TeamTNT botnet makes 50,000 victims over the last three months
TeamTNT, a crypto-mining botnet specialized in infecting misconfigured Docker and Kubernetes platforms, has compromised more than 50,000 systems over the last three months, between March and May 2021, security firm Trend Micro said last week.
The huge spike in attacks shows the evolution and growth the botnet has been going through in recent months.
First spotted last summer, TeamTNT is one of today's most advanced and most persistent threats to cloud environments.
The botnet works by infecting Docker and Kubernetes clusters that have accidentally exposed admin or management API interfaces online.
The malware takes over exposed systems and deploys server images that include a high-powered cryptocurrency mining script that generates profits for the attackers while exhausting computing resources and creating server costs for the victim.
But TeamTNT also comes with a worm component that converts every infected server into a node in its botnet and instructs it to scan for other Docker and Kubernetes systems on the internet it can infect.
In addition, the botnet creators also innovated last year when they were the first to add a feature that scanned infected systems for AWS (Amazon Web Services) credentials so the malware can also pivot to a company's other cloud resources and spread its malware there too.
This feature, spotted by Cado Security last year, was expanded over the winter to also target Docker and SSH credentials. In addition, a DDoS feature was also added, albeit it has not been seen abused until now.
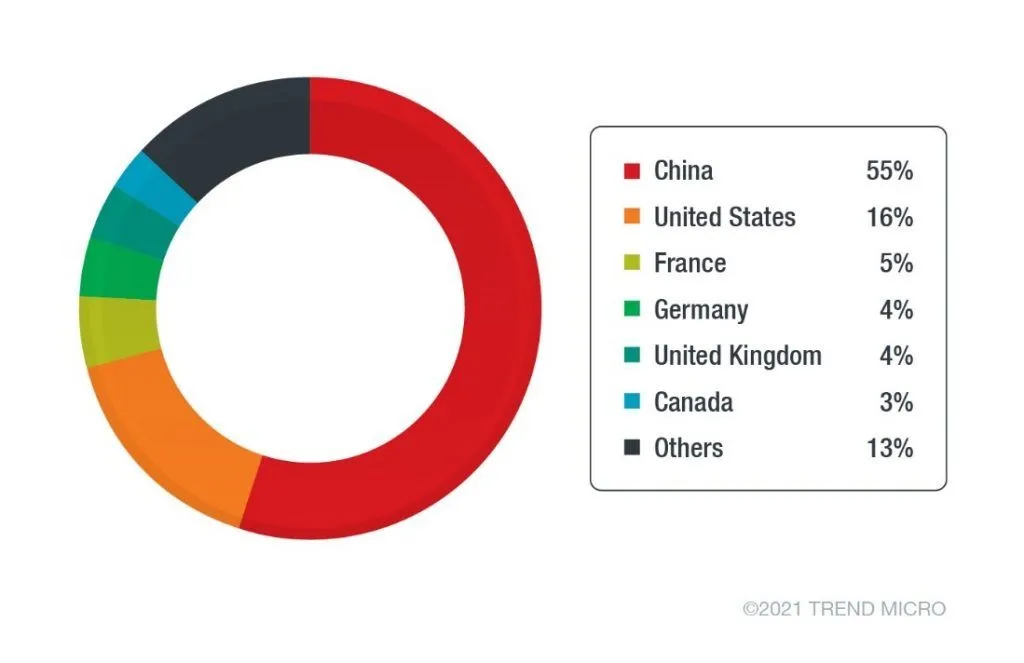
Most hacked systems are in China
The sudden spike in infected hosts observed by Trend Micro confirms that the features added in 2020 and earlier this year are paying dividends for the attackers.
Most of the recent 50,000+ victims are systems stored at Chinese cloud providers, which is the same victim pool distribution that Lacework reported earlier this year in January.
Trend Micro researchers Magno Logan and David Fiser said they expect the botnet to continue to expand going further.
Last year, Cado Security co-founder Chris Doman said attacks like TeamTNT are indicative of a wider trend.
"As organisations migrate their computing resources to cloud and container environments, we are seeing attackers following them there," Doman said.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.