Some ransomware gangs lose interest in extortion sites
In late 2019, the ransomware group known as Maze pioneered a tactic that soon spread throughout the cybercrime underground: steal encrypted data and threaten to release it publicly unless a ransom is paid.
But according to data collected from the sites these groups operate, the practice that's sometimes referred to as “double extortion” appears to be declining.
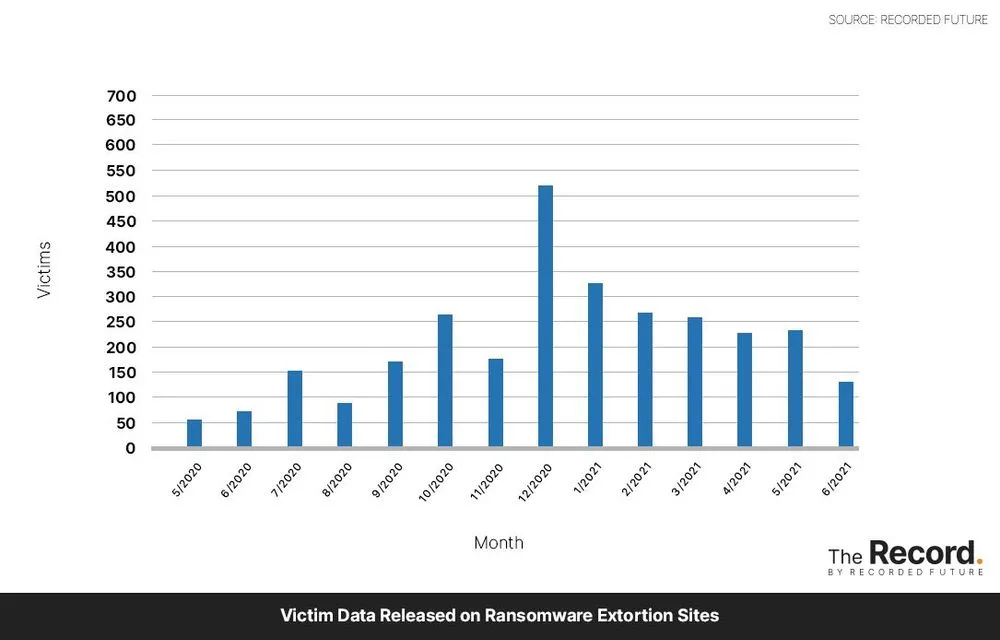
Data released on ransomware extortion sites rose somewhat steadily in 2020 and reached a peak of 521 victims in December of that year. But that number has shrunk almost every month in 2021, and dipped to just 129 victims in June—the lowest number since August 2020.

Allan Liska, a ransomware expert at Recorded Future who has been tracking leak sites operated by ransomware gangs, said these groups are likely realizing that threatening to post stolen data isn’t making them more money.
“Ransomware actors came up with this whole system that they thought would encourage people to pay, and us researchers and journalists lapped it up and said it made perfect sense,” he said. “But we’ve seen over time that companies don’t really suffer consequences if their data winds up on extortion sites. Ransomware actors aren’t always the psychological geniuses we think they are.”
In recent months, groups like Babuk have pulled away from posting victim data on leak sites, deciding to focus on traditional ransomware demands and other types of cybercrime, Liska said. “We saw them focus entirely on extortion, and two months later they’ve gone back to ransomware—it turns out that no one wants to pay to stop their data from being posted.”
Other major ransomware groups including Avaddon, REvil, and Clop have shut down or experienced extended disruptions in recent months.
Another reason extortion sites might be in decline is that they are seen as a liability for the groups. The sites require the groups to publicly expose more of their infrastructure, which could make it easier for law enforcement to shut down their operations. Additionally, it could encourage victims to work with law enforcement because the tactic makes it impossible for companies to bury ransomware attacks under the rug.
To Liska, this last point potentially forced companies to give ransomware the attention it needs. “One of the things extortion sites did was expose how big our ransomware problem is,” he said. “Most ransomware attacks aren’t like Colonial Pipeline—nobody ever knows about them because the companies don’t want to make them public. Now ransomware is in the news constantly, because the attackers are making them public.”
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.