Iranian espionage campaign targets journalists, diplomats, activists, says Human Rights Watch
A well-resourced and ongoing international cyber espionage campaign targeting human rights activists, journalists, diplomats and politicians working in the Middle East has been uncovered by Human Rights Watch (HRW), the NGO said on Monday.
The advocacy organization’s joint technical analysis, conducted alongside Amnesty International’s Security Lab, attributed the campaign with high confidence to a hacking group that numerous specialist companies including Google, Mandiant, Recorded Future and Proofpoint, have said is sponsored by the Iranian government.
After identifying and contacting more than a dozen victims who were unaware their accounts had been compromised, HRW has called for Google to strengthen the security protections it provides for Gmail users, whose log-in credentials were stolen as part of the social engineering and phishing campaign.
The NGO complained that the lack of any permanent security notifications that attackers can’t delete is leaving victims in the dark, even though Google’s security features do allow informed users to identify who had been logging in to their accounts — one example in this campaign involved someone using an IP address in Tehran.
How was the campaign uncovered?
In October, a Human Rights Watch staff member focusing on the Middle East and North Africa received a suspicious contact via WhatsApp from an individual who claimed to work for a Lebanese think tank, inviting them to appear at a conference.
This individual eventually sent a phishing link to the target over the app which directed them to a fake Microsoft login page, tailored to mimic the target’s real Office 365 account, using the curly.biz link shortening service.
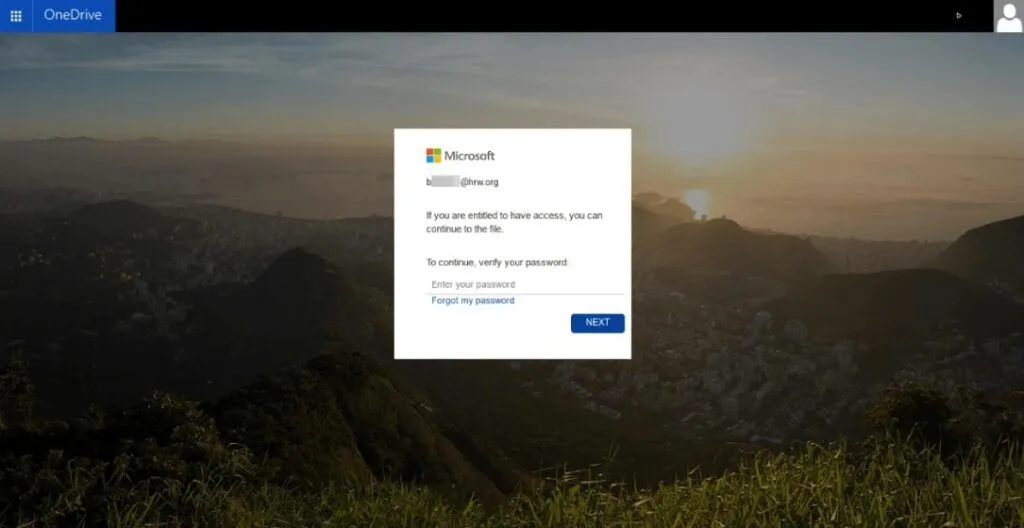
The page was designed to capture both the target’s email password and any secondary authentication codes, although the phishing kit would not have been able to bypass a hardware-based authentication key using the FIDO protocols.
A joint technical investigation by Human Rights Watch and Amnesty International’s Security Lab was able to examine the link shortening service to identify similar pages set up to mimic the email accounts of the campaign’s additional targets.
Human Rights Watch explained that the phishing link “included a random path of five
characters, both lowercase letters and numbers, which represents around 6 million combinations, making it possible to enumerate all of the existing paths on the attacker’s infrastructure to find other existing links.”
Doing so the NGO discovered 44 valid URLs, many redirecting to phishing pages crafted to look like Microsoft, Google or Yahoo login pages, that displayed the email addresses of the targets.
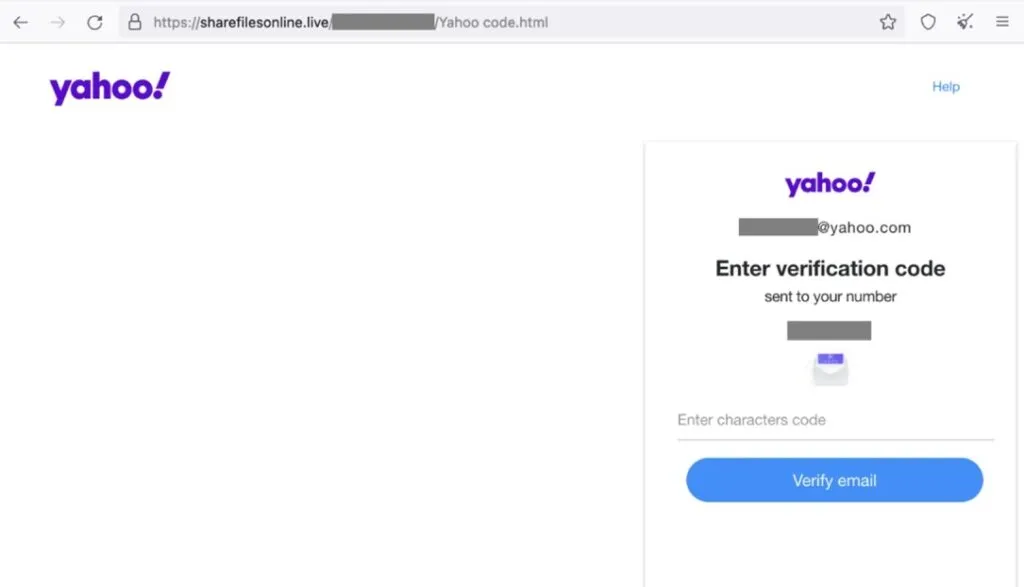
Victims include major U.S. newspaper correspondent
The researchers then reached out to the 18 “high-profile individuals” who were identified, including six journalists. Fifteen of them responded and confirmed they had received the same WhatsApp messages between September 15 and November 25.
At least three of these individuals had their email accounts, cloud storage drives, calendars and contacts compromised by the campaign, including “a correspondent for a major US newspaper, a women’s rights defender based in the Gulf region, and Nicholas Noe, an advocacy consultant for Refugees International based in Lebanon,” said HRW.
The attackers “also performed a Google Takeout, using a service that exports data from the core and additional services of a Google account” to exfiltrate a large amount of data from the victims’ accounts.
“Individuals successfully targeted by the phishing attack told Human Rights Watch that they did not realize their Gmail accounts had been compromised or a Google Takeout had been initiated, in part because the security warnings under Google’s account activity do not push or display any permanent notification in a user’s inbox or send a push message to the Gmail app on their phone,” stated HRW.

“Google’s security activity revealed that the attackers accessed the targets’ accounts almost immediately after the compromise, and they maintained access to the accounts until the Human Rights Watch and Amnesty International research team informed them and assisted them in removing the attacker’s connected device.”
HRW called for Google to “promptly strengthen its Gmail account security warnings to better protect journalists, human rights defenders, and its most at-risk users from attacks.”
"Helping people stay safe online is our top priority, which is why we design our products with built-in protections and have teams like our Threat Analysis Group (TAG) and Mandiant Threat Intelligence to track and disrupt cyber threats," a Google spokesperson said. "We implement protections, both for everyday and high risk users, so their Google Accounts are protected against threats against Google services, or on other platforms as seen in this case. Some of these protections include our Advanced Protection Program (APP) and 2-Step Verification (2SV) auto enrollments. Google also remains committed to threat collaboration and sharing our ongoing research to raise awareness on bad actors across the industry, as it helps to more quickly respond to attacks and protect online users."
The spokesperson added that TAG and Mandiant "have confidence these campaigns are linked to APT42," an Iranian state-sponsored cyber espionage group.
Recorded Future, which has previously investigated the group linked to the attacks, was one of the cybersecurity firms Human Rights Watch consulted regarding the incident. The Record is an editorially independent unit of Recorded Future.
“Iran’s state-backed hackers are aggressively using sophisticated social engineering and credential harvesting tactics to access sensitive information and contacts held by Middle East-focused researchers and civil society groups. This significantly increases the risks that journalists and human rights defenders face in Iran and elsewhere in the region,” said HRW’s Ghattas.
She added: “In a Middle East region rife with surveillance threats for activists, it’s essential for digital security researchers to not only publish and promote findings, but also prioritize the protection of the region’s embattled activists, journalists, and civil society leaders.”
Updated 12/6/2022 to include a statement from Google.
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and is also a fellow at the European Cyber Conflict Research Initiative.



