US says Russian hackers breached multiple DOD contractors
The US government said today that Russian state-sponsored threat actors have targeted and breached multiple defense contractors between January 2020 and February 2022.
"Compromised entities have included CDCs [cleared defense contractors] supporting the US Army, US Air Force, US Navy, US Space Force, and DoD and Intelligence programs," US officials said in a joint security alert published today by the NSA, CISA, and the FBI.
"During this two-year period, these actors have maintained persistent access to multiple CDC networks, in some cases for at least six months," officials added.
In cases of successful compromises, the threat actors were seen collecting and exfiltrating emails and sensitive but unclassified data, such as proprietary and export-controlled information.
"For example, during a compromise in 2021, threat actors exfiltrated hundreds of documents related to the company's products, relationships with other countries, and internal personnel and legal matters," the three agencies explained.
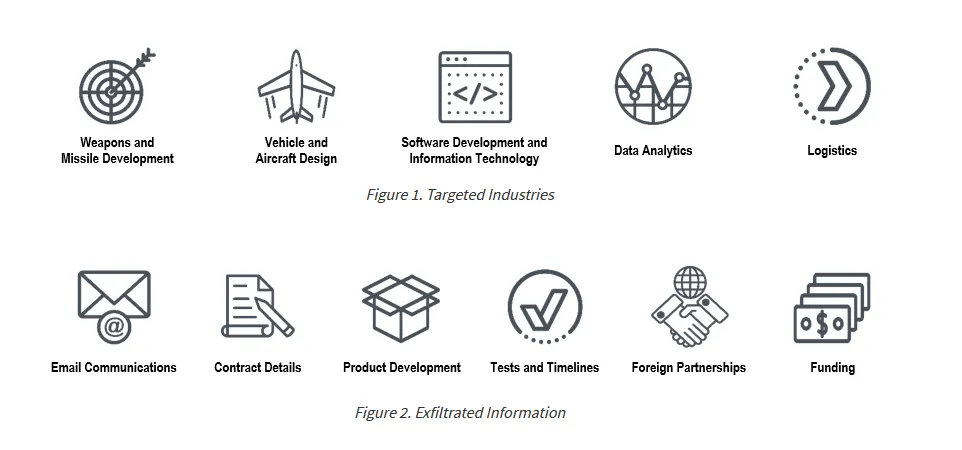
Officials said that the theft of this information has granted the attackers "significant insight into US weapons platforms development and deployment timelines, plans for communications infrastructure, and specific technologies employed by the US government and military."
The rest of the joint advisory contains technical details from some of the intrusions, which the agencies shared so other contractors and the private sector can use to shore up their IT security defenses.
The alert today comes after US officials published another joint alert last month, warning of cyberattacks on US companies if Russia attacks Ukraine.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



