Hackers to show they can take over a European Space Agency satellite
Cybersecurity researchers will show this week how they seized control of a European Space Agency (ESA) satellite in a demonstration that has been described as the world’s first ethical satellite hacking exercise.
Experts from French defense giant Thales announced on Tuesday that they, alongside members of the ESA team, will provide an in-depth explanation of the attack scenario at the CYSAT conference in Paris.
The exercise was planned before the release of a tranche of highly classified U.S. intelligence documents, one of which warned that China is developing similar capabilities to seize control of what it assesses to be hostile satellites.
The document, which was first reported by the Financial Times, suggests that China intends to surpass the traditional form of communications jamming that blocks signals between satellites and terrestrial terminals.
Instead the attackers would mimic the operator signals, potentially enabling them to “seize control of a satellite, rendering it ineffective to support communications, weapons, or intelligence, surveillance and reconnaissance systems,” stated the document.
The demonstrative hack was specifically organized for the CYSAT conference to provide an example of the consequences that real-world cyberattacks could have on civilian systems in space.
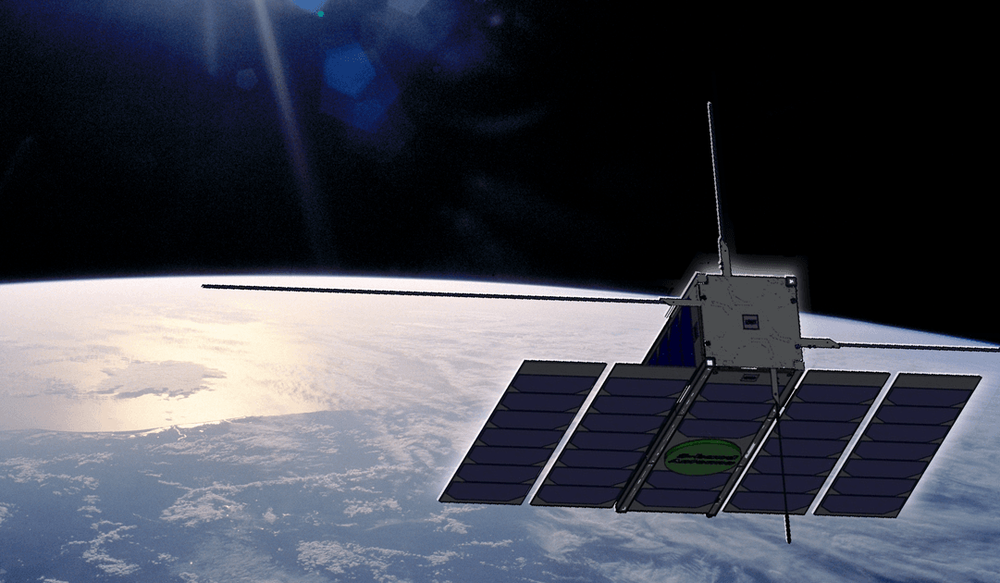
It targeted ESA’s OPS-SAT, a nanosatellite about the size of a shoebox that was launched in December 2019 and contains “an experimental computer ten times more powerful than any current ESA spacecraft.”
The point of OPS-SAT is to address the risks involved in live testing mission control systems. Thales stated that ESA retained access to the satellite’s systems throughout the exercise so it could return to normal operation afterwards.
“This unprecedented exercise was a chance to raise awareness of potential flaws and vulnerabilities … [and] to improve the cyber resilience of satellites and space programmes in general, including both ground segments and orbital systems,” said Pierre-Yves Jolivet, the vice president of cyber solutions at Thales.
Although the full nature of the Thales demonstration is not yet clear, the company says its team was able to hijack a number of systems used to operate the demonstration satellite in what appears to be a traditional cyberattack.
The company said its ethical hackers exploited the satellite’s “standard access rights to gain control of its application environment” before then exploiting vulnerabilities and introducing malicious code to the satellite’s systems.
“This made it possible to compromise the data sent back to Earth, in particular by modifying the images captured by the satellite's camera, and to achieve other objectives such as masking selected geographic areas in the satellite imagery while concealing their activities to avoid detection by ESA,” said Thales.
The demonstration comes as space cybersecurity in general has received more attention from experts. A U.S. government-backed panel recently urged the Biden administration to designate space as a critical infrastructure sector.
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79