Turkish malware used to infect machines in 11 countries through fake Google Translate links
Turkish-speaking hackers are spreading crypto-mining malware through free software download sites, including one offering a fake Google Translate desktop app, according to new research.
Cybersecurity firm Check Point on Monday said it discovered the campaign at the end of July and named it Nitrokod. The researchers said it may have infected thousands of devices with malware across 11 countries.
Maya Horowitz, vice president of research at Check Point, said her team found a popular website offering imitations of PC applications, including Google Desktop, which include a cryptocurrency miner. The malware hijacks a device's processor and forces it to verify transactions of currency like Bitcoin.
“The malicious tools can be used by anyone. They can be found by a simple web search, downloaded from a link, and installation is a simple double-click. We know that the tools are built by a Turkish-speaking developer,” Horowitz said. “Currently, the threat we identified was unknowingly installing a cryptocurrency miner, which steals computer resources and leverages them for the attacker to monetize on.”
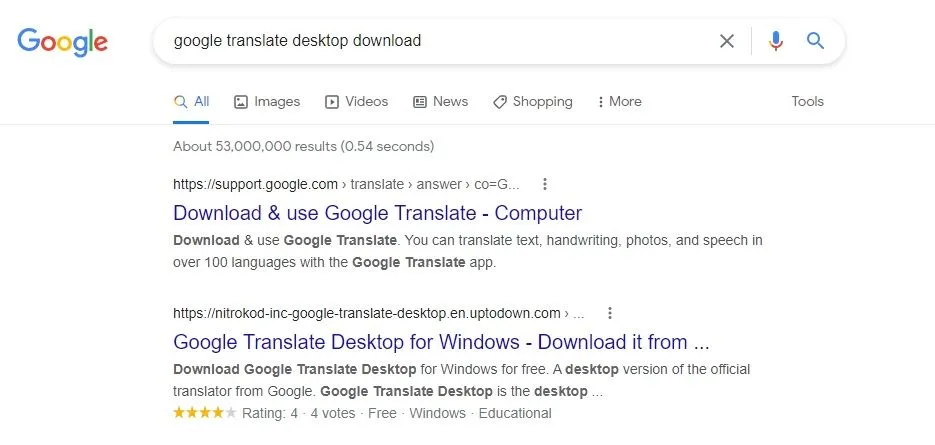
As Horowitz explained, one of the links that leads to a download of the malware is easily found through Google when users search “Google Translate Desktop download.”
The programs have a delayed mechanism that deploys the malware after several days or weeks while also deleting any trace of the original installation, which “allowed the campaign to successfully operate under the radar for years,” the report said.
“The malware is first executed almost a month after the Nitrokod program was installed," researchers wrote. "The infection chain continued after a long delay using a scheduled task mechanism, giving the attackers time to clear the evidence.”
Once the malware is finally downloaded, it connects to a command and control server and starts mining for cryptocurrency.
Horowitz added that the perpetrator can easily choose to alter the final payload of the attack, changing it from a crypto-miner to, say, a ransomware or banking Trojan.
According to Check Point, the software developer Nitrokod has been active since 2019, offering popular applications that do not have official desktop versions. Many of Nitrokod's programs can be found on free software sites like Softpedia and Uptodown.
One of the most popular programs on Nitrokod is the Google Translate desktop application. Google has never released a desktop application for Google Translate, which makes the corrupted Nitrokod version one of the first links that shows up.
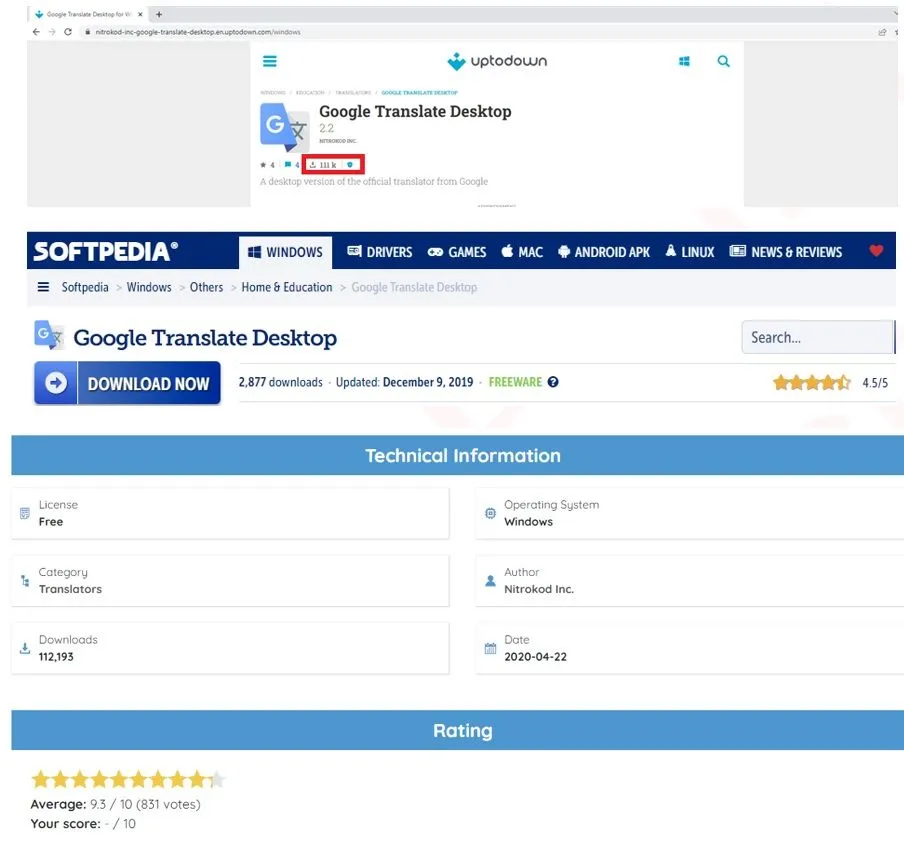
Check Point discovered that most of the programs on the platform are easily created using a Chromium-based tool that allows an application to be built directly from a web page, like Google Translate, thus saving Nitrokod authors from devoting time on building functional programs.
Some of the programs have been downloaded more than 100,000 times.
“What’s most interesting to me is the fact that the malicious software is so popular, yet went under the radar for so long,” she said. “We blocked the threat for Check Point customers, and are publishing this report so that others can be protected as well.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



