Ukraine warns of 'massive' Russian spear-phishing campaign
Three Ukrainian cybersecurity agencies have warned last week of a "massive" spear-phishing operation carried out by Russian threat actors against the Ukrainian government and private sector.
The Ukrainian Secret Service, one of the three agencies, has attributed the attack to the "special services of the Russian Federation," marking the third cyberattack the agency has publicly attributed to Russian hackers this year.
Emails mimicked the Kyiv Patrol Police Department
The spear-phishing operation took place in early June last week, according to alerts published by the Ukrainian Secret Service, Ukrainian Cyber Police, and CERT Ukraine.
The attackers sent emails posing as representatives for the Kyiv Patrol Police Department, warning recipients of their failure to pay local taxes.
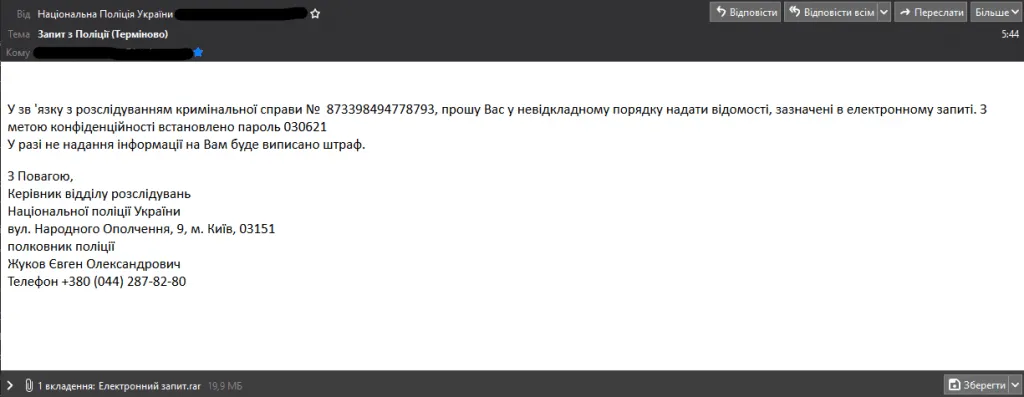
Recipients were urged to download a RAR archive included in the email, which, when decompressed, would drop an EXE file with a double extension (filename.pdf.exe) that tried to pass as a PDF file.
Victims who ran the malicious files would unwittingly install a modified version of a remote access software named RemoteUtilities that would ping back to remote command and control servers located in Russia, Germany, and the Netherlands.
"This allows the foreign intelligence service to remotely exercise full control over the PC," the Ukrainian Secret Service said on Friday.
Ukrainian officials have urged local organizations to scan their networks for indicators of compromise (IOCs) published on the Ukrainian Secret Service website and in a Facebook post by CERT Ukraine.
CERT officials also said that last week's campaign used tactics similar to past attacks that took place earlier this year in January and March.
A constant target for Russian cyber operations
Since 2014, when Russian forces invaded Eastern Ukraine, the former Soviet state has been under a constant barrage of cyberattacks that Ukrainian officials have regularly linked to the Kremlin.
But while the most widely known incidents include the NotPetya and Bad Rabbit ransomware outbreaks, and the attacks that shut down parts of the Ukraine power grid in 2015 and 2016, there have been hundreds of smaller attacks throughout the recent years.
Most are just like the one reported last week. They are short bursts of email spam executed with the hope of gaining a foothold inside Ukrainian organizations in order to collect intelligence.
But while spear-phishing operations have accounted for the bulk of attacks, Russian hackers also varied their tactics. For example, in February this year, Ukraine's National Security and Defense Council accused Russian state hackers of launching DDoS attacks against Ukrainian government websites.
A week later, they also said that a Russian hacking group known as Gamaredon compromised a government file-sharing system as part of an attempt to disseminate malicious documents to other government agencies through one of the Ukraine government's own internal systems.
In an interview with The Record earlier last year, Serhii Demediuk, Deputy Secretary of the country's National Security and Defense Council, discussed the difficulties in dealing with the constant cyberattacks from Russian special services, including their predisposition to sometimes use local hackers.
Of course, the law enforcement agencies of our country know that the listed hacker groups of the Russian special services have a spy network in the hacker environment of Ukraine. Most of these participants have been identified and are being monitored.
Serhii Demediuk, Deputy Secretary of the country's National Security and Defense Council
But in recent years, Ukraine has also been getting a helping hand from some of its allies, namely US intelligence agencies. According to a report, the collaboration between US and Ukrainian agencies has stopped at least 350 Russian cyber operations this year alone.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



