No evidence of malicious access, Toyota says about serious bug exploited by outside researcher
Toyota says it has fixed a vulnerability discovered by an outsider that allowed for widespread access to a platform used by employees to coordinate operations.
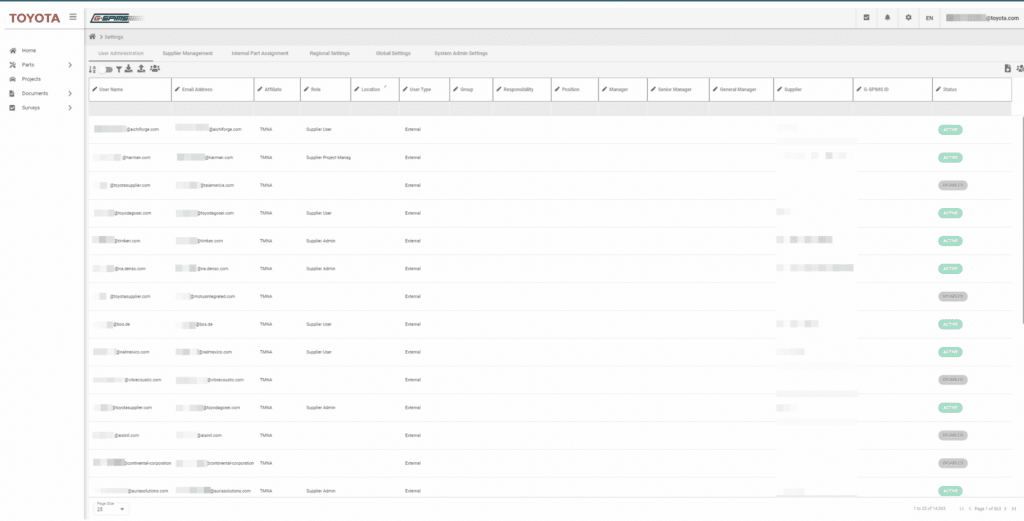
Security researcher Eaton Zveare published a blog post Monday explaining how he managed to gain full control of the web app, called the Global Supplier Preparation Information Management System (GSPIMS), in October 2022. The platform is used to coordinate projects, parts, surveys, purchases and more.
“We promptly remediated the reported vulnerability and confirmed that there was no evidence of malicious access to Toyota systems," a company spokesperson said in a statement to The Record. They referred other researchers "interested in partnering with Toyota" to its coordinated disclosure program at hackerone.com/toyota.
Zveare said he was able to take advantage of a poorly secured application programming interface (API) to break into the system. He submitted several reports to Toyota about vulnerabilities he had found but said the issue with GSPIMS was the most concerning.
“One of the reports had a remarkably severe impact and is one of the most severe vulnerabilities I have ever found (so far!) I discovered what was essentially a backdoor login mechanism in the Toyota GSPIMS website/application that allowed me to log in as any corporate Toyota user or supplier just by knowing their email,” he wrote.
Zveare said he "uncovered" a system administrator email and was able to log in to their account, which gave him full control over the "global system."
“I used the word ‘staggering’ to describe the amount of data I had access to in the Jacuzzi SmartTub hack, but that was relatively minor compared to this," he said, referring to a previous vulnerability he publicized. "I had full access to internal Toyota projects, documents, and user accounts, including user accounts of Toyota’s external partners/suppliers.”
Zveare said he had access to a directory of more than 14,000 users, as well as account details, confidential documents, projects, supplier rankings/comments, and more.
His access also spanned all of Toyota’s systems worldwide. He reported the issue to Toyota in November and it was fixed quickly.
The Toyota spokesperson confirmed that Zveare contacted the company about the issue.
“Toyota takes cyber threats very seriously. We regularly test our systems and also run a coordinated disclosure program to allow security researchers to report vulnerabilities. We appreciate the research performed by Eaton,” the spokesperson said.
In his blog post on the vulnerabilities, Zveare provided evidence of widespread access, sharing screenshots of internal systems, users, and more.
While much of his post was tongue-in-cheek, he went on to explain that if a malicious threat actor had discovered the same issue, the “consequences could have been severe.”
Someone could have added their own user account and retained perpetual access without ever being discovered. They could have downloaded and leaked all of the available data or simply deleted everything.
The access allowed for data to be modified in a way that would have disrupted Toyota’s operations globally. A phishing campaign could have been concocted to capture other corporate login details that would expose Toyota to other attacks.
“It’s one thing to have 14,000+ corporate emails, but it’s another to have 14,000+ corporate emails and know exactly what they are working on/have worked on,” Zveare said. “If a supplier user has a habit of reusing passwords, it’s possible their own infrastructure could be attacked too.”
By November 23, less than three weeks after being notified, Toyota had remediated the vulnerability. Zveare lauded the company for having the “fastest and most effective” response to security issues he’s reported.
Toyota factories were crippled last year by a cyberattack on a supplier in Japan, and another researcher last month found vulnerabilities in their cars that would have given hackers access to some of their vehicle’s systems.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



