Semiconductor giant says IT supplier was attacked; LockBit makes related claims
The multibillion-dollar Taiwan Semiconductor Manufacturing Company (TSMC) said one of its IT hardware suppliers experienced a security incident that caused the leak of information.
TSMC made the statement after the LockBit ransomware group claimed it attacked the company in a posting on its leak site on Thursday.
A company spokesperson would not specifically address the LockBit posting but said the company recently became aware that one of its suppliers, a firm called Kinmax, was attacked, causing the “leak of information pertinent to server initial setup and configuration.”
TSMC is considered the world’s most valuable semiconductor company with a 2021 annual revenue of more than $57 billion.
“Upon review, this incident has not affected TSMC’s business operations, nor did it compromise any TSMC’s customer information,” the spokesperson said. “After the incident, TSMC has immediately terminated its data exchange with this concerned supplier in accordance with the Company’s security protocols and standard operating procedures.”
The company told Recorded Future News that the incident is currently “under investigation that involves a law enforcement agency.”
TSMC attached a letter to its statement from Kinmax that confirmed it was dealing with a cyberattack that began on the morning of June 29. Kinmax provides networking, cloud computing, storage, security and database management services. Like TSMC, the company is based in Hsinchu, Taiwan.
Kinmax officials said they discovered that their “internal specific testing environment was attacked, and some information was leaked.”
“The leaked content mainly consisted of system installation preparation that the Company provided to our customers as default configurations,” Kinmax said.
“We would like to express our sincere apologies to the affected customers, as the leaked information contained their names which may have caused some inconvenience. The company has thoroughly investigated this incident and implemented enhanced security measures to prevent such incidents from occurring in the future.”
TSMC said all further questions should be directed to a Kinmax spokesperson, who did not respond to requests for comment about whether the attack was launched by the LockBit ransomware group.
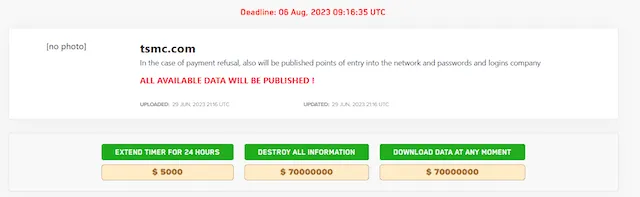
The LockBit posting drew the concern of cybersecurity researchers because the gang issued a $70 million ransom demand — one of the highest ransom demands ever issued by cybercriminals.
Researchers from the cybercrime-tracking site vx-underground said the attack was launched by the National Hazard Agency — a sub-clique of the LockBit ransomware group.
The group shared photos of some data stolen, including information on a VMware ESXI screen and more.
LockBit continues to be the most prolific ransomware group operating, accounting for one in every six ransomware attacks during 2022, according to the U.S. Cybersecurity and Infrastructure Security Agency and FBI.
The agencies said LockBit has claimed responsibility for at least 1,653 ransomware attacks, based on victims posted to its leak site, and brought in at least $91 million in ransoms from U.S. victims since its first reported attack in the country in January 2020.
TSMC noted in its statement that its customer should not be concerned about the attack, explaining that “every hardware component undergoes a series of extensive checks and adjustments, including security configurations, before being installed into TSMC’s system.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



