Thousands of Tor exit nodes attacked cryptocurrency users over the past year
For more than 16 months, a threat actor has been seen adding malicious servers to the Tor network in order to intercept traffic and perform SSL stripping attacks on users accessing cryptocurrency-related sites.
The attacks, which began in January 2020, consisted of adding servers to the Tor network and marking them as "exit relays," which are the servers through which traffic leaves the Tor network to re-enter the public internet after being anonymized.
But since January 2020, a threat actor has been inserting thousands of malicious servers into the Tor network to identify traffic heading to cryptocurrency mixing websites and perform an SSL stripping attack, which is when traffic is downgraded from an encrypted HTTPS connection to plaintext HTTP.
The belief is that the attacker has been downgrading traffic to HTTP in order to replace cryptocurrency addresses with their own and hijack transactions for their own profit.
The attacks are not new and were first documented and exposed last year, in August, by a security researcher and Tor node operator known as Nusenu.
At the time, the researcher said the attacker managed to flood the Tor network with malicious Tor exit relays on three occasions, peaking their attack infrastructure at around 23% of the entire Tor network's exit capacity before being shut down by the Tor team on every occasion.
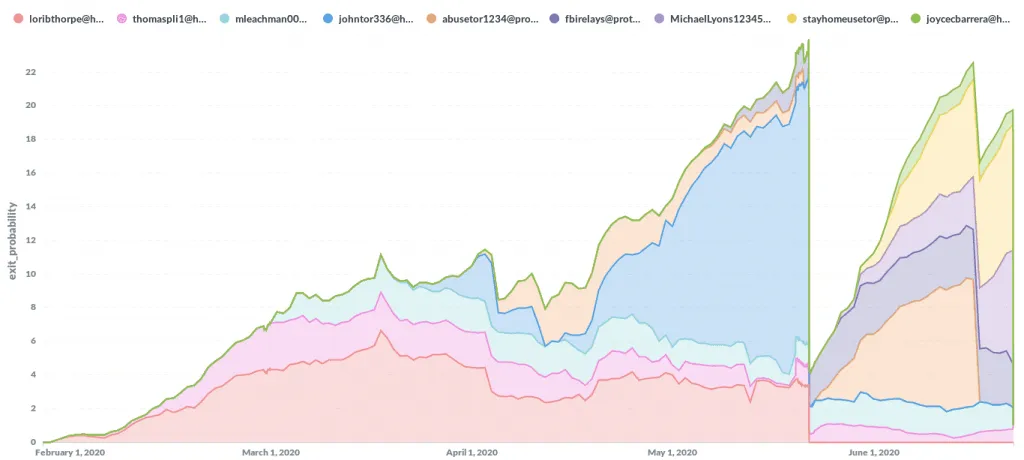
But in new research published today and shared with The Record, Nusenu said that despite having their operations publicly exposed, the threat actor continued their attacks, which are still ongoing.
Nusenu said the attacks even reached and surpassed a quarter of the Tor network's entire exit capacity on two occasions earlier in 2021, peaking at 27% in February 2021.
The second wave of attacks were all detected, just like the first, and the malicious Tor exit relays were removed from the Tor network, but not before the attack infrastructure was alive and intercepting Tor traffic for weeks or months.
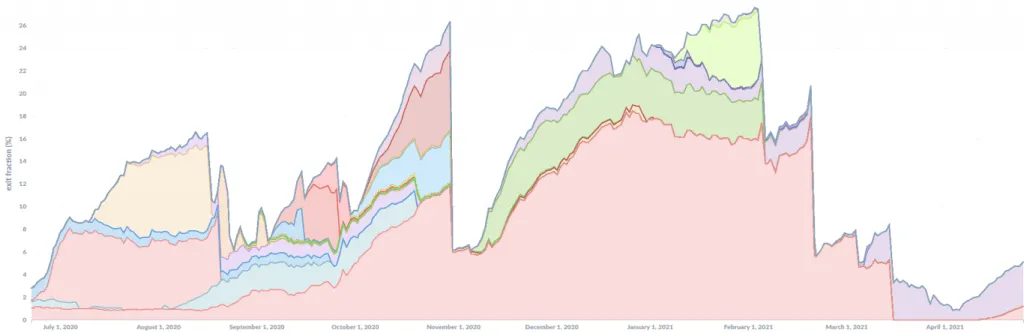
The primary reason the attacks worked for more than a year was because the threat actor added malicious exit relays in small increments, passing under the radar, and amassing infrastructure with time.
But the threat actor diverted from this tactic earlier this month when, most likely out of frustration that their infrastructure was taken down again, they attempted to bring back all servers online at the same time.
This most recent attack was spotted within a day after it increased the Tor network's exit capacity from around its daily 1,500 exit relays to more than 2,500, a spike that nobody could ignore inside the Tor Project.
But despite having more than 1,000 servers taken down, Nusenu also said that as of May 5, 2021, the attacker is still controlling between 4% and 6% of the entire Tor network's exit capacity, with SSL stripping attacks still ongoing.
Furthermore, Nusenu said that since last year, the attacker also appears to be engaging in download modifications after performing the SSL strip attacks, although it is unclear what exactly they're tampering with or if the attacker is using other techniques.
Back in August 2020, the Tor Project issued a series of recommendations on how website operations and Tor Browser users could protect themselves against these types of attacks. Users who use the Tor browser to access cryptocurrency or other financial sites are advised to follow the advice given there.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.