Target open-sources its web skimmer detector
Target's cybersecurity team has open-sourced the code of Merry Maker, the company's internal application that it has used since 2018 to detect if any of its own websites have been compromised with malicious code that can steal payment card details from buyers.
"Since its launch in 2018, Merry Maker has completed over one million website scans, and we've filed multiple patent applications," the Target security team said in a blog post this week.
"The technology was launched right before Thanksgiving in 2018 and we nicknamed it for its ability to help keep the holiday shopping season — and all shopping occasions — safer and merrier," Target said about the tool's peculiar name.
Under the hood, the tool was developed to access an e-commerce portal and behave like a real user. It can access product pages, search listings, add items to the cart, and enter payment details in the checkout form.
But Merry Maker also inspects how the website behaves and reacts to all these actions and runs a continuous analysis of any code the website is loading and executing, even in real-time.
This code is checked against lists of existing IOC and YARA rules for known threats, such as domain names, IP addresses, and JavaScript files that have been used in past web skimmer attacks.
If any threat is detected, Merry Maker will raise an alert in a web-based dashboard, and security teams can move to inspect any possible compromises.
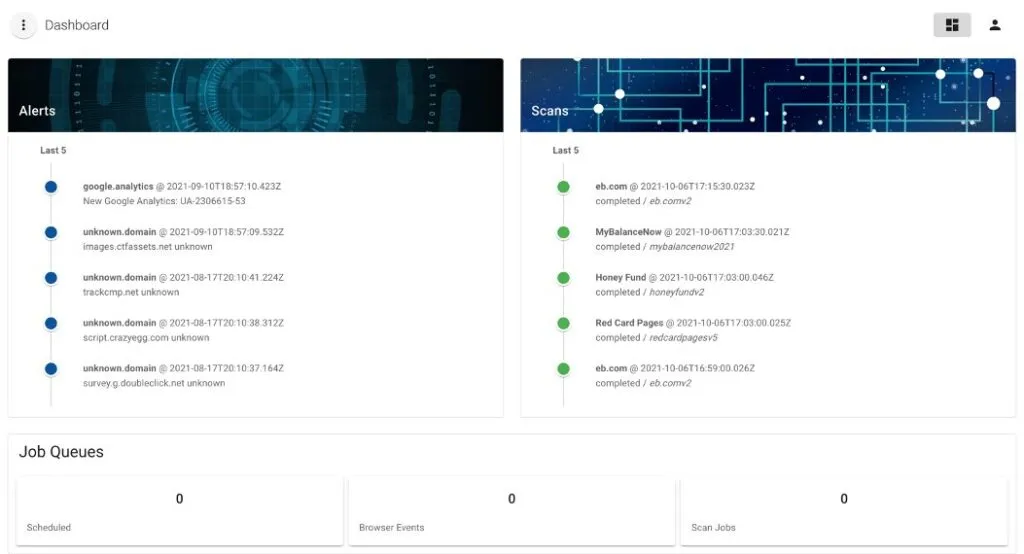
Target's Merry Maker tool is available on the company's GitHub account.
The tool is recommended for the owners of online stores who want to protect their e-commerce platforms against attacks known as Magecart, web-skimmers, or e-skimmers.
These types of attacks have first been seen in 2016 and have become more sophisticated each year. While initially, anyone would have been able to detect Magecart attacks just by looking at a site's source code using their browser, nowadays, malicious code is often hidden and only executes in certain conditions, requiring advanced HTML and JavaScript knowledge and specialized tools to detect.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



