US charges former GRU officer with hacking and stock market trading scheme
The US Department of Justice has charged today five Russian nationals, including a former officer of Russia's GRU military intelligence agency, with hacking two SEC Filing Agents, stealing non-public information, and then sharing the stolen data with partners for the purpose of making beneficial trades ahead of time.
The five suspects were named as Vladislav Klyushin (41, Moscow), Ivan Yermakov (35, Moscow), Nikolai Rumiantcev (33, Moscow), Mikhail Vladimirovich Irzak (43, St. Petersburg), and Igor Sergeevich Sladkov (42, St. Petersburg).
This marks the third time Yermakov was charged in the US. While working for GRU, Yermakov was also charged in July 2018 with hacking the Democratic National Committee and interfering in the 2016 US Presidential Election, and again in October 2018 for hacking and leaking data from the World Anti-Doping Agency (WADA). He is believed to have been a member of a cyber-espionage group known as APT28 or Fancy Bear.
Suspects used an IT security company as a front
But in court documents filed today, the DOJ said that Yermakov left GRU and, since 2018, began working at M13, a Moscow-based IT company that provided IT penetration testing and "Advanced Persistent Threat (APT) emulation" services.
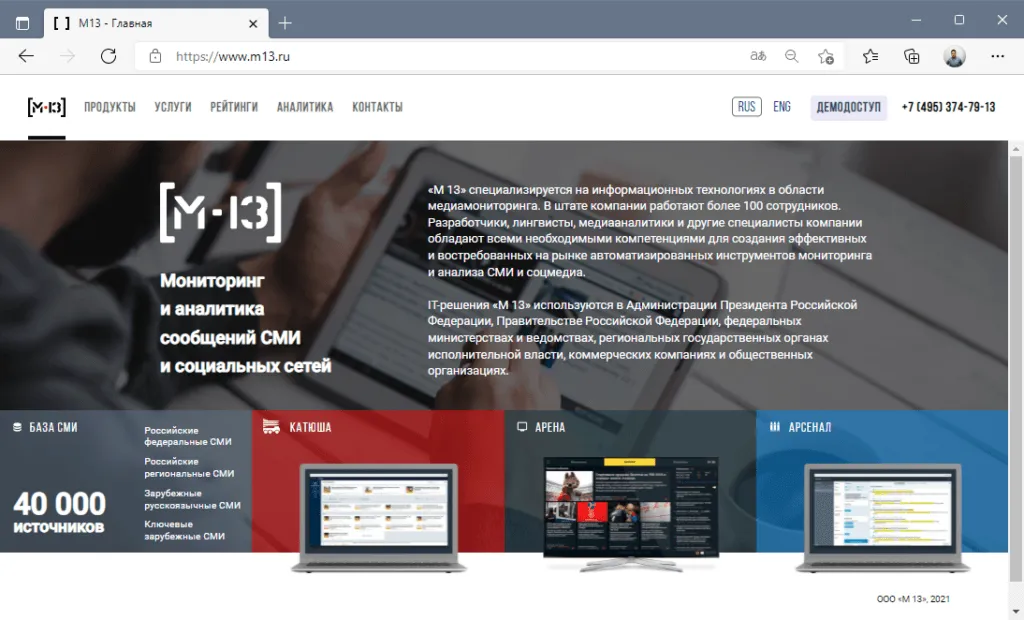
From behind the cover of this front company, US officials said that Yermakov, Rumiantcev, and Klyushin breached two US companies that operated as SEC filing agents and helped publicly-traded corporations prepare their quarterly and yearly reports that need to be filed with the US Securities and Exchange Commission.
Between January 2018 and September 2020, the DOJ said the five suspects phished employees at the two companies to gained access to their internal networks, from where they stole documents that the two filing agents were preparing for their customers.
To remain under the radar, the three used local proxies to make it look like they were connecting to the compromised networks from local IP addresses.
The DOJ said that during their attacks, Yermakov, Rumiantcev, and Klyushi stole documents for hundreds of companies listed on NASDAQ and the New York Stock Exchange, such as Tesla, IBM, Snap, Box, Kohl's, Datadog, Nanometrics, The Nielsen Company, SS&C Technologies, Capstead Mortgage, and Nevro Corp.
Suspects asked for 60% cut from any trading profits
They allegedly disseminated the stolen information to other investors through their M13 front company, which also provided investment management services, and asked for 60% of any profits the insider information would yield.
Irzak and Sladkov are accused of having helped the M13 trio make some of their market transactions, according to the DOJ. The group is suspected of having earned tens of millions of US dollars from their illegal trading.
Charges against the five were unsealed today after Klyushin was arrained in front of a US judge today after being extradided from Switzerland, where he was arrested in March this year.
The other four suspects remain at large, according to the DOJ, and Yermakov is still on the FBI's Cyber Most Wanted list as one of the most sought-after hackers today.
"Today's announcement and the extradition of Vladislav Klyushin is just one more example of how the FBI and our partners are working around the clock and around the world to counter the cyber threat that we face today," said Albert Murray III, Assistant Special Agent in Charge of the FBI Washington Field Office Criminal and Cyber Division.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.