US, UK, and Australia warn of Iranian hacking activity after Microsoft report
Cybersecurity agencies from the US, UK, and Australia have published a joint security alert to raise awareness of an ongoing wave of intrusions carried out by Iranian government-sponsored hacking groups since the start of the year.
The joint advisory, authored by the FBI, CISA, ACSC, and NCSC, comes a day after Microsoft has published its own report on the matter, detailing a rise in the sophistication and number of attacks carried out by Iranian groups.
Joint advisory warns of Fortinet and Exchange exploitation
The joint advisory includes details about attacks during which Iranian hackers targeted Fortinet and Microsoft Exchange servers as a way to breach corporate networks.
The four agencies provided examples of past attacks where Iranian groups used these two technologies as a point of entry:
- In March 2021, the FBI and CISA observed these Iranian government-sponsored APT actors scanning devices on ports 4443, 8443, and 10443 for Fortinet FortiOS vulnerability CVE-2018-13379, and enumerating devices for FortiOS vulnerabilities CVE-2020-12812 and CVE-2019-5591. The Iranian Government-sponsored APT actors likely exploited these vulnerabilities to gain access to vulnerable networks. Note: for previous FBI and CISA reporting on this activity, refer to Joint Cybersecurity Advisory: APT Actors Exploit Vulnerabilities to Gain Initial Access for Future Attacks.
- In May 2021, these Iranian government-sponsored APT actors exploited a Fortigate appliance to access a webserver hosting the domain for a US municipal government. The actors likely created an account with the username elie to further enable malicious activity. Note: for previous FBI reporting on this activity, refer to FBI FLASH: APT Actors Exploiting Fortinet Vulnerabilities to Gain Initial Access for Malicious Activity.
- In June 2021, these APT actors exploited a Fortigate appliance to access environmental control networks associated with a U.S.-based hospital specializing in healthcare for children. The Iranian government-sponsored APT actors likely leveraged a server assigned to IP addresses 91.214.124[.]143 and 162.55.137[.]20—which FBI and CISA judge are associated with Iranian government cyber activity—to further enable malicious activity against the hospital's network. The APT actors accessed known user accounts at the hospital from IP address 154.16.192[.]70, which FBI and CISA judge is associated with government of Iran offensive cyber activity.
- As of October 2021, these APT actors have leveraged a Microsoft Exchange ProxyShell vulnerability—CVE-2021-34473—to gain initial access to systems in advance of follow-on operations.
The joint advisory, available on the CISA and ACSC sites, also includes details about the techniques and tools that the Iranian hackers used after compromising Fortinet and Exchange servers, tools they used to move across a network.
Iranian groups branching into ransomware
Similar to Microsoft's report yesterday, the joint advisory also mentions that in some instances, the Iranian groups also deployed ransomware inside some of the hacked networks. Multiple strains were used, including some that were developed in-house.
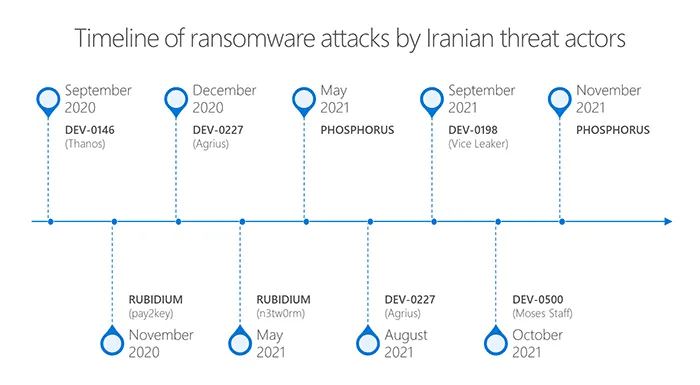
But the Microsoft report is more expansive than the joint FBI, CISA, NCSC, and ACSC alerts and focuses on explaining how six Iranian groups had evolved in recent years to become highly-sophisticated threats that can vary their techniques and possess a wide malware arsenal.
This includes the use of desktop and mobile malware, disk wipers, ransomware, sophisticated phishing techniques, brute-force and password-spraying attacks, some of the most sophisticated social engineering tricks today, and network exploitation.
Microsoft said that one of the biggest differences from previous years was that Iranian groups now exhibit more patience in their intrusions, some of which can take weeks until they reach their goal.
Furthermore, in some incidents, the cyberattacks supported physical operations, while in others, they supported espionage or information operations. This shows that the Iranian regime is learning from other countries that their cyber units can be used for more than just intelligence collection and tracking dissidents.
The Microsoft report, followed up by the joint US, UK, and Australia joint advisory, comes to show that while Iranian threat actors might not be as sophisticated as US, Israeli, Russian, or Chinese counterparts, they are slowly catching up.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



