New Stealc malware-as-a-service targets web browsers, crypto wallets, email clients
Researchers have identified a popular new information stealer being advertised for purchase on Russian-speaking dark web forums.
Stealc is a ready-to-use stealer that can compete with other popular malware families such as Vidar, Raccoon, Mars and Redline, according to a report published by threat intelligence company Sekoia.io this week.
It targets sensitive data from at least 23 web browsers — such as Google Chrome, Vivaldi and Mozilla Firefox — as well as popular desktop cryptocurrency wallets, like Binance and Coinomi. Stealc also goes after web browser-based wallets, email clients and messenger software.
"Companies facing stealer compromise need to be aware of this malware," Sekoia.io said. "We expect that the Stealc infostealer will become widespread in the near term, as multiple threat actors add the malware to their arsenal while it is poorly monitored."
Malware-as-a-service tools like Stealc lower the entry barrier to the cybercrime world by allowing hackers without advanced technical skills to purchase readymade kits from online marketplaces and quickly and easily launch cyberattacks.
In January and February, researchers discovered dozens of Stealc samples circulating in the wild, indicating that this new info-stealer has traction among cybercriminals, they said.
Infection with the malware happens when a cybercriminal tricks someone into downloading it. Sekoia.io found one example involving hijacked YouTube sites that promoted links to pirated software. Clicking on the links led to a disguised installer for Stealc instead of the software.
Customization is king
Stealc can customize its data collection features based on a user's needs, which makes it stand out from other stealers analyzed by the researchers.
It also has a customizable file grabber used to obtain sensitive or confidential information such as login credentials, financial information, or personal data from a victim’s computer or network.
The stealer’s administration panel, a web-based interface that is used to manage a hacking tool or program, includes a suite of features. It allows hackers to set up the malware configuration, to display, filter, sort and analyze the stolen data, and download the logs in a personalized way.
According to researchers, the developer behind the malware “almost certainly” put in great effort to develop features for handling data logs since hackers are likely to sell the stolen information on marketplaces.
Customer-oriented
Stealcʼs alleged developer is going by the handle Plymouth on XSS and BHF — two Russian-speaking dark web hacking forums created to share knowledge about exploits, vulnerabilities and malware. There are advertisements for the malware on additional channels, including the Exploit hacking forum and Telegram messaging app.
Plymouth “quickly established itself as a reliable threat actor, and its malware gained the trust of cybercriminals dealing with infostealers,” researchers wrote.
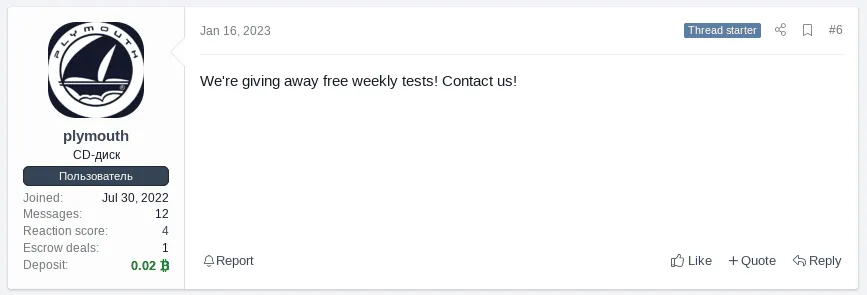
A screenshot from a post on the XSS darknet forum. Image: Sekoia.io
To gain the trust of potential customers, Plymouth offers free weekly malware tests, in which users test the tool and provide feedback on the product. While the stealer is already functional and adopted by several undisclosed threat actors, the developer continues to add new features every week and improve both malware and administration panels, according to the research.
Daryna Antoniuk
is a reporter for Recorded Future News based in Ukraine. She writes about cybersecurity startups, cyberattacks in Eastern Europe and the state of the cyberwar between Ukraine and Russia. She previously was a tech reporter for Forbes Ukraine. Her work has also been published at Sifted, The Kyiv Independent and The Kyiv Post.



