What We Know So Far About the FireEye Breach—and Why It Matters
On Tuesday afternoon, cybersecurity firm FireEye announced what is likely one of the most significant cyberattacks of 2020—with itself as the victim.
“A highly sophisticated state-sponsored adversary stole FireEye Red Team tools,” the company said in a statement that included hundreds of countermeasures, released in an effort to help security professionals defend against attacks if the tools are used maliciously.
The attack was notable not just because the fallout could be immense, but because it required a brazenness and skill that only the most sophisticated hacking groups could pull off.
“This attack is different from the tens of thousands of incidents we have responded to throughout the years,” FireEye chief executive Kevin Mandia said in a statement. “The attackers tailored their world-class capabilities specifically to target and attack FireEye.”
In a rare statement, the FBI confirmed that it was investigating the incident and that it appeared to involve a nation state group with “a high level of sophistication.” Congressional leaders said they have asked intelligence agencies to brief them on the incident and vulnerabilities that may arise from it.
Details will likely emerge as the FBI, FireEye, and its partners investigate the incident, but here’s what we know already:
Cybersecurity firms like FireEye are a natural target for sophisticated, nation-state hackers.
In his statement, Mandia said that the hackers operated at a much higher level than other attackers and “used a novel combination of techniques not witnessed by us or our partners in the past.”
Cybersecurity experts from other companies—including FireEye competitors—added that even the best-defended organizations aren’t invulnerable to these types of attacks.
“When you have nation states using advanced technologies to launch targeted attacks against an organization, even a cybersecurity company that has strong cyberdefenses can become a victim,” Steve Grobman, chief technology officer of cybersecurity firm McAfee told The Record in an interview.
Dmitri Alperovitch, a co-founder and former chief technology officer of rival firm CrowdStrike, said in a series of tweets that “it's important to remember that no one is immune to this… Security companies are a prime target for nation-state operators for many reasons, but not least of all is ability to gain valuable insights about how to bypass security controls within their ultimate targets.”
The attackers appear to be Russian.
And perhaps APT29, a hacking group believed to be associated with the Russian Foreign Intelligence Service, or SVR, the Washington Post reported.
According to data collected by Recorded Future, first indications of the group emerged in 2008, but references to the group’s activity escalated in 2014, when security researchers observed signs of attacks against government agencies, including the White House and U.S. State Department.
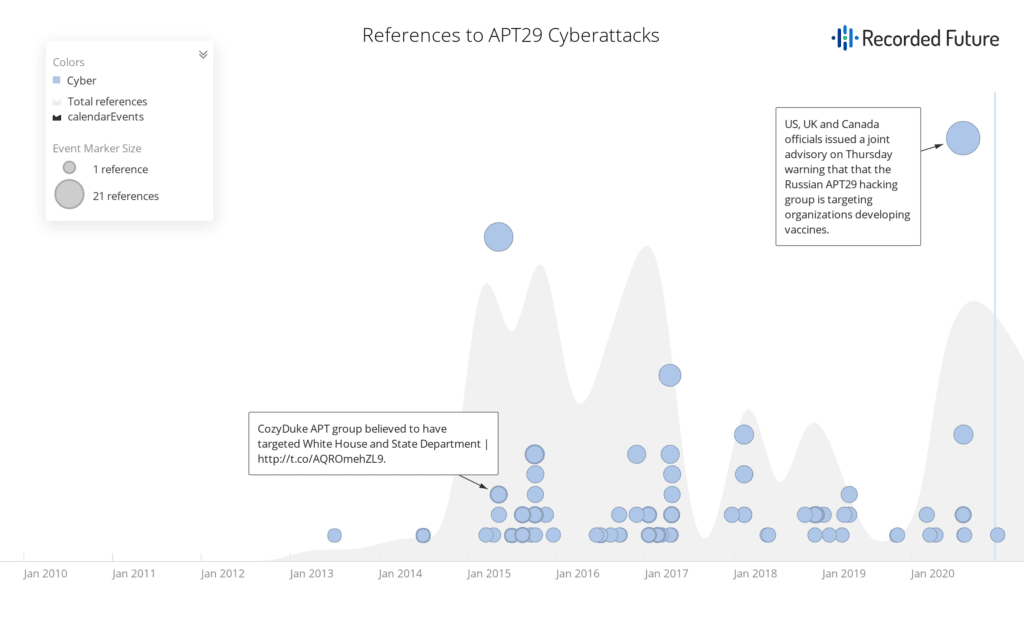
In 2016, the group was implicated in the hacking of the Democratic National Committee in an attempt to interfere in the election process. More recently, the NSA publicly accused the group of trying to steal COVID-19 vaccine research.
Naturally, FireEye was aware of the group and published research detailing its tactics, including domain fronting techniques to get backdoor access to victim environments and targeted phishing campaigns. The New York Times suggested the attack might be a form of revenge, though the group’s motivations are unclear at the moment.
FireEye’s tools are valuable in more ways than one to nation-state hackers.
If a hacking group is skilled enough to break into an organization, why would they be interested in stealing the victim’s cybersecurity tools? One reason is because it can save them time and energy with future attacks.
“Most likely they plan to use this commodity type tooling to cover up their tracks so as to not expose their own custom tools and save those for special attacks or second stage attacks,” Brandon Hoffman, chief information security officer at cybersecurity firm Netenrich said in an email.
Additionally, hackers can use the tools to make attribution harder for cyberdefenders. In recent years, for example, state-sponsored groups have used offensive simulation tools like Cobalt Strike to deploy payloads and manage compromised assets. These tools can be widely—and legitimately—used by red teams to test an organization’s security posture, which means that it can be easy for attackers to deny that they were involved.
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.



