUM and "Iran-based" APT42, or Charming Kitten – are contacting their targets in a benign fashion and attempting to build a rapport and a sense of trust.
Only after this has been established do the groups attempt to dupe their victims into visiting a website which looks like the real sign-in page of a legitimate service, such as Gmail or Office 365, but is actually designed to harvest the target’s log-in credentials.
Individuals working in “academia, defence, government organisations, NGOs, think-tanks, as well as politicians, journalists and activists,” are being targeted by the two groups. The attackers use “open-source resources to conduct reconnaissance, including social media and professional networking platforms” before reaching out.
“Having taken the time to research their targets’ interests and contacts to create a believable approach,” the hackers start to build a rapport with their targets, often beginning “by establishing benign contact on a topic they hope will engage their targets,” NCSC said.
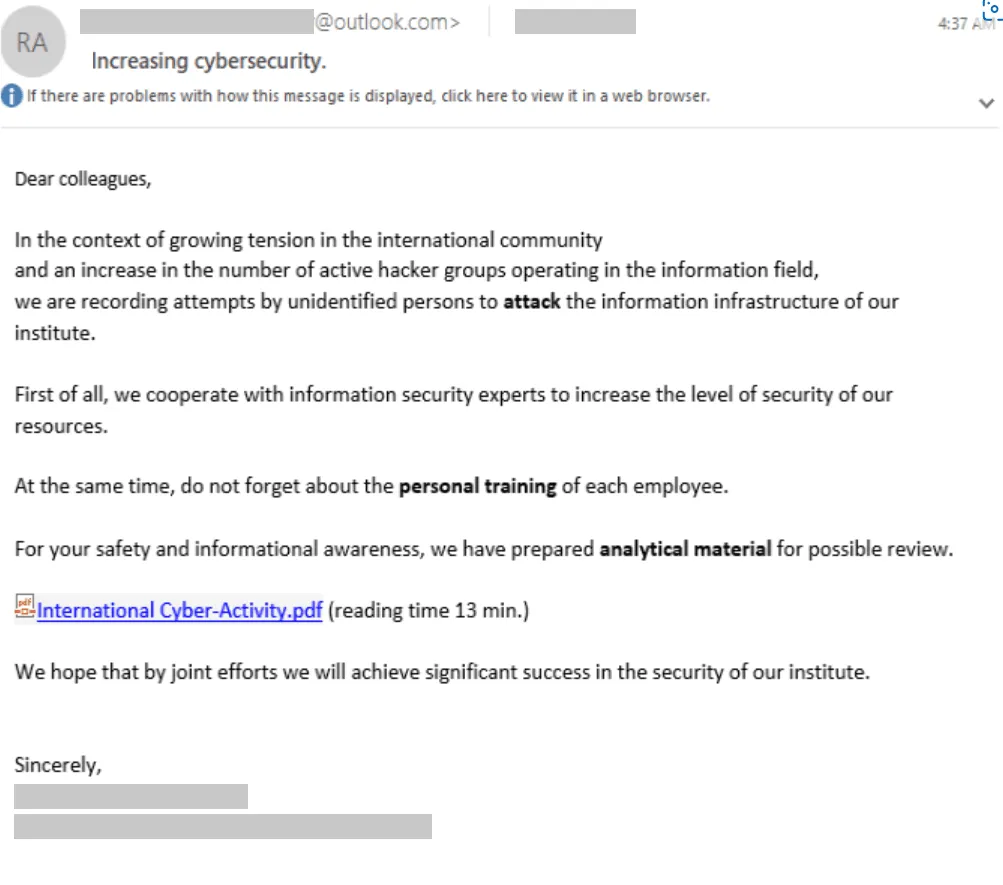
“Once trust is established, the attacker uses typical phishing tradecraft and shares a link, apparently to a document or website of interest. This leads the target to an actor-controlled server, prompting the target to enter account credentials.”
After these credentials are compromised, the groups “then use the stolen credentials to log in to targets’ email accounts, from where they are known to access and steal emails and attachments from the victim’s inbox. They have also set-up mail-forwarding rules, giving them ongoing visibility of victim correspondence.”
Although many cybersecurity researchers have labeled the entities as nation-state hacking groups, the NCSC has not formally attributed the campaigns to the governments of Iran and Russia. Typically the United Kingdom regards attribution to a state as a political declaration normally reserved for the Foreign Office.
Targeting by the Iran-based group
Charming Kitten has been described as state-sponsored by numerous specialist companies — including Google, Recorded Future and Proofpoint — on the basis of its apparent intelligence-gathering rather than financial motivation.
Last December, Human Rights Watch said that Charming Kitten was behind a well-resourced and ongoing international cyber espionage campaign that had aimed to compromise the accounts of a member of the organization’s staff by having them enter their login credentials into a webpage that the hackers controlled.
After investigating the infrastructure being used to support the campaign, HRW discovered 44 phishing pages crafted to look like Microsoft, Google or Yahoo! login pages, displaying the email addresses of the targets who were human rights activists, journalists, diplomats and politicians working in the Middle East and North Africa.
The pages were designed to capture both the target’s email password and any secondary authentication codes, although the phishing kit would not have been able to bypass a hardware-based authentication key using the FIDO protocols.
Among the industry research linked to by the NCSC's advisory is a publication by CERTFA (the ‘Computer Emergency Response Team in Farsi’), a mostly anonymous collective that tracks Iranian cybercriminals and state-sponsored hackers targeting Iranian citizens around the world.
CERTFA’s founder, Amin Sabeti, told The Record he knew of at least two cases of people in the U.K.being targeted by the Charming Kitten campaign. He explained how the espionage can pose various risks to these individuals, including even exposing their network of contacts inside Iran.
“If the individual works with them, the network will end up in prison in Iran or [the government will] use the material against the target to discredit them. For example, we have seen leaks of emails from prominent activists that the IRGC [Islamic Revolutionary Guard Corps] has been trying to discredit in the public's eye,” explained Sabeti.
Last year, the head of MI5, the U.K.’s domestically-focused security service which takes the lead on counter-terrorism and counter-espionage, warned that there had been at least 10 potential threats by Iran to "kidnap or even kill" British or U.K.-based people who were perceived as enemies of the regime.
It is not known what links, if any, these threats share with the Charming Kitten espionage campaign, but Sabeti told The Record he believed that Charming Kitten was linked to the IRGC and that he wouldn't be surprised to read a news story announcing that one of the campaign's targets had been killed.
"For example, imagine if the IRGC can convince someone to go to a country where the IRGC can run ops easily, such as Armenia, by impersonating someone and then inviting the target for a face-to-face meeting, workshops, speech, educational opportunity, etc," he said.
The IRGC has claimed that it lured Ruhollah Zam, a dissident accused of inspiring protests in Iran and who had been living in exile in France, back to the country in 2019. Zam had reportedly visited a potential romantic interest in Iraq whom he had met online before the IRGC announced his capture. He was executed a year later.
Targeting by the Russia-based group
SEABORGIUM is described by Microsoft as “a threat actor that originates from Russia, with objectives and victimology that align closely with Russian state interests.”
The group “primarily targets NATO countries, particularly the US and the UK” said researchers from Microsoft Threat Intelligence Center (MSTIC), and has a “high interest in targeting individuals” rather than corporations. Almost a third of the alerts which the company has sent out to potential victims were to people with consumer Microsoft email accounts.
As reported by Reuters, the group has also been linked to a website that published stolen private emails from several leading Brexit supporters, including the former chief of the Secret Intelligence Service, Sir Richard Dearlove, in an influence operation presenting the emails as evidence of a conspiracy.
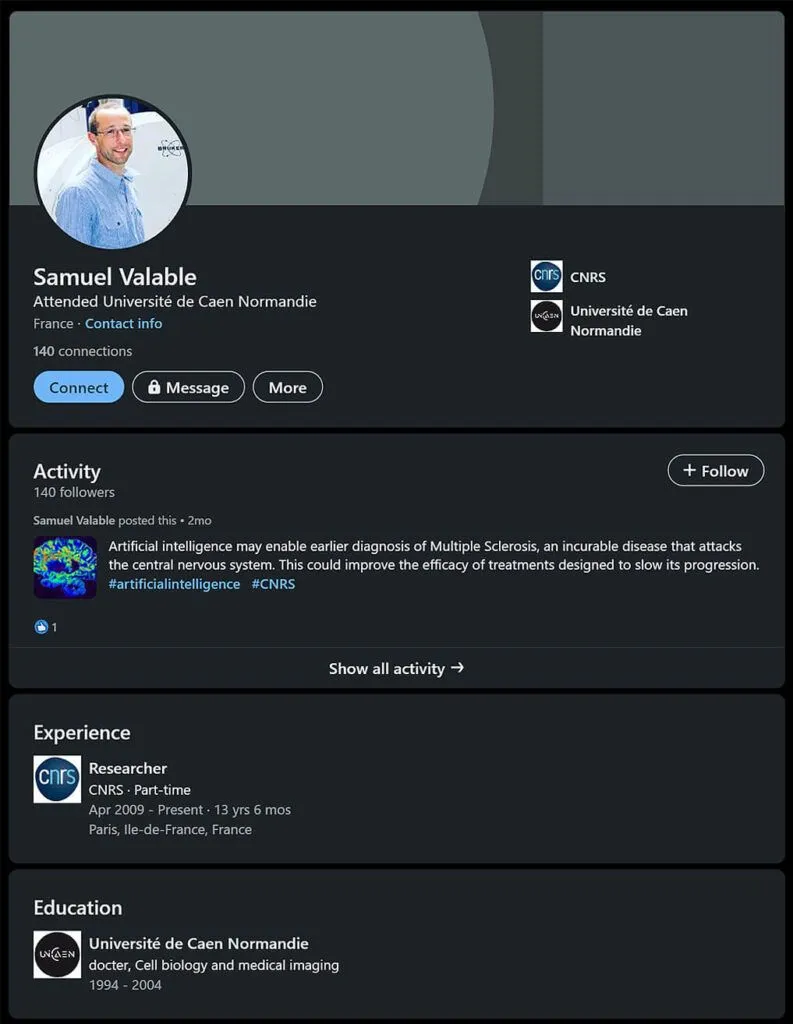
It is not clear what interaction if any Dearlove had with the group before it accessed his ProtonMail account, however Microsoft’s article on the group has revealed it has — similarly to Charming Kitten — created fake profiles on LinkedIn “for conducting reconnaissance of employees from specific organizations of interest.”
“While the malicious campaigns use similar techniques and have similar targets, the campaigns are separate and the two actors are not collaborating,” the NCSC’s advisory stated.
In a statement published alongside the advisory, the NCSC's director of operations, Paul Chichester, said: “The UK is committed to exposing malicious cyber activity alongside our industry partners and this advisory raises awareness of the persistent threat posed by spear-phishing attacks.
“These campaigns by threat actors based in Russia and Iran continue to ruthlessly pursue their targets in an attempt to steal online credentials and compromise potentially sensitive systems. We strongly encourage organisations and individuals to remain vigilant to potential approaches and follow the mitigation advice in the advisory to protect themselves online.”
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and is also a fellow at the European Cyber Conflict Research Initiative.



