Thousands of Chrome extensions are tampering with security headers
Thousands of Google Chrome extensions available on the official Chrome Web Store are tampering with security headers on popular websites, putting users at risk of a wide range of web-based attacks.
While they are a little-known technical detail, security headers are an important part of the current internet landscape.
At a technical level, a security header is an HTTP response sent by the server to a client app, such as a browser.
Whenever a user accesses a website, the browser makes a request to a server, which then delivers the website. While the websites per-se are displayed through HTML, JavaScript, and CSS code, website administrators can add additional settings in the HTTP connection header to instruct the user's browser to treat the delivered content in a certain way.
Security headers are a type of HTTP response that have been created across the years by internet standards groups to allow website administrators to activate and customize security features inside the user's browser or other client applications.
Some of the most common security headers in use today are typically employed by website operators to make sure that their site works via an encrypted HTTPS connection, that users are protected from cross-site scripting attacks, or that code running inside iframes can't steal their browser data.
Study of the Chrome Web Store ecosystem
Although not all websites use security headers, many of today's top-tier web services usually employ them to secure their users against attacks, as due to their larger size, they usually tend to see more web-based attacks than regular sites.
However, while website administrators configure their security headers, this does not mean the security headers are still in place on the client side, where they can be intercepted and disabled by attackers performing a man-in-the-middle attack, malware running on an operating system, or by browser extensions.
But while the first two categories are obvious attack vectors and malicious in nature, the third one is not that simple to describe, as while some extensions might be malicious, other extensions may be disabling security headers for more benign reasons, such as to enable a certain functionality blocked by the header or by mistake.
In a paper presented at the MADWeb workshop at the NDSS 2021 security conference, researchers from the CISPA Helmholtz Center for Information Security said they tried to assess the number of Chrome extensions tampering with security headers for the very first time.
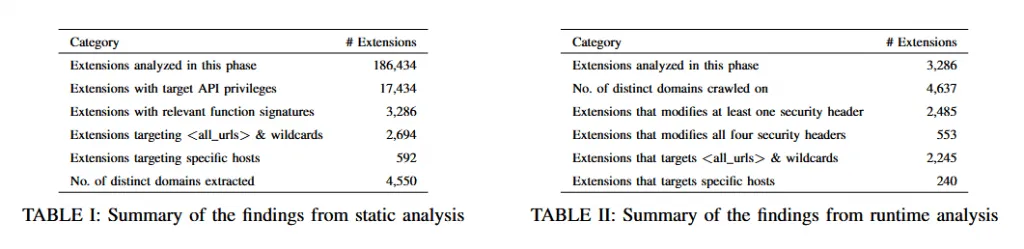
Using a custom framework they built specifically for their study, the research team said they analyzed 186,434 Chrome extensions that were available on the official Chrome Web Store last year.
2,485 Chrome extensions disabled at least one security header
Their work found that 2,485 extensions were intercepting and modifying at least one security header used by today's Top 100 most popular websites (as available in the Tranco list).
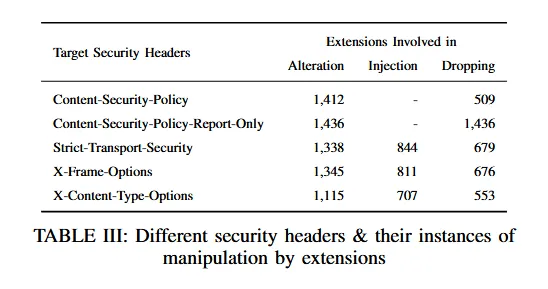
The study didn't focus on all security headers, but only on the four most common ones, such as: Content-Security Policy (CSP), HTTP Strict-Transport-Security (HSTS), X-Frame-Options, and X-Content-Type-Options.
While 2,485 extensions disabled at least one, researchers said they found 553 disabling all the four security headers they analyzed in their research.
The most commonly disabled security header was CSP, a security header that was developed to allow site owners to control what web resources a page is allowed to load inside a browser and a typical defense that can protect websites and browsers against XSS and data injection attacks.
According to the research team, in most of the cases they analyzed, the Chrome extensions disabled CSP and other security headers "to introduce additional seemingly benign functionalities on the visited webpage," and didn't look to be malicious in nature.
However, even if the extensions wanted to enrich a user's experience online, the German academics argued that by tampering with security headers, all the extensions did was to expose users to attacks from other scripts and sites running inside the browser and on the web.
Additional details can be found in a research paper titled "First, Do No Harm: Studying the manipulation of security headers in browser extensions," available here [PDF].
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.