Ukraine discloses identity of Gamaredon members, links it to Russia's FSB
The Ukrainian Security Service (SSU) has revealed today the real identities of five members of the Gamaredon cyber-espionage group, linking its members to the Crimean branch of the Russian Federal Security Service (FSB).
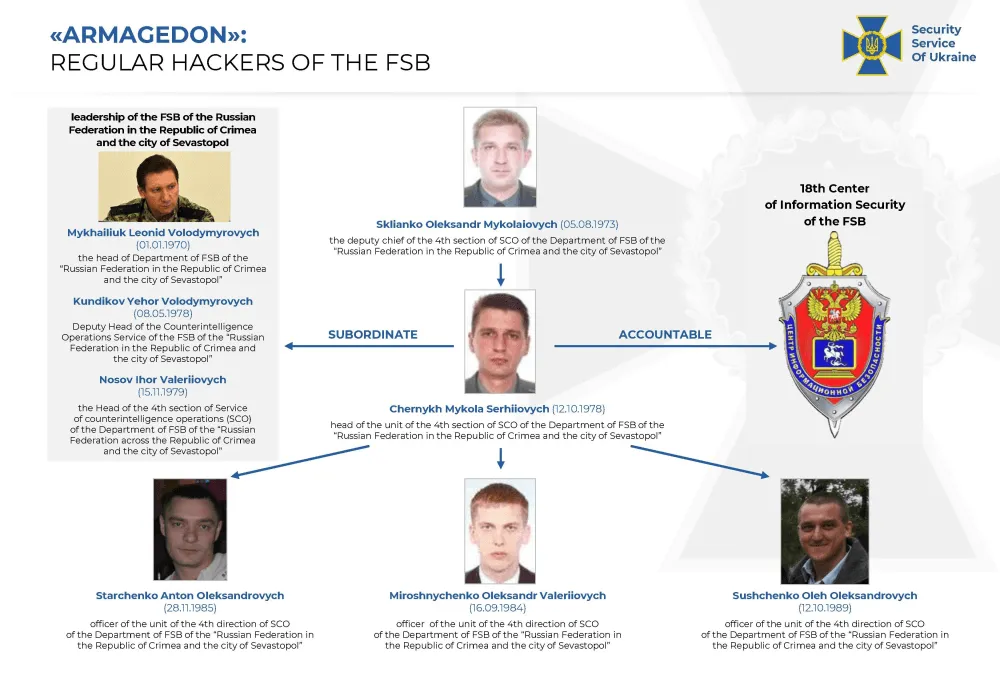
Officials said the group —which the SSU tracks internally as Armageddon but is more widely known in cybersecurity circles as Gamaredon— operated from the city of Sevastopol, Crimea, but acted on orders from the FSB Center for Information Security (also known as "Center 18") in Moscow, a known hub for the FSB's cyber operations.
Five members were identified by name and position and the SSU said it sent them "notices of high treason":
- Chernykh Mykola Serhiiovych (head of the 4th section of SCO of the FSB Sevastopol branch)
- Sklianko Oleksandr Mykolaiovych (deputy chief of the 4th section of SCO of the FSB Sevastopol branch)
- Starchenko Anton Oleksandrovych (officer of the 4th section of SCO of the FSB Sevastopol branch)
- Sushchenko Oleh Oleksandrovych (officer of the 4th section of SCO of the FSB Sevastopol branch)
- Miroshnychenko Oleksandr Valeriiovych (officer of the 4th section of SCO of the FSB Sevastopol branch)
"They were officers of the 'Crimean' FSB, as well as traitors who sided with the enemy during the occupation of the peninsula in 2014," the SSU said today in a press release.
To support parts of its claims, the SSU also published intercepted phone conversations between two of the Gamaredon members regarding attacks they were carrying out and complaints they had with their FSB salaries.
Although previous reports from multiple cyber-security companies have linked the group to a suspected Russian government entity, today's SSU press release marks the first time that the Gamaredon group has been linked to the FSB.
One of the most active groups targeting Ukraine
Known as Gamaredon (Eset, PaloAlto), Primitive Bear (CrowdStrike), Winterflouder (iDefence), BlueAlpha (RecordedFuture), BlueOtso (PWC), IronTiden (SecureWorks), SectorC08 (Red Alert), and Callisto (NATO Association of Canada), the group began operations in June 2013, just months before Russia forcibly annexed the Crimean Peninsula from Ukraine.
Since that time, the SSU says the group has carried out more than 5,000 cyberattacks against more than 1,500 Ukrainian government systems.
"The main purpose of its activity is to conduct targeted cyberintelligence operations against state bodies of Ukraine, primarily security, defense and law enforcement agencies, in order to obtain intelligence information," the SSU said in a 35-page technical report [PDF] that accompanied its press release.
The SSU report describes past Gamaredon attacks with terms such as "intrusiveness and audacity" and suggesting that the group had not been focused on staying "secret for a long time."
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



