Atlassian says employee, company info stolen from third-party app
UPDATE: Representatives from Atlassian and Envoy confirmed that the breach involved the compromise of an Atlassian employee account on Envoy and not any systems at either company.
“We found evidence in the logs of requests that confirms the hackers obtained valid user credentials from an Atlassian employee account and used that access to download the affected data from Envoy’s app. We can confirm Envoy’s systems were not compromised or breached and no other customer’s data was accessed,” an Envoy spokesperson said.
Atlassian said its security team is now “exploring all possible avenues to understand how the threat actor gained access and working closely with Envoy to do so.”
“While we do not wish to speculate, for the sake of clarification, we are aligned with Envoy in the belief that our app data was not compromised due to a breach of their systems,” the spokesperson told The Record.
PREVIOUSLY: Data related to $44 billion software company Atlassian was stolen from a third-party application, the company confirmed on Thursday, after hackers published troves of the information on Telegram.
A spokesperson for Atlassian told The Record that Envoy, an app that helps companies organize office spaces, was compromised and that Atlassian only learned of the breach on Wednesday.
The spokesperson said customer and product data is not accessible via the app, but the information stolen appears to include employee records, building floor plans and more.
In a statement to The Record, an Envoy spokesperson denied that the breach involved a compromise of their systems.
“Our initial research shows that a hacker gained access to an Atlassian employee’s valid credentials to pivot and access the Atlassian employee directory and office floor plans held within Envoy’s app,” the spokesperson said.
Envoy has dozens of high-profile customers including Slack, Pinterest, the Golden State Warriors, the Salvation Army, Hulu and Lululemon.
The hack came to light on February 15 when a group calling itself SiegedSec posted on Telegram claiming it hacked the tech giant alongside photographs of the records.
SiegedSec taunted Atlassian with several Valentines Day-themed messages connected to the stolen documents.
“The safety of Atlassians is our priority, and we worked quickly to enhance physical security across our offices globally. We are actively investigating this incident and will continue to provide updates to employees as we learn more,” the Atlassian spokesperson said.
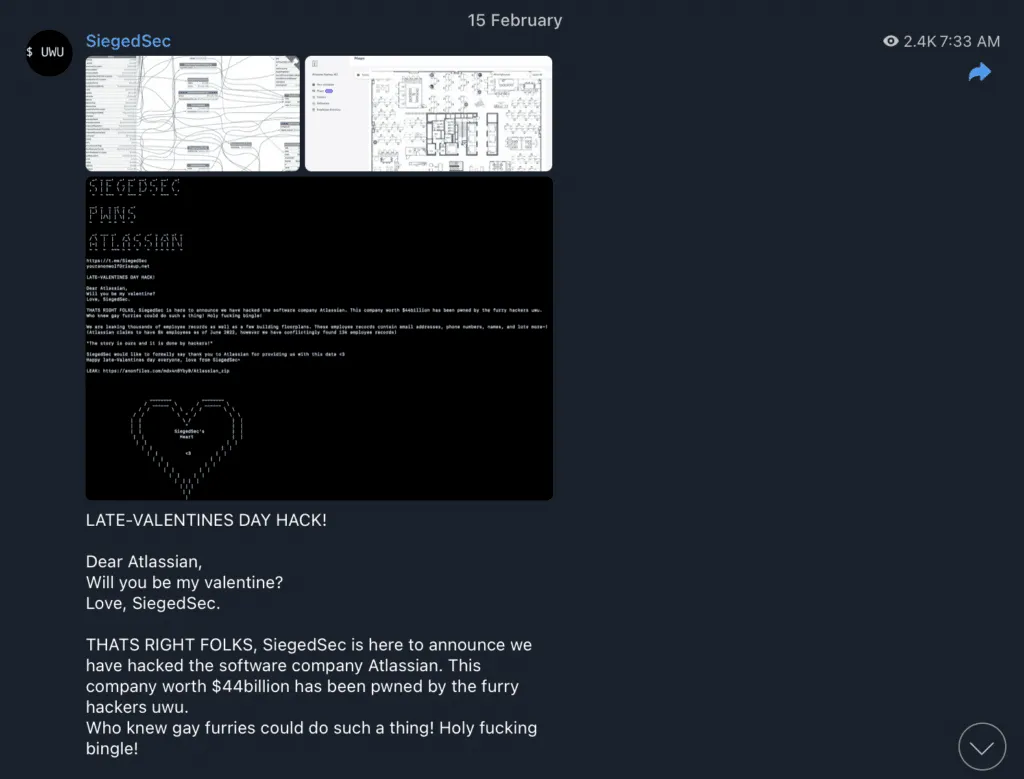
Security researchers from Check Point examined the documents and found two floor maps for Atlassian’s San Francisco office as well as a JSON file with nearly 14,000 records containing names, phone numbers, emails and more.
Check Point confirmed Atlassian’s assessment that the group “did not hack Atlassian directly.”
According to Check Point, the SiegedSec group has been active since April 2022, and researchers said they “have yet to unveil the agenda or their origins.”
SiegedSec made headlines last year when it claimed to have stolen internal documents from the state governments of Kentucky and Arkansas in response to their abortion bans following the Supreme Court decision overturning Roe v. Wade.
Representatives for governors of both states told The Record that the information was publicly available and not private.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.

