Crafty PDF link is part of another tax-season malware campaign
Accounting firms appear to be the prime target of a malware campaign that mixes some familiar moves with a less common exploit involving a manipulated file shortcut, cybersecurity researchers said Thursday.
At least two customers of cybersecurity company Sophos reported the attacks earlier this year as the U.S. accounting industry was ramping up for tax season. Tax Day is April 18.
The campaign’s goal is to trick recipients of an email into clicking on a Windows shortcut that ultimately causes a download of malware called GuLoader, which can allow malicious hackers to send more malware — such as banking trojans or ransomware — to infected computers.
The overall process involves some social engineering: Attackers send what looks like a highly credible email to a firm, soliciting its business. If a recipient responds, they’re sent another email that links to a zip file.
“Because the attacker only sends the link to a CPA who responds to the initial email message, very few of them were caught in spam traps,” writes Sophos’ Andrew Brandt. “The samples we obtained had been submitted to us only after the targets realized they were being attacked.”
What’s inside the zip file is the interesting part, Sophos says. There are dummy files that Windows won’t open, essentially forcing the recipient — if they’ve gotten this far — to click on what appears to be a shortcut to a PDF.
The shortcut actually delivers the malware, but it hides its intentions through a little trick in the associated Properties fields that pop up when you right-click a file icon.
“The attackers have crafted the shortcut, by prepending a large number of space characters to the Target field in the properties, so that the Target field appears blank,” Brandt writes, noting that the exploit was first publicly disclosed last year by a researcher at U.K. cybersecurity company MDSec known as x86matthew.
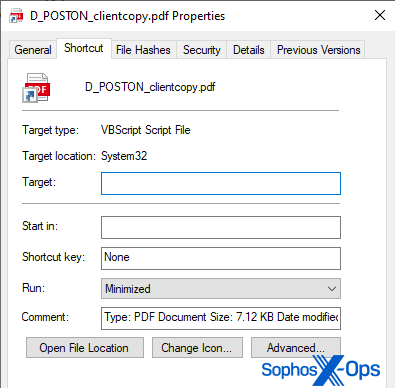 Image: Sophos
Image: Sophos
Once initiated, the shortcut downloads an actual PDF — it’s a decoy intended for human consumption — along with a malicious Virtual Basic script (VBS) that serves as the first stage for the GuLoader infection. Sophos says it was able to investigate the related servers.
“We found 29 different varieties of the VBS and 90 other encrypted and unencrypted payloads hosted in these locations,” Sophos says. “There may be others.”
Sophos also notes that the PDF shortcut itself “doesn’t resemble the icon used by any known PDF reader application.”
The social-engineering part of the campaign is similar to others reported this tax season. Cybersecurity company Securonix warned earlier this month about emails from a group known as “Tactical Octopus” that included zip files and decoy PDFs.
Researchers have tracked GuLoader malware for several years. Symantec reported on a campaign in 2022 that used it to target French-speaking countries in Africa.
Joe Warminsky
is the news editor for Recorded Future News. He has three decades of experience as an editor and writer in the Washington, D.C., area. He previously he helped lead CyberScoop for more than five years. Prior to that, he was a digital editor at WAMU 88.5, the NPR affiliate in Washington, and he spent more than a decade editing coverage of Congress for CQ Roll Call.



