Singapore's deputy cyber chief on how the city-state became a laboratory for security initiatives
Last spring, professional services firm Deloitte published a study that ranked Singapore as the most exposed country to cyberattacks in the Asia-Pacific region. The city-state was also deemed the most prepared at defending against them.
Over the last decade Singapore has aggressively rolled out a slew of cybersecurity initiatives aimed at protecting its nearly 6 million highly-connected citizens from cyber threats. As a global financial and shipping hub, it took early steps at bolstering critical infrastructure security and reducing barriers to information sharing between the public and private sectors. More recently, the country has rolled out cybersecurity labels for consumer smart devices, and awards marks of distinctions to companies that have invested heavily in cybersecurity.
Ng Hoo Ming leads the country's National Cyber Security Centre, and serves as deputy chief executive of Singapore's Cyber Security Agency, which has launched many of the initiatives since its 2015 debut. But in addition to the domestic programs, Hoo Ming says Singapore—as a small country with big rivals—recognizes the need for global norms and stronger international laws around cybersecurity.
"We need to consider cybersecurity as a common good which is managed in the interest of the public and is beneficial to all of us," said Hoo Ming, who previously served as the director of Singapore's Infocomms Technology Security Authority, which was in charge of responding to attacks against the nation's critical infrastructure. "When we start to view it as a common good, we start to understand that there's a need for a global consensus on cybersecurity."
The Record caught up with Hoo Ming recently via videoconference to discuss Singapore's recent cybersecurity efforts and what the U.S. and other countries can learn from those initiatives. The following conversation has been lightly edited for clarity.
The Record: Which measures or initiatives has your organization taken that have been the most impactful?
Ng Hoo Ming: There are quite a lot of activities that we initiated, but let me first put things in context. The Singapore government treats cybersecurity as an existential issue, as our society is very highly connected. Fiber broadband exists in almost every household, and most businesses rely on the internet in one way or another. This trend has been accelerated by COVID-19, and even mom-and-pop companies that have no experience with digital technology are embarking on online platforms to push their services. I think something interesting to note is that you’ve probably heard a lot about smart cities—in Singapore, we’re embarking on a Smart Nation Initiative, because we’re a city state. All these developments on the digitization front make us very vulnerable to any form of cyber threats.
In view of increasing cyber risks, the Singapore government saw the need to establish a centralized national cybersecurity agency, and that’s why the Cyber Security Agency of Singapore was established in 2015. Prior to that, cybersecurity was scattered across different agencies. Take me for example—I was the director of the Singapore Infocomm Technology Security Authority, and my only focus was on securing the critical infrastructure, not the policies, other industry developments, or international engagements. When CSA was formed, it was done so under the aegis of the Prime Minister's Office—you need someone who has the highest authority to provide credibility and backing across governments, both domestically and internationally. And in order to create this resilient and trusted cyberspace, it's important for the public to know about the government's role in cybersecurity.

A lot of our work in the early years culminated in the launch of Singapore’s Cybersecurity Strategy in 2016, and since then we've gone through a few rounds of minor revisions to the strategy. But by and large you can summarize it as four pillars, the first being building a resilient infrastructure. We have identified 11 sectors as Critical Information Infrastructure sectors, and CSA plays both the role of a regulator and a partner to these operators to ensure our CII operators have the measures in place to detect and respond and recover from a cyber threat in a prompt and expedient manner. We have developed a multi-tier national cybersecurity response plan that draws out clearly the processes for dealing with all the cybersecurity incidents at a national level. It's very different from how it’s done in most other countries: We have a three-tier model with CSA sitting at the top as the national authority, the second tier includes sectoral regulators, and tier three includes all CII operators. It's how we systematically developed this process, and conduct exercises to make sure there's no misunderstandings during any incidents.
Another important policy is the Cybersecurity Act, which was launched in 2018 to help us have a better organizational mandate. It has a few main objectives—the first is to strengthen the protection of the CII sectors against cyberattacks. We have a Commissioner of Cybersecurity who has the power to designate a system as a CII asset. The moment you designate something as a CII, there are obligations for the system owner to adopt, in terms of protections and other things. It's very important because cybersecurity is often seen as a cost instead of a business enabler. Most of the operators would not want to invest and would not want to qualify as a CII because it requires them to really beef up their cybersecurity posture.
The Cybersecurity Act also authorizes my officers to prevent and respond to cybersecurity threats. During incidents, we have the power to request information to facilitate our investigations. We have also established a licensing framework for cybersecurity services providers, and we focus on two groups—pen testers and managed security service providers. These are the people who have intimate understanding of the systems and potentially, the loopholes. We want this group to be accredited and to uphold professional ethics.
Imagine if in Singapore, our financial infrastructure hub was hit, and our stock market impacted. It's not just Singapore that will be affected. The region, and other financial hubs, would be affected as well. If our ports were paralyzed, all the goods would not be able to move."
Finally, the Cybersecurity Act facilitates information sharing between CSA and the operators. As you know, it's often very difficult to share classified information between the government and the private sector, and most of the CII operators are privately owned. So the Act was necessary to allow for greater ease of sharing information with the private sector. It helps to identify system vulnerabilities and prevent cyber incidents more effectively. The Act also gives us a framework on when operators share information with CSA. CSA has the duty to protect the information shared with us. We cannot use it for any other purposes. We can only use it to help protect against other cyber incidents. We cannot use it to inform the sector regulators that they're noncompliant, or other things. It provides a comfort level that helps with their willingness to share with us.
The last initiative I’ll mention is noteworthy given what we’ve seen recently with supply chain attacks—we started an initiative to study cybersecurity risks in critical infrastructure. We recognize that most organizations, including the CII owners, engage their OEM suppliers to support their organizations, which can create a backdoor for malicious actors to exploit and potentially compromise the systems. We have witnessed this very often. Service providers, not being a CII, have much lower security standards. We therefore need to expand beyond protecting the CII sectors, to manage the security risk from the supply chain. We are working with consultants and hopefully once the study is completed we will be able to share the information with the industry and potentially share with an international panel as well.
TR: Experts estimate that more than 80% of the U.S.'s critical infrastructure is privately owned. What fraction is it in Singapore?
HM: Government services like safety and emergency response, which falls under critical infrastructure, are obviously owned by the government, but by and large, the rest of the CII sectors such as financial, transport, maritime are more or less owned by the private sector. And they're not private in the same way they might be in the U.S. Citibank, for example, only has a footprint in Singapore, but still has to be classified as a CII. Sometimes the infrastructure isn't hosted in Singapore, so it can be very difficult to exercise our power beyond our national jurisdiction. We have to come to mutually-agreed positions.
When an organization is characterized as a CII, it comes with obligations. But the government has to give certain incentives and provide a helping hand as well. It is a partnership of sorts. When there are stipulated measures, we don't enforce a singular approach—there are many ways to comply and we try to take the best way or the most cost-effective way.
TR: How do you use policies to protect your country and companies in Singapore?
HM: We are only as strong as the weakest link, so it's important for small businesses and the general public to be more diligent about protecting their digital life to improve our collective safety in cyberspace. In this regard, we launched the Safer Cyberspace Masterplan, which outlined a blueprint for a safer and more secure cyberspace in Singapore. It was developed in consultation with industry and academic partners, and the aim is to raise the general level of cybersecurity for individual users and community enterprises. It consists of three strategic thrusts—the first is to secure our core digital infrastructure, such as our internet infrastructure, our telecommunications infrastructure. The second thrust is to safeguard our cyberspace activities, and the third is to empower our cyber savvy population. There are various programs we run depending on the audience, so for instance, we visit junior schools to teach students about cybersecurity together with cyberbullying and other relevant topics.

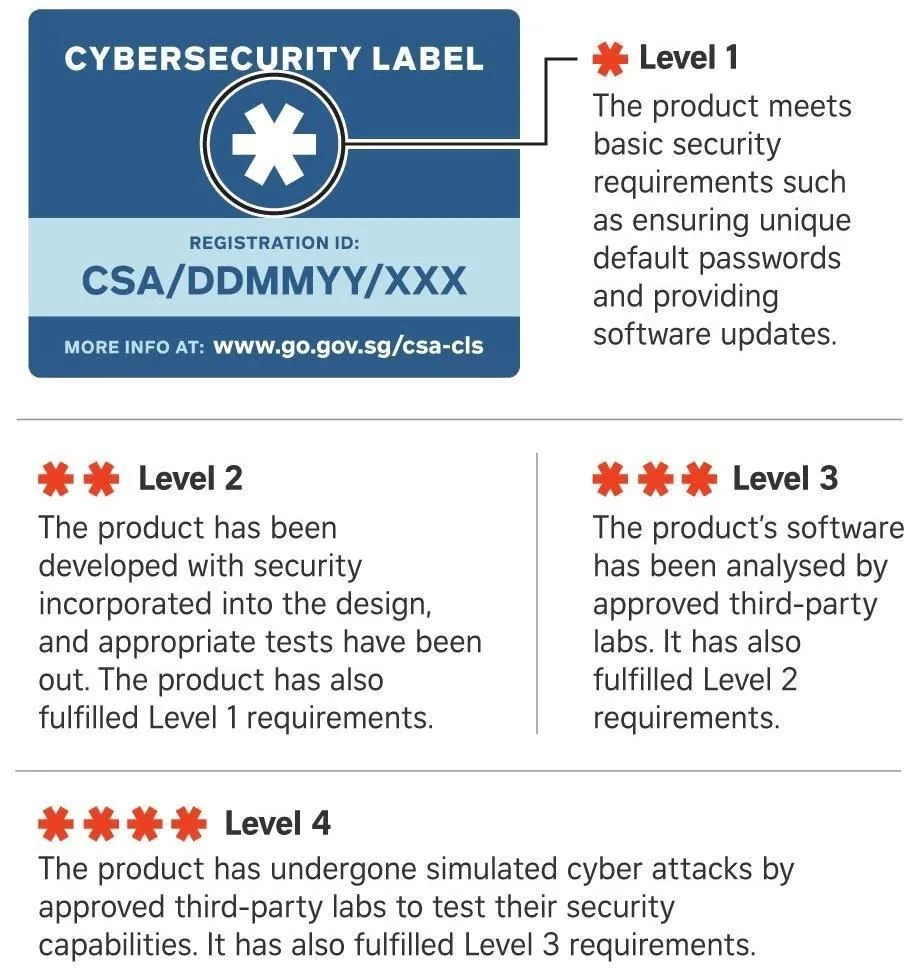
Another initiative we have is the Cybersecurity Labelling Scheme, also known as the CLS. It's for consumer smart devices, and is part of our efforts to improve IoT security and raise overall cyber hygiene levels. It provides greater transparency on the security of consumer smart devices, such as home routers and cameras, through the use of a label to indicate the security rating of a product, based on a series of assessments. The CLS provides an instrument to help consumers make informed choices when purchasing devices. It also incentivizes companies to develop more secure products. The scheme at this moment is voluntary. Companies make their own assessments and declare that their products fall under a certain level. We hope that the industry will become more mature and we may consider making the scheme mandatory for some products.
The CSA also funded an IoT Security Reference Architecture study which was undertaken by a university in Singapore. The study is aimed at helping to design a more secure IoT system. The report titled ANT-Centric IoT Security Reference Architecture – Security-by-Design for Satellite-Enabled Smart Cities was officially accepted by the IEEE Internet of Things Journal and will be published at the IEEE portal in a month’s time, and we're quite proud of it. Hopefully the report will attract more people to embark on this journey with us and prototype and promote a secure reference architecture.
The last initiative I’ll mention is the SG Cyber Safe Trustmark, which serves as a mark of distinction for companies that have invested significantly in cybersecurity. It's a cybersecurity assurance mechanism—it shows customers that this organization prioritizes cybersecurity and has adopted measures that correspond with their risk profile. It helps organizations value cybersecurity as a key competitive advantage, rather than looking at it merely from a business cost perspective.
TR: There have been efforts in the U.S. to create a cybersecurity label for consumer goods, but so far it hasn’t gotten off the ground. What lessons have you learned from the program so far?
HM: The CLS has been around for less than a year, but since its launch, it has been well received by industry, and some products already have the labels. Most companies just go for the basic rating, but for the more critical devices, we're pushing them to go up a level or more. And yes, the U.S. has cited Singapore's efforts when they spoke of wanting to start a label system for the software industry. I think we are heading in the right direction.
TR: What role do you play in training and developing Singapore’s cybersecurity workforce?
HM: We aim to develop a vibrant cybersecurity ecosystem. The government recognizes that cybersecurity is a growth sector in our economy, where good jobs remain available even during the COVID-19 pandemic. Because of work-from-home and other developments, the demand for cybersecurity specialists has remained strong. We have attracted the world's top cybersecurity companies to establish a presence in Singapore and they'll help to grow the local companies and expertise. We're looking to attract not just the people in Singapore to join the sector, but also entrepreneurs from around the world who want to establish a start-up in Singapore. We have started an entrepreneurship hub that seeks to create a vibrant and sustainable innovation ecosystem by providing access to funding, go-to-market support, and mentorship support from the cybersecurity community.

We have also launched another initiative that focuses on the workforce. The SG Cyber Talent initiative aims to attract a stronger and more diverse pipeline of professionals to join the workforce and enhance the skills we have. It will reach out to more than 20,000 people who will be groomed for cybersecurity over three years and it will help advance their professional journey in cybersecurity.
TR: What international policies or norms are you pushing for?
HM: As you know, cyberspace is borderless and the threats we face are asymmetric. There's a need to strengthen international partnerships, and we recognize that combatting this threat requires international collaboration. As a small city state, Singapore firmly believes in the importance of a rules-based international order for cyberspace, based on the applicable international law and the voluntary adoption of those norms. The norms should be complemented by other efforts to drive international collaborations in cyber.
Singapore has leaned forward with things like Singapore International Cyber Week, which is an event in Asia that might be the region's biggest cybersecurity-focused event. Typically, during this event, we would hold the ASEAN Ministerial Conference on Cybersecurity (AMCC), where all the ASEAN ministers gather in Singapore to discuss policies and collaborations. At the 4th AMCC in 2019, ASEAN member countries developed a long-term Regional Action Plan to ensure the effective implementation of the norms we discussed. There are metrics to track the progress made by the individual countries, which is interesting. And last year they recommitted to these norms and the urgent need to protect cross-border CII.
Most of the time, when we speak of CII, we talk about it within the national boundaries. This is the first time we talked about cross-border CII. Singapore is a shipping hub, a telecommunications hub, and a financial hub. It is important that our infrastructure should not be attacked. The impact goes beyond our national borders. Imagine if in Singapore, our financial infrastructure hub was hit, and our stock market impacted. It's not just Singapore that will be affected. The region, and other financial hubs, would be affected as well. If our ports were paralyzed, all the goods would not be able to move.
TR: Are there any cybersecurity policies that you view as harmful or counterproductive?
HM: I think there are some policy gaps that have a tremendous impact on cybersecurity. Data governance is one example. Cybersecurity is clearly tied to data governance, and cyber must be considered in the policy decisions on data governance. Unfortunately, there's no harmonized standard among the cybersecurity community for data governance. We're left with a fragmented approach, and the tech giants are allowed to define their own policies that are not necessarily aligned with a country's interests. Some social media platforms have been known to harvest huge amounts of user data, and they track all the online habits of their users in order to drive more targeted services, in the name of better customer service. But the privacy terms laid out by these companies is obfuscated behind legalese that average users like us would find challenging to comprehend. Users are often left wondering what are the measures these companies have in place to safeguard their data and what all this data is being used for.
There must be an international global consensus to identify what are the common root infrastructures. And if it's common, we should all work together to protect it. It's common sense, and this is the message we're trying to drive."
We have to see cybersecurity as a common good, and there's a need for a group consensus. Because the internet forms the backbone of our digital society, it's often interwoven with economic, social and political elements—we talk about fake news, misinformation. The security of the internet has direct and indirect implications for the masses, and it enables infrastructure to work, businesses to operate. The modern society we live in is highly interconnected. A cyberattack that occurs in one country may affect another. An attack that affects one infrastructure system may affect another too.
There must be an international global consensus to identify what are the common root infrastructures. And if it's common, we should all work together to protect it. It's common sense, and this is the message we're trying to drive. We need to consider cybersecurity as a common good which is managed in the interest of the public and is beneficial to all of us. When we start to view it as a common good, we start to understand that there's a need for a global consensus on cybersecurity. Cyber threats may undermine the stability of ICT environments and put all the digital technology that global sectors rely on at risk. As you can see, major cyberattacks are reported more frequently than ever, with devastating impacts observed globally. We’ve seen several big incidents in the span of a few months. It is now clear that cybersecurity is a challenge that countries must tackle together. Cyberattacks don't respect national or organizational borders, so the governance has got to be global.
TR: What’s an example of a policy that you would want to see more countries adopt?
HM: Cybersecurity is a multi-stakeholder problem, and technology is a double-edged sword that brings both opportunities and dangers. We earlier talked about the dangers of data privacy violations if we allow the private sector to self-regulate. In order to secure the public's trust, the onus is on the government agencies and the companies to play their part in ensuring that data violations are taken seriously. We need an approach to data governance where users and industry come together. Governments can help create a safe and trustworthy cyberspace by putting in place a sound regulatory framework and policy for technology companies to know the rules to abide by. Some examples include the EU’s General Data Protection Regulation, which makes privacy paramount and reinforces the importance of good data governance. Closer to home, Singapore introduced an enhanced Personal Data Protection Act, expanding the ability of organizations to use personal data. We allow the use of data, but it has to be done so in a controlled manner, and this increases the accountability of data breaches. Breaches now come with the liability that companies have to do their due diligence to protect the data, and if there's a data breach you must inform people in a timely manner, failing which you can be fined up to $1 million [about $750,000 USD].
From the company perspective, they have to do their part to safeguard their customers. I always like to talk about corporate social responsibility. Some companies have set up a KPI for it and have dedicated departments working on it. But at the same time, it's important, especially in today's context, for companies to play their part in their corporate cyber responsibilities by being more accountable for their users' data and explicitly stating their regulations pertaining to the terms and conditions and ethical code of conduct. It's even more important for companies to adhere to them and provide assurance for their users. For the users, we must safeguard our data and arm ourselves with information about the cyber risks we face and the type of information that we share in the digital space before using some of these applications. In today's interconnected world, the amount of data within global cyberspace is tremendous, underscoring the importance of cybersecurity. Data governance and regulations should not be viewed as an obstruction to operations but rather, as a safeguard and enabler of operations to carry on during the increasing presence of cyber threats that cut across citizens, businesses and nations.
TR: When you look ahead five years, what policies and initiatives are you planning to prioritize?
HM: Some of the initiatives I talked about will continue—they won't be outdated or be obsolete. For example, building resilient infrastructure is a journey. How do we incentivize the CII operators to adopt a more proactive stance towards combating cyber actors? The challenge for CSA is how to constantly keep ourselves, our policies, our technical recommendations up to date and current with the evolutions of security threats, and how we can build defense systems that are futureproof.
We have solutions for some of these challenges. Others, we're still trying to sort it out. For example, I'm trying to understand what is zero trust and how to build trust on zero trust. I've identified the problems but I've yet to find convincing technical solutions. This is especially relevant in IoT devices, where there are no boundaries. How do you build trust on a network that may contain something like a connected lamp post? We talk about identity and how to derive it, and so on. The other approach is very traditional, using PKIs. I believe this has its own challenges as well—for instance, it will not be scalable to address something like the IoT Smart Nation scenario. This approach has inherent weaknesses in scalability. Imagine a country like Singapore where we're talking about hundreds of millions of devices—I can't imagine having PKIs to manage hundreds of millions of keys. It's impossible. So the challenge to me is what's the next technology if the traditional approach is not feasible.
TR: What are Singapore’s biggest international cyber threats? How do you view nations like China and North Korea?
HM: For political and security reasons, we have not done any public attributions. That's our policy. But we're facing a myriad of threats from different threat actors, including criminals and APT groups. We do what we do, and some of the attacks that we've encountered, they can be an APT group in the day but when the night falls, they may moonlight and start to steal corporate information, carry out ransomware attacks and sell information on the dark web. But we have not named any countries. We just try to deal with the attack.
TR: I like that—don't cause more problems than the ones you already have.
HM: Yes (laughs).
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.



