US charges Iranian hackers for spoofed Proud Boys emails threatening US voters
The US Department of Justice has charged today two Iranian nationals of attempting to undermine and influence the 2020 US Presidential Election through a series of hacks and influence operations carried out between September and November 2020.
The two suspects, Seyyed Mohammad Hosein Musa Kazemi (24) and Sajjad Kashian (27) stand accused of a list of crimes, detailed below:
- Hacked the voter websites for 11 US states - In September and October 2020, members of the conspiracy conducted reconnaissance on, and attempted to compromise, approximately eleven state voter websites, including state voter registration websites and state voter information websites. Those efforts resulted in the successful exploitation of a misconfigured computer system of at least one US state, from where they stole information on more than 100,000 voters, including non-public data.
- Contacted Republican party members with fake videos of Democrats' election fraud - In October 2020, members of the conspiracy, claiming to be a "group of Proud Boys volunteers," sent Facebook messages and emails (the "False Election Messages") to Republican Senators, Republican members of Congress, individuals associated with the Presidential campaign of Donald J. Trump, White House advisors, and members of the media. The False Election Messages claimed that the Democratic Party was planning to exploit "serious security vulnerabilities" in state voter registration websites to "edit mail-in ballots or even register non-existent voters." The False Election Messages were accompanied by a video (the "False Election Video") carrying the Proud Boys logo, which purported, via simulated intrusions and the use of State-1 voter data, to depict an individual hacking into state voter websites and using stolen voter information to create fraudulent absentee ballots through the Federal Voting Assistance Program (FVAP) for military and overseas voters.
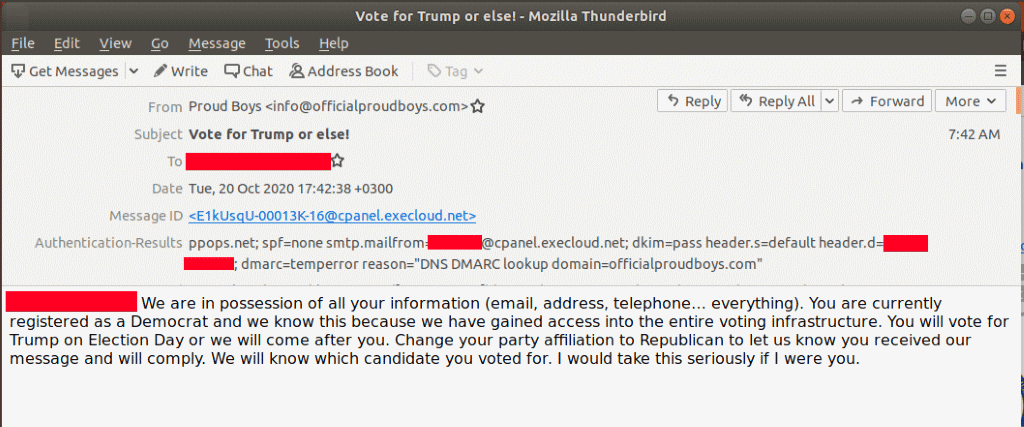
- Posed as right-wing group ProudBoys, and sent emails threatening Democrat voters to vote for Trump - Also, in October 2020, the conspirators engaged in an online voter intimidation campaign involving the dissemination of a threatening message (the "Voter Threat Emails"), purporting to be from the Proud Boys to tens of thousands of registered voters, including some voters whose information the conspiracy had obtained from State-1's website. The emails were sent to registered Democrats and threatened the recipients with physical injury if they did not change their party affiliation and vote for President Trump.
- Hacked a US media company - On November 4, 2020, the day after the 2020 US Presidential election, the conspirators sought to leverage earlier September and October 2020 intrusions into an American media company's (Media Company-1) computer networks. Specifically, on that day, the conspirators attempted to use stolen credentials to again access Media Company-1's network, which would have provided them another vehicle for further disseminating false claims concerning the election through conspirator-modified or created content. However, because of an earlier FBI victim notification, Media Company-1 had by that time mitigated the conspirators' unauthorized access, and these log-in attempts failed.
The suspects worked for an Iranian cybersecurity firm
According to court documents, the two suspects conducted their operations while they were employed by an Iranian cybersecurity firm named Eeleyanet Gostar (formerly Emennet Pasargad).
The DOJ said the company is a cybersecurity contractor for the Iranian government, which confirms statements made by Lab Dookhtegan, a hacktivist with a history of exposing Iranian cyber operations, and who has also mentioned Eelyeyanet Gostar in several leaks, according to Kaspersky security researcher Mark Lechtik.
As part of the US crackdown on this operation, the two suspects and their employers were also sanctioned by the US Treasury Department earlire today. These sanctions come after the US Treasury sanctioned four other Iranian entities last October for similar campaigns that tried to influence the result of the 2020 US Presidential Election.

The charges levied today are no surprise for industry observers as besides the attack on a US media network, most of the attacks detailed in the indictment today had been already known.
For example, the US Cybersecurity and Infrastructure Security Agency (CISA) sent out an alert about the group's attacks on US state voter sites last October, and US officials determined that an Iranian group was behind the Proud Boys email spam and fake video a day after the event happened.
Kazemi and Kashian are still at large, believed to be located in Iran. The two were also added to the FBI's cyber most wanted list, and the US State Department has offered a reward of up to $10 million for information about their whereabouts or which may lead to an arrest.

Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.