US indicts four members of Chinese hacking group APT40
The US Department of Justice has unsealed charges today against four Chinese nationals for hacking companies, government agencies, and universities across the world on behalf of the Chinese government.
The US said the four suspects, believed to be part of a much larger group, set up a company named Hainan Xiandun Technology Development Co., Ltd. (海南仙盾) (Hainan Xiandun), which they used as a front for their hacking campaigns.
US investigators said the company operated under the direct supervision of the Hainan State Security Department (HSSD), the provincial arm of China's Ministry of State Security (MSS).
Using agents planted inside the company, the US alleges the MSS directed the group's hacking campaigns since at least 2011, selecting targets to breach and then steal proprietary and confidential business information that they would later disseminate inside China.
Four APT40 members charged today
US officials said Hainan Xiandun was responsible for hacks that the cybersecurity community has attributed to groups under different names, such as ATP40, BRONZE, MOHAWK, FEVERDREAM, G0065, Gadolinium, GreenCrash, Hellsing, Kryptonite Panda, Leviathan, Mudcarp, Periscope, Temp.Periscope and Temp.Jumper.
Of the four Chinese nationals indicted today, three were MSS officers working for the Hainan provincial department, DOJ officials said:
- Ding Xiaoyang (丁晓阳)
- Cheng Qingmin (程庆民)
- Zhu Yunmin (朱允敏)
A fourth suspect, named Wu Shurong (吴淑荣), worked as a hired hacker for the Hainan Xiandun front company, for which he created malware and then used it to hack into computer systems belonging to foreign governments, companies, and universities, at the behest of the three MSS supervisors. He allegedly operated under hacker nicknames such as "goodperson" and "ha0r3n."

DOJ officials said the group used both public and custom-made malware strains to carry out their intrusions.
This included malware strains such as BADFLICK, aka GreenCrash; PHOTO, aka Derusbi; MURKYTOP, aka mt.exe; and HOMEFRY, aka dp.dll.
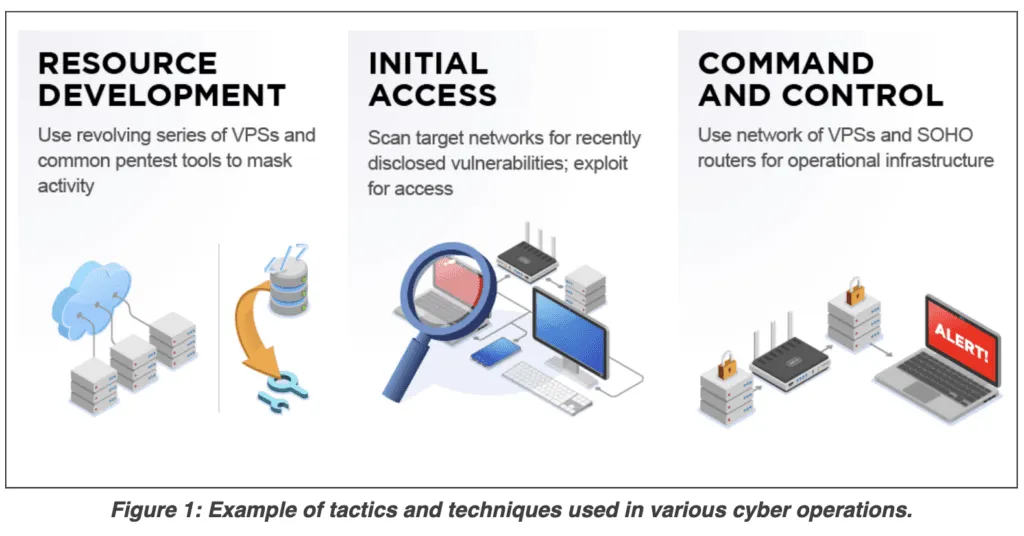
According to court documents [PDF], the group often used the Tor network to access and operate their malware and hacking infrastructure, which included servers, domains, email, GitHub, and Dropbox accounts.
The group would often use GitHub to both store malware and stolen data, with the latter being concealed using steganography, hiding stolen information in images that sometimes would portray US President Donald Trump.
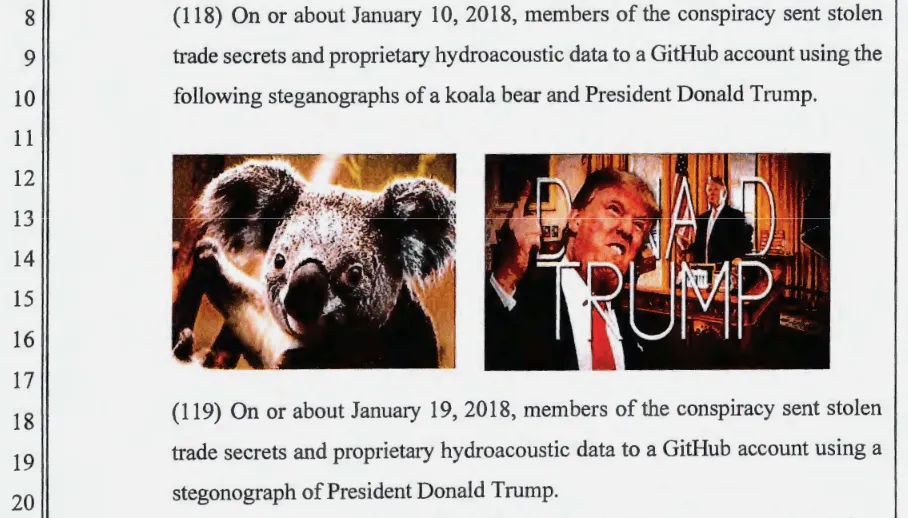
APT40 operators would also often abuse Dropbox accounts as collection points for stolen data, relying on the fact that most companies wouldn't see Dropbox traffic as malicious.
APT40 stole data to aid Chinese companies
The group was most active between 2011 and 2018. During that time, the DOJ said APT40 breached targets in the United States, Austria, Cambodia, Canada, Germany, Indonesia, Malaysia, Norway, Saudi Arabia, South Africa, Switzerland, and the United Kingdom.
Targeted industry sectors included aviation, defense, education, government, health care, biopharmaceutical, and maritime transport.
Stolen trade secrets and confidential business information included sensitive technologies used for submersibles and autonomous vehicles, specialty chemical formulas, commercial aircraft servicing, proprietary genetic-sequencing technology.
The DOJ said the data was often used to support China's efforts to secure contracts for state-owned enterprises within targeted countries, allowing Chinese companies to have better bids and get an edge on competitors in securing large contracts.
APT40 was also allegedly involved in stealing data from research institutes and universities, with the group often targeting infectious-disease research related to Ebola, MERS, HIV/AIDS, Marburg, and tularemia.
Furthermore, US investigators said APT40 worked closely with various universities in Hainan and across China. Using their Hainan Xiandun front company, the group collaborated with university staff to recruit hackers and linguistics from the universities' ranks to aid in future intrusions.
This collaboration went as far that "personnel at one identified Hainan-based university also helped support and manage Hainan Xiandun as a front company, including through payroll, benefits and a mailing address," the DOJ said today.
According to court documents, Ding, the main officer believed to be in charge of APT40 operations, even received an award from the MSS in May 2018 for the group's successful operations.

APT40 was doxed in January 2020
News of today's charges against APT40, MSS officer Ding Xiaoyang, and the MSS' Hainan provincial department is not a surprise.
The connections between the Hainan Xiandun front company, APT40 activity, Ding, and the Hainan MSS office were previously detailed in two reports from anonymous research group IntrusionTruth in January 2020.
This now marks the fourth time an IntrusionTruth report translates to DOJ charges. The group previously exposed details about the MSS' involvement in APT3 (believed to operate out of the Guangdong province), APT10 (Tianjin province), and APT17 (Jinan province).
The DOJ charges announced today also came as the US, the UK, the EU, and other western allies blamed the recent hacking campaign against Microsoft Exchange servers on Chinese state-sponsored hackers, naming APT31 and APT40 as two of the entities behind the Hafnium group. The DOJ indictment doesn't cover the Exchange hacks, but only APT40 operations between 2011, when the Hainan Xiandun front company was established, and up to 2018.
Following today White House announcement and DOJ charges, the NSA, CISA, and the FBI have also issued technical guidance on detecting APT40 intrusions and activity.
Article updated to point out that the DOJ charges do not cover APT40's attacks on Exchange servers that took place in late 2020 and early 2021, a hacking campaign for which they were internationally blamed by several governments.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



