As ransomware attacks surge, UK privacy regulator investigating fewer incidents than ever
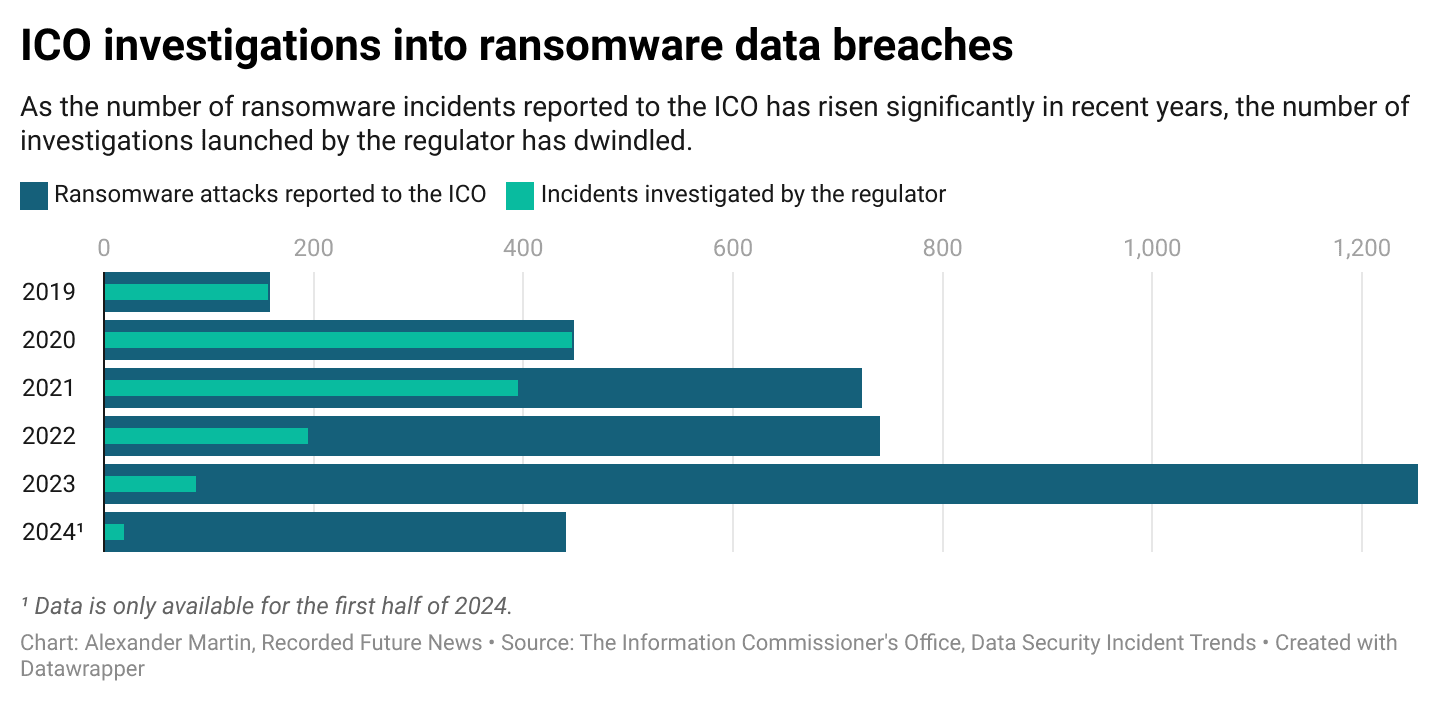
As ransomware data breaches reach record high levels across the United Kingdom, the number of incidents being investigated by the country’s data protection regulator is dwindling to record lows, raising questions about its capacity and approach to the problem.
Of the 1,253 incidents reported to the Information Commissioner’s Office (ICO) last year, only 87 were investigated — fewer than 7% — and just 19 of the 440 incidents reported in the first half of this year have been subjected to an investigation, fewer than 5%.
Those numbers stand in contrast to data published for 2019 and 2020, when the privacy watchdog investigated more than 99% of the 605 ransomware incidents, probing all but three cases.
Alongside the ICO’s duties, the significant increase in ransomware attacks since the publication of the National Cyber Strategy in 2022 brings into question whether the government is effectively protecting organizations and individuals in Britain.
Part of the role of the ICO is to enforce British data protection laws, which require organizations to protect people’s personal information using reasonable security measures. Its enforcement investigations into whether these measures were in place can take years to complete. In just the past few months the ICO reprimanded Hackney Council in London for failing to prevent an attack that occurred in 2020, and fined the NHS software supplier Advanced for a similar incident in 2022.
A spokesperson for the regulator said its work increasing the “awareness of the link between cyber attacks and personal data breaches” was “driving organisations to improve their practices,” but the growing number of reported attacks affecting millions of people in Britain does not suggest practices are improving.
Asked about the drop in investigations and whether the ICO’s capacity to investigate these data breaches had shrunk since 2020, a spokesperson said: “The ICO regulates the whole UK economy, and so we continuously review and make difficult choices about how we prioritise our resources.”
They added it was the ICO’s “duty to ensure we use our powers to have the maximum possible positive impact for the public and provide regulatory certainty to organisations. We have a robust triage process for each and every report we receive to determine which should progress to a formal investigation and those where other courses of action may be more appropriate.”
For cyber incidents, this triage process involves considering the breach’s impact on the confidentiality, integrity and availability of personal data and the risks to the public. The ICO will also consider focusing on cases that might have the greatest impact, or on the initial source of a supply-chain breach rather than each subsequent victim.
“Not every case progresses to a formal investigation, but it is important to note that investigations and enforcement are not the only ways the ICO has impact,” said the spokesperson.
“We regulate proactively as well as reactively, providing advice and guidance to controllers (such as our recent Learning from the Mistakes of Others report) and engaging with industry and partners including NCSC to support and prompt good cyber practice.”
The British government has pledged to introduce a new Cyber Security and Resilience Bill to parliament next year to address the growing disruption caused by cyberattacks. As the government describes the bill, it will expand existing laws to cover more digital services and supply chains and increase mandatory incident reporting.
The legislation as described falls short of more ambitious plans that were to be proposed in a Home Office public consultation, as reported by Recorded Future News, before the consultation was ultimately scuppered by Rishi Sunak’s snap election.
That proposed major overhaul of how the country responds to ransomware attacks would have required all ransomware victims to report incidents to the government, and then obliged those victims to seek a license from sanctions authorities before making any extortion payments.
It also would have prohibited companies working in critical infrastructure from ever making an extortion payment, intending to remove the incentive for hackers to disrupt these critical services by preventing them from monetizing attacks.
Recorded Future News’ sources suggest the consultation will be launched before the bill is introduced to Parliament.
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79



