US seizes two domains used by the SVR in recent hacking campaign
The US Department of Justice and the Federal Bureau of Investigation have seized two domains abused by Russian hacking group APT29 that have been used as part of a sprawling spear-phishing campaign that targeted government agencies, think tanks, consultants, and NGOs.
The attacks were discovered and detailed last week in a series of blog posts from Microsoft and security firm Volexity.
APT29, a hacking group which the White House formally linked to the Russian Foreign Intelligence Service (SRV) earlier this year and blamed for the SolarWinds supply chain attack, allegedly breached an account on email marketing platform Constant Contact that belonged to USAID, a US government agency that provides help to foreign governments and organizations.
Using this account, the SVR hackers sent around 3,000 booby-trapped emails to more than 150 organizations across 24 countries.
Upon a recipient clicking on a spear-phishing email's hyperlink, the victim computer was directed to download malware from a sub-domain of theyardservice[.]com. Using that initial foothold, the actors then downloaded the Cobalt Strike tool to maintain persistent presence and possibly deploy additional tools or malware to the victim's network. The actors' instance of the Cobalt Strike tool received C2 communications via other subdomains of theyardservice[.]com, as well as the domain worldhomeoutlet[.]com.
US Department of Justice
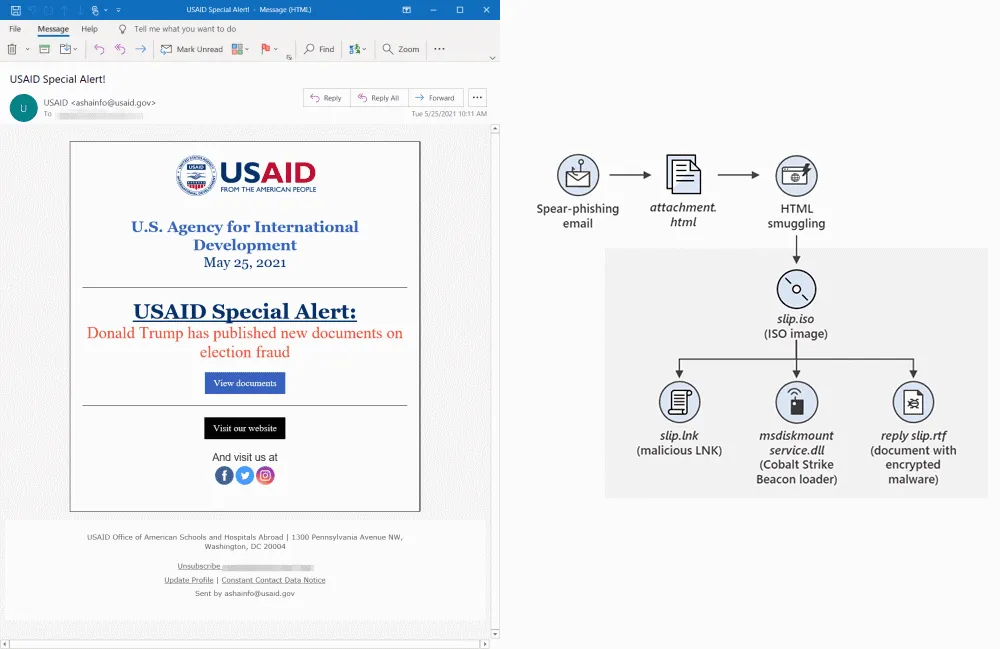
Now, the DOJ said it worked together with the FBI to obtain a court order and seize these two domains from SVR operators in order to block their ability to infect new systems or interact with previously infected hosts.
"The FBI remains committed to disrupting this type of malicious cyber activity targeting our federal agencies and the American public," said Assistant Director Bryan Vorndran of the FBI's Cyber Division.
"We will continue to use all of the tools in our toolbelt and leverage our domestic and international partnerships to not only disrupt this type of hacking activity but to impose risk and consequences upon our adversaries to combat these threats."
This is the second time when the FBI and the DOJ have intervened to seize domains used by Russian state hackers.
The first time was in May 2018 when they seized domains used to control the VPNFilter botnet, allegedly created by fellow Russian hacking group APT28 (linked to Russian military intelligence).
Besides US government agencies, Microsoft has also used court orders to seize domains used by Russian state hackers in their attacks, first in 2018 and then again this year.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



