Suspected China-backed hackers target 7 Indian electricity grid centers
China on Thursday denied any connection to cyberattacks targeting seven facilities managing the electricity grid in Northern India after a new report from Recorded Future implicated a group potentially connected to the country’s military.
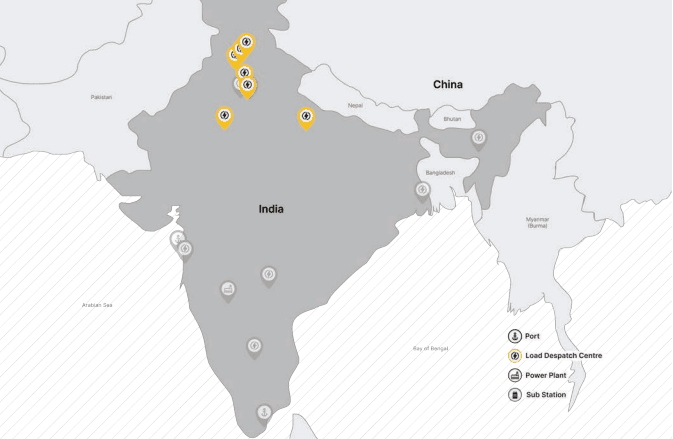
Recorded Future, which owns The Record, said it observed “likely network intrusions targeting at least 7 Indian State Load Despatch Centres (SLDCs) responsible for carrying out real-time operations for grid control and electricity dispatch” near the disputed India-China border in Ladakh.
SLDCs are responsible for carrying out real-time operations for grid control and electricity dispatch, making them critical for maintaining access to supervisory control and data acquisition (SCADA) systems.
The company added that it also “identified the compromise of a national emergency response system and the Indian subsidiary of a multinational logistics company by the same threat activity group.”
China and India – the two countries with the largest populations in the world – have been engaging in a border conflict since 2020, when there were brief skirmishes in the Himalayan region of Ladakh. At least four Chinese soldiers and 20 Indian soldiers were killed in the fighting.
The Foreign Ministry offices for India and China did not respond to requests for comment, but a reporter for Bloomberg asked Foreign Ministry spokesperson Zhao Lijian about the report during a press conference on Thursday.
“We have reiterated many times that China firmly opposes and combats all forms of cyber attacks. We will never encourage, support or condone cyber attacks. Given the virtual nature of cyberspace and the fact that there are all kinds of online actors who are difficult to trace, it’s important to have enough evidence when investigating and identifying cyber-related incidents,” Lijian said.
“One should be all the more prudent when pointing cyberattacks to the government of a certain country. As is known to all, the US is the world’s largest source of cyberattacks and [a] hacking empire. A piece of advice to the relevant company that you just mentioned: if they really care about global cybersecurity, they should pay more attention to the cyberattacks by the US government-sponsored hackers on China and other countries, and do more to promote dialogue and cooperation among countries, rather than sow discord and sling mud at China under the pretext of cyberattack issues.”
‘We are always alert’
Despite the denial, AFP reported that Indian power minister R.K. Singh told reporters in New Delhi that "Two attempts by Chinese hackers were made to target electricity distribution centers near Ladakh but were not successful."
“We are always prepared. We have a very robust security system. We are always alert,” he added.
The statements came one day after Recorded Future’s report, which details how a likely Chinese state-sponsored threat activity group may have “compromised and co-opted internet-facing DVR/IP camera devices for command and control (C2) of Shadowpad malware infections, as well as use of the open source tool FastReverseProxy (FRP).”
The use of the Shadowpad malware was what led Recorded Future experts to tie the campaign to Chinese threat actors because of how widely it is used by an “ever–increasing number of People’s Liberation Army (PLA) and Ministry of State Security (MSS)-linked groups, with its origins linked to known MSS contractors first using the tool in their own operations and later likely acting as a digital quartermaster.”
Jonathan Condra, director of strategic and persistent threats with Recorded Future’s Insikt Group and one of the authors of the report, told The Record that what stood out to him was the continued targeting of critical infrastructure by a Chinese group.
He noted that historically, they have been largely confined to economic and traditional espionage.
“The fact this targeting resumed in the face of public reporting is indicative that this activity is likely a long term strategic priority for these actors,” Condra said, acknowledging that assessing motivations for state-sponsored activity can be tricky.
“We believe that the targeting of the Indian power sector is likely for prepositioning purposes or intelligence collection with an eye towards having the capability to disrupt the Indian power sector in the event of kinetic conflict between China and India, and/or for signaling purposes to India – showcasing a capability for deterrence purposes. The targeting of the emergency system may be motivated by more traditional intelligence collection goals, but we cannot confirm at this time.”
Recorded Future previously notified the Indian government of intrusion activity targeting ten power sector organizations in India in February 2021 by a “likely Chinese state-sponsored threat activity group we track as RedEcho.” The new report notes that the latest attacks could not be attributed to RedEcho.
According to the report, the threat actors likely compromised internet-facing, third-party DVR/ IP camera devices because they are usually poorly secured. The researchers noted that other Chinese state-sponsored groups have previously compromised IP cameras.
Condra said his team did not know which brand or specific devices were compromised in this campaign and he said it was still unclear how the DVRs/IP cameras were initially compromised.
“It is plausible that they were accessed with default credentials, vulnerability exploitation, or other initial access vectors, but cannot make such a determination at this time,” he said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



