Wave of Avaddon ransomware attacks triggers ACSC, FBI warning
Cyber-security agencies from Australia and the United States are warning about a wave of attacks carried out with the Avaddon ransomware strain.
The ransomware, which has been active since February 2019, is advertised on underground cybercrime forums as a Ransomware-as-a-Service (RaaS).
Criminal groups rent access to the ransomware, breach victim companies, and then deploy the Avaddon strain to lock systems and demand a ransom.
As of May 2021, Avaddon victims have been recorded worldwide across different industry verticals, the US Federal Bureau of Investigation and the Australian Cyber Security Centre said in alerts published on Wednesday and Friday last week.
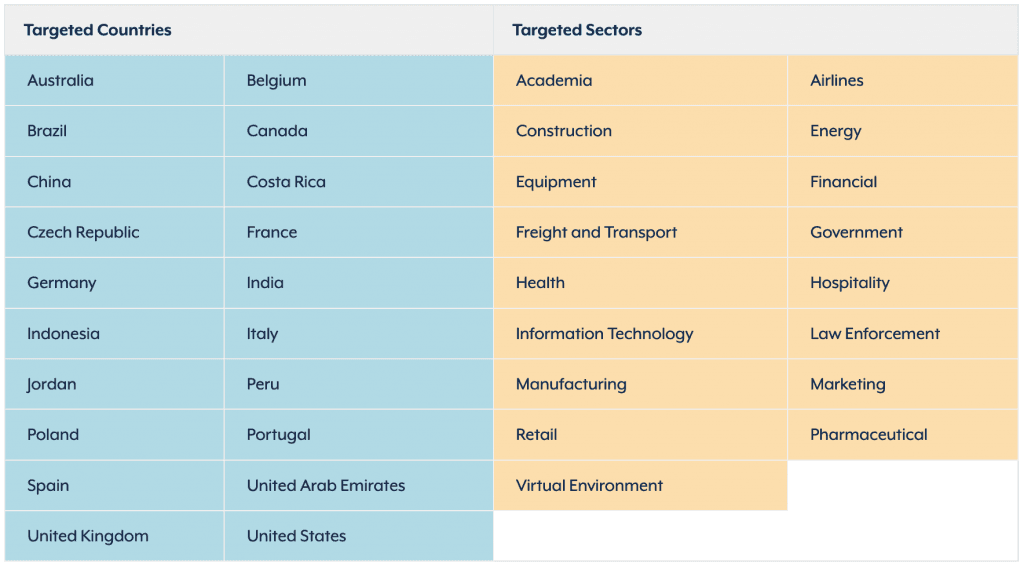
Avaddon have been targeting weakly secured networks
The FBI said the group has been compromising victims by abusing weakly secured systems that employees use for remote access into their own networks.
"Avaddon ransomware actors have compromised victims through remote access login credentials [e.g., remote desktop protocol (RDP) and virtual private network (VPN)] with single-factor authentication or improperly configured RDP," the FBI said.
DarkSide #ransomware Leaks Press Center: pic.twitter.com/NNmv0UphQw
— (@ddd1ms) May 10, 2021
The attackers, which usually avoid attacking organizations located in the Commonwealth of Independent States (CIS), also engage in double-extortion schemes, the two agencies said.
If victims refuse to pay the ransom fee to obtain a decryption key to recover their files and instead choose to restore from backups, the attackers move into a second extortion phase where they threaten companies to release sensitive files they stole from their network prior to encrypting files.
This data is usually leaked in several stages on a dark web portal, called a "leak site," which the group launched in August 2020, imitating other ransomware operations.
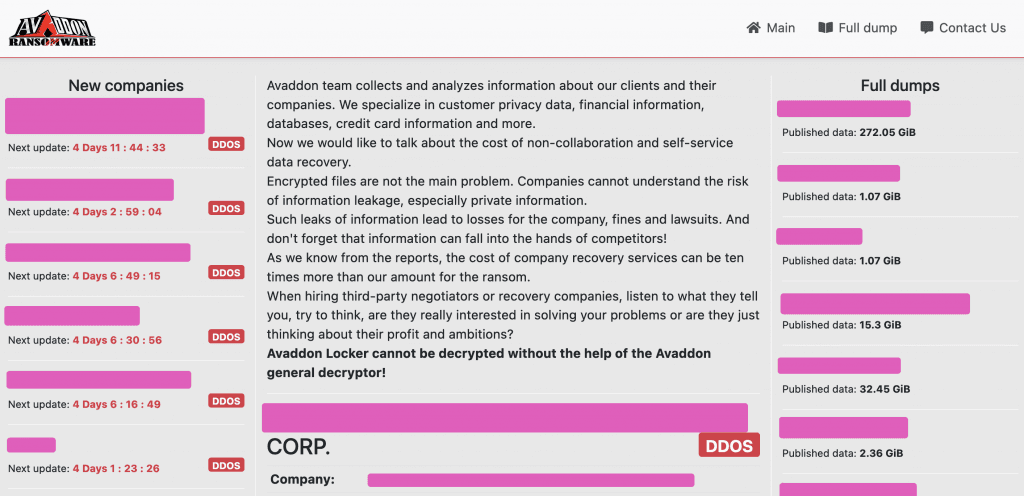
According to the FBI, these leak stages usually follow the pattern below:
- Leak Warning: After initially gaining access to a victim network, Avaddon actors leave a ransom note on the victim's network and post a "leak warning" to the Avaddon TOR leak website. The warning consists of screenshots from files (e.g., sensitive documents) and proof of access to the victim's network (e.g., screenshots of network folders).
- 5 Percent Leak: If the victim does not quickly pay the ransom within 3 to 5 days, Avaddon actors increase the pressure on victims by leaking a portion of the files (as opposed to screenshots). The Avaddon actors leak this data by uploading a small ZIP file to Avaddon's TOR leak website.
- Full Leak: If the ransom is not paid after the 5 percent leak, Avaddon actors post all their exfiltrated data in large ZIP files in the "Full dumps" section of the Avaddon TOR leak website.
In addition, in adverts for their RaaS offering, the Avaddon creators have also bragged about their ability to execute distributed denial of service (DDoS) attacks against organizations in order to put more pressure on victims.
But the FBI said last week that as of April 2021, they had not identified any Avaddon incident where DDoS attacks were involved.
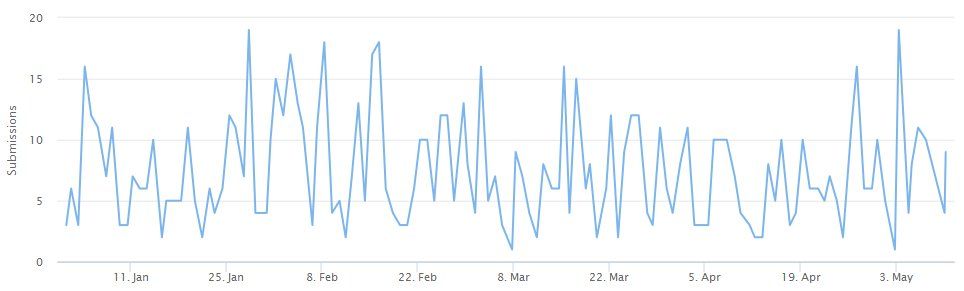
Attacks with the Avaddon ransomware have not been the most widespread this year; however, the operation has been making a steady stream of 10-20 victims per week since the start of the year, according to data provided to The Record by MalwareHunterTeam, one of the people behind ransomware identification service ID-Ransomware.
To help companies prepare and deal with Avaddon attacks, the ACSC has published a publicly accessible security advisory that contains both advice to prevent attacks and indicators of compromise to detect any attempted intrusions.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



