Sysrv: A new crypto-mining botnet is silently growing in the shadows
If you forget to update or properly secure an internet-connected server or web app, the chances are that a crypto-mining botnet will infect it first, long before any nation-state hacking group.
Crypto-mining botnets have been a plague on the internet for the past three years, and despite the space being more than saturated, new botnets are being built and discovered on a regular basis, driven mainly by cybercriminals' unquenched thirst for easy money.
The most recent of these discoveries is a botnet named Sysrv. Active since December 2020, this botnet targets enterprise web applications, either using exploits for old vulnerabilities or a good ol' brute-force attack.
As analyzed in reports from security researchers at Alibaba's Aliyun, Juniper, and Lacework, Sysrv's internal architecture follows the classic makeup of 99% of most botnets today.
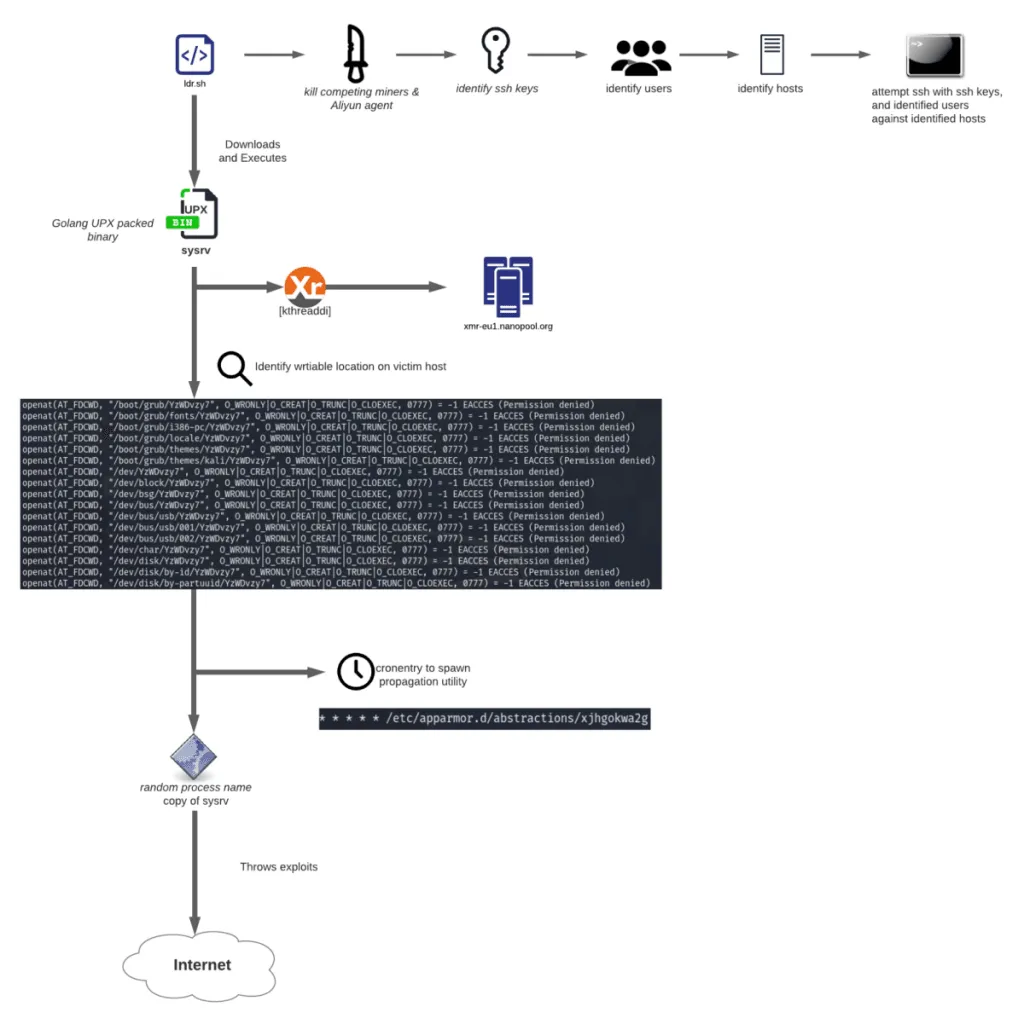
It consists of a command and control (C&C) infrastructure that scans the internet for vulnerable systems and then instructs its attack servers, or already-infected systems, to run attacks/exploits and create new bots.
Combining the three reports, we can see that Sysrv's current targets and exploit techniques include the following web apps, which are usually found in enterprise environments:
ExploitSoftwareCVE-2021-3129LaravelCVE-2020-14882Oracle WeblogicCVE-2019-3396Atlassian Confluence ServerCVE-2019-10758Mongo ExpressCVE-2019-0193Apache SolrCVE-2017-9841PHPUnitCVE-2017-12149Jboss Application ServerCVE-2019-7238Sonatype Nexus Repository ManagerCVE-2017-11610Supervisor (XML-RPC)CVE-2017-5638Apache StrutsBrute force JenkinsJenkinsJupyter Notebook Command Execution (No CVE)Jupyter Notebook ServerApache Hadoop Unauthenticated Command Execution via YARN ResourceManager (No CVE)Apache HadoopTomcat Manager Unauth Upload Command Execution (No CVE)Tomcat ManagerWordPress BruteforceWordPress
Both Juniper and Lacework mentioned that Sysrv is capable of infecting both Linux and Windows systems, a feat that not all crypto-mining botnets today can achieve, suggesting that some serious development work has been put behind this botnet from the get-go.
Under the hood, this was achieved by coding the malware in Go, a programming language that's seeing increased adoption among malware operations for this same reason—cross-platform support.
Furthermore, Sysrv is also extremely aggressive in its post-infection routine. For starters, it contains a component that will hunt down other crypto-mining botnets and shut down their processes. This suggests the botnet operator has not only thought of the competition but also studied how the rival botnets work and put together a series of countermeasures for each one, something that not all malware gangs usually care about.
Second, Sysrv also comes with a feature that scans infected servers for SSH private keys in certain locations where web developers might leave credentials to automate and interconnect different applications and development infrastructure.
Sysrv takes these SSH keys and logs into remote systems, allowing it to move laterally and wreak havoc inside a company's network, making new bots and deploying even more crypto-mining infrastructure to maximize its profits.
While security researchers have found some of the Monero cryptocurrency wallets where the Sysrv team appears to store illicitly mined funds and found profits in the range of thousands of US dollars, the botnet's profits are most likely much much higher, since these types of botnets usually like to split their earnings across multiple locations to avoid any surprises.
Both Juniper and Lacework recommend that network administrators take a look over the entry vectors listed above and if they use any of the apps, make sure they are patched and don't already show traces of a Sysrv infection.
If any infections are found—due to the botnet's ability to harvest SSH keys—companies should just wipe and rotate old credentials and then initiate incident response teams to discover other infected hosts.
As things stand right now, and thanks to the boom in cryptocurrency exchange rates, illegal crypto-mining botnets like Sysrv are expected to remain a mainstay on the malware scene for months, if not years, to come or until crypto-mining becomes unprofitable for the attackers.
Header image via EveryPixel
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



