‘StrongPity’ hackers created fake video-chat app to spy on users
Suspected nation-state hackers from the StrongPity group have created a malicious Android video chat app that can record users' phone calls, collect SMS messages, and steal data from dozens of mobile apps, according to new research.
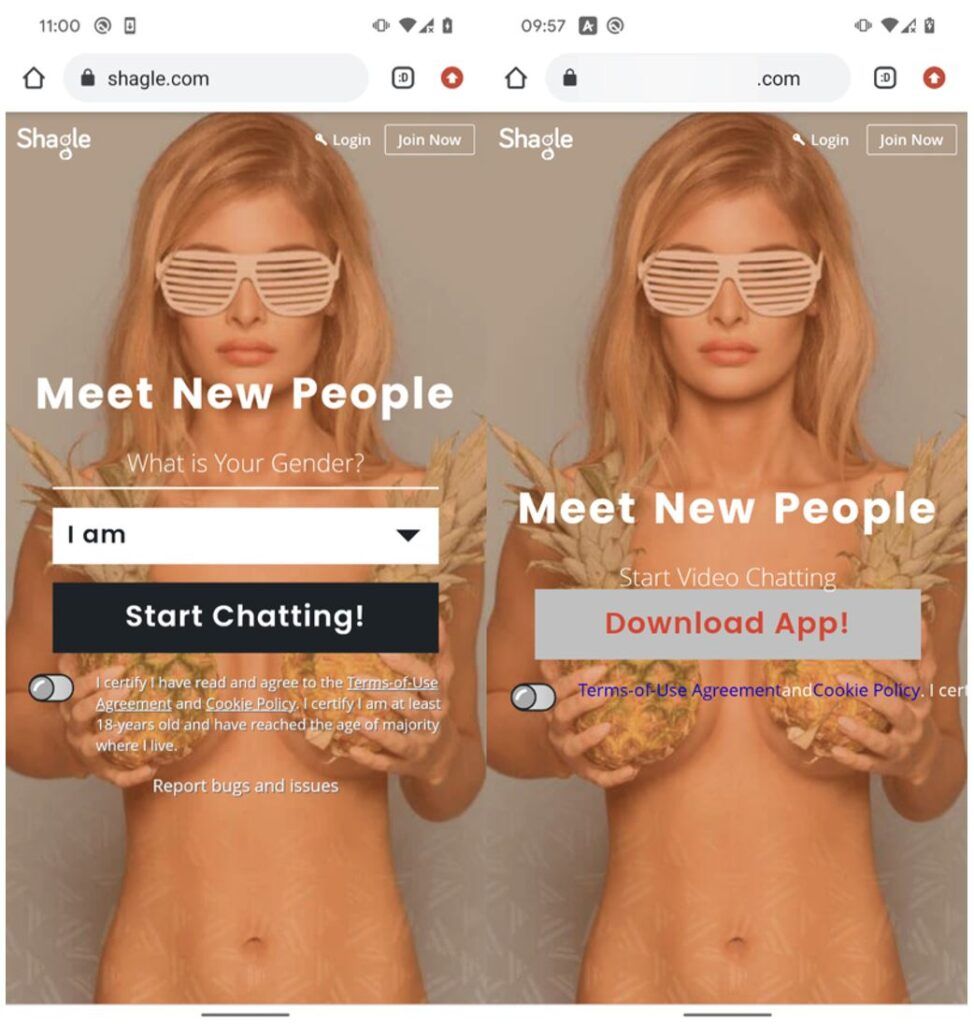
Hackers distributed the malicious app through a website impersonating a real video-chat service called Shagle, which provides encrypted communications between strangers, according to the Slovakia-based cybersecurity company ESET. The real Shagle, however, is entirely web-based and has no official app.
The fake app is based on a modified open-source code of the Telegram messenger, repackaged with StrongPity's backdoor code.
This backdoor has various spying features: it can record phone calls, collect SMS messages and contact lists, and steal data from other mobile apps such as Instagram, Twitter, Messenger, and Snapchat if users allow Shagle to access them.
StrongPity also attempted to disable the official security app on Samsung devices and turn off all notifications coming from Shagle itself, which could be displayed to the victim in case of app errors, crashes, or warnings.
The malicious app was launched in November 2021, but ESET was unable to identify any of its victims. The researchers suggest that this is because the campaign was likely to be “very narrowly targeted.”
ESET also was unable to determine how potential victims were lured to or discovered the fake website. The home pages of both websites look almost identical, but the fake one prompts visitors to download an app instead of starting a video chat.
The malicious app was never made available on the Google Play store — users could only download it directly from the fake website.
Additionally, the malicious Shagle app is no longer active because it used a sample API ID from Telegram for initial testing purposes, which was deactivated by Telegram.
“Since no new and working version of the app was ever made available through the website, it might suggest that StrongPity successfully deployed the malware to its desired targets,” the researchers said.
It was also impossible to install the fake Shagle app on potential victims' devices if they already had Telegram installed, as both apps had the same IDs and could not co-exist on Android. According to ESET, this might mean one of two things — either StrongPity first communicated with potential victims and pushed them to uninstall Telegram from their devices, or the campaign focused on countries where Telegram isn’t ubiquitous.
And while the app is currently unavailable, that could change at any time if hackers decide to update it, researchers warned.
StrongPity has a history of using Android malware to spy on users. Last year, the group created a malicious version of the Syrian e-government Android app and replaced the real app on the government website with the fake one. This app could steal contact lists and collect files from its victim's device, according to research by Trend Micro.
Compared to the previous campaign, the new StrongPity backdoor has extended spying features, according to ESET. Although it’s unclear which country backs StrongPity, some security researchers have said it is likely a Turkish group.
StrongPity has been active since 2012 and usually follows the same tactics of adding backdoors to legitimate software used by certain users. StrongPity’s malware has infected thousands of systems in Italy, Belgium, Algeria, and France.
Daryna Antoniuk
is a reporter for Recorded Future News based in Ukraine. She writes about cybersecurity startups, cyberattacks in Eastern Europe and the state of the cyberwar between Ukraine and Russia. She previously was a tech reporter for Forbes Ukraine. Her work has also been published at Sifted, The Kyiv Independent and The Kyiv Post.



