Zoho warns of new zero-day vulnerability exploited in attacks
Zoho urged customers on Friday to update their ManageEngine servers and apply a software fix that patches a zero-day vulnerability that is currently being exploited in the wild.
Tracked as
In a security advisory, the company said it patched a bug that would have allowed attackers to bypass authentication and run malicious code on Desktop Central servers.
"As we are noticing indications of exploitation of this vulnerability, we strongly advise customers to update their installations to the latest build as soon as possible," the company told customers.
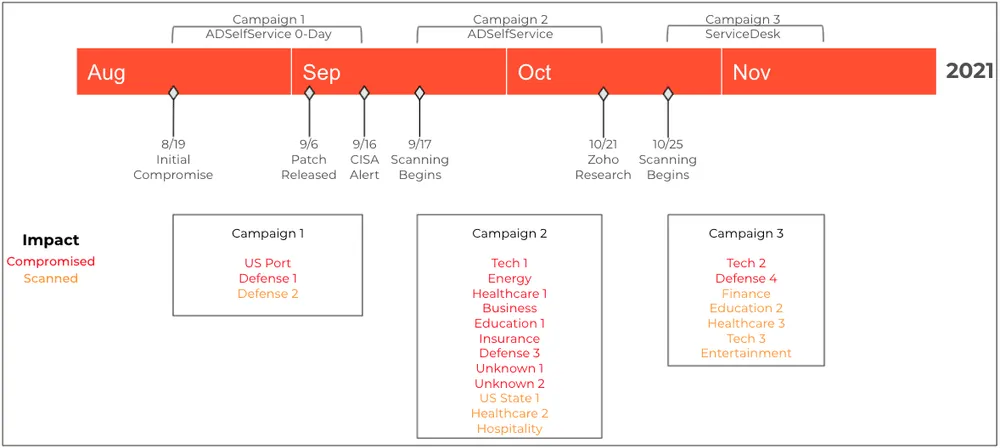
The company did not share any details about the threat actor(s) exploiting this bug, but the advisory comes after state-backed groups have already exploited two other vulnerabilities in ADSelfService Plus (CVE-2021-40539) and ServiceDesk Plus (CVE-2021-44077) software packages to compromise its customers' networks already.
Attacks against the first began as early as August, according to CrowdStrike, CISA, and Palo Alto Networks, and attacks against the second bug began in November, according to Palo Alto Networks and CISA.
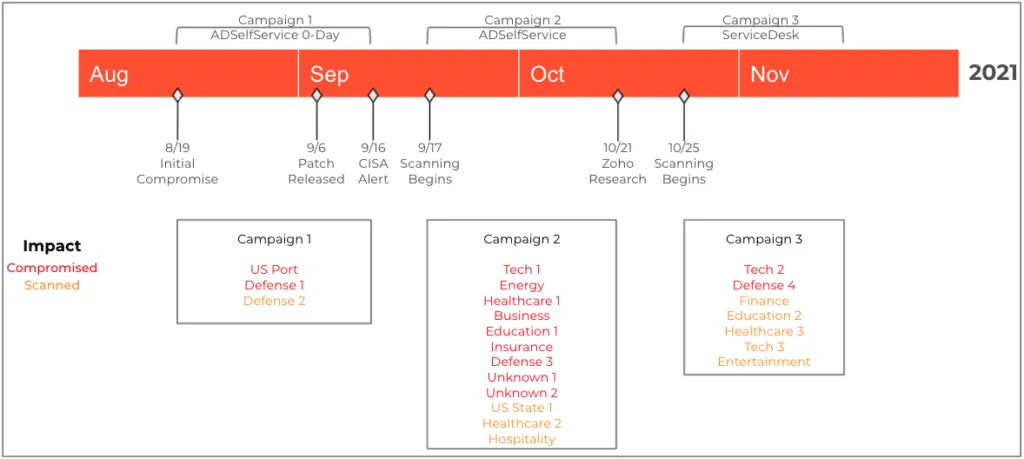
According to Palo Alto Networks, the targets of these previous attacks included several organizations in the US defense sector. It is believed that the purpose of these attacks is cyber-espionage and data theft.
While it is currently unconfirmed that the same nation-state groups are behind the exploitation of this third vulnerability, companies should exercise caution and update their Zoho servers as soon as possible.
There are currently approximately 3,100 Zoho ManageEngine Desktop Central servers connected to the internet, ripe for exploitation.
While previously Zoho released some steps to discover if a server has been hacked, there are no such instructions or steps at the time of writing, meaning Zoho customers will also most likely have to initiate incident response procedures right after they patch and inspect servers for the presence of any suspicious files. They can start by looking for the webshells detailed in the two Palo Alto Network and CISA alerts first.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.