Web skimmers hit 300+ sites hidden inside Google Tag Manager containers
Threat actors have abused a legitimate feature of the Google Tag Manager service to secretly add and deploy malicious JavaScript code to more than 300 e-commerce stores since March this year.
The malicious code—called a "web skimmer" or "Magecart script"—was used to collect the payment card details of online shoppers, data that was later offered for sale on underground carding forums, Gemini Advisory, a Recorded Future division specialized in financial fraud, said today.
In total, this campaign hit 316 online stores and an estimated 88,000 users, who had their data sold online, Gemini Advisory said.
What is Google Tag Manager?
The common trait of this campaign was the abuse of Google Tag Manager, a Google tool that lets website owners dynamically update tracking and analytics code on their sites. More specifically, the attacks abused GTM containers, a feature that can be used to package and ship entire blocks of JavaScript code.
The way the attack worked is that the hackers created their own GTM container, hacked into e-commerce stores, and secretly loaded the code without the owners' knowledge.
The attack worked and remained under the radar for months because web security tools and even website owners inspecting their own code would have had a hard time detecting the malicious GTM container from their own GTM tags.
But Gemini Advisory says that these malicious GTM containers loaded code that collected all the information that buyers added in payment forms, data that it sent to a remote collection server, from where it was later monetized on underground forums.
Two threat actors identified so far
Based on how the malicious GTM containers were abused, Gemini Advisory believes the attacks were orchestrated by two different groups.
The difference between the two is that Group One embedded the entire web skimmer inside their GTM container, while Group Two placed a loader inside the container that ran on the hacked site and loaded the web skimmer through an intermediary step.
"Although the two GTM container variants involve similar tactics—storing
e-skimmers within GTM containers or housing scripts in GTM containers that load e-skimmers from dual-use domains—analysis of the two variants suggest that two different Magecart groups are responsible for each variant," the Gemini Advisory team said in a report today.
The first group was the one that was most active, being responsible for two-thirds of all the hacks.
The first group began operations in March, while the second started its attacks in May. Both hacked online stores running on different platforms, including Magento, WordPress, Shopify, and BigCommerce.
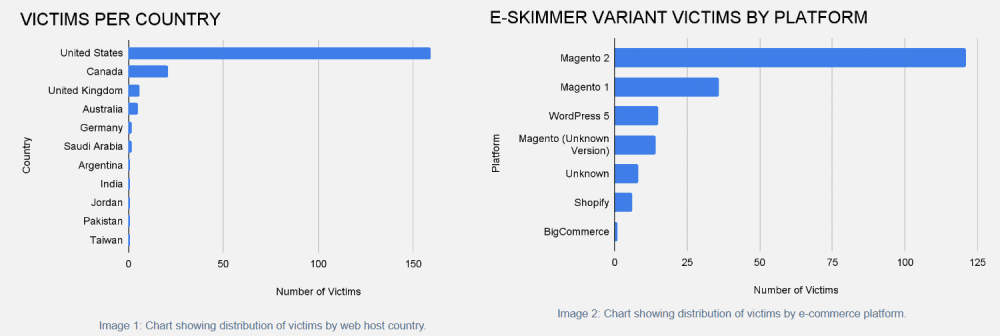
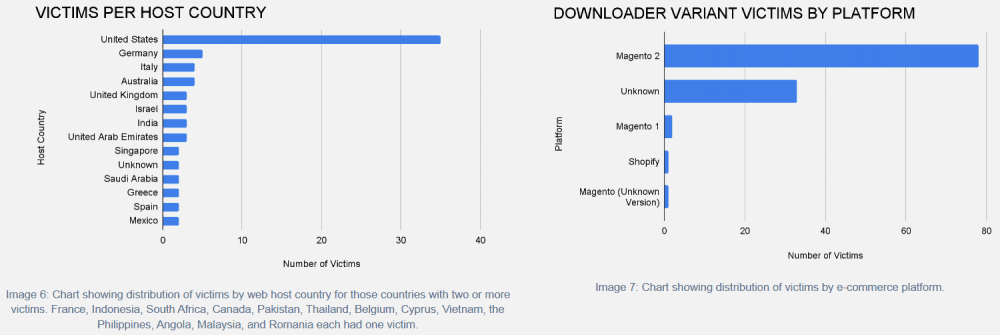
Most of the compromised sites were small online store operations, and only one had enough traffic to be listed in the Alexa Top 50,000, researchers said.
Gemini's findings come just days after security firm RiskIQ disclosed details about another web skimming operation, this time one that targeted WordPress sites running the WooCommerce plugin.
In addition, security firm Sansec has recently disclosed details about different web skimming operations, highlighting a trend where groups are slowly evolving away from web-based compromises to developing their own malware that they insert into hacked sites at the server level, for continued future access (linux_avp, CronRAT, NginRAT).
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.