SAP systems usually come under attack 72 hours after a patch
Companies that run on-premises SAP systems usually come under attack 72 hours after security patches are released, SAP and enterprise security company Onapsis said in a joint security alert published today.
Onapsis and SAP said they observed more than 300 successful exploitation attempts through a network of proprietary sensors during a recent study of the SAP threat landscape.
The study's findings point to the conclusion that attackers are reverse-engineering SAP patches as soon as they become available to create proof-of-concept exploit code they could weaponize against SAP's customers.
The window for defenders is significantly smaller than previously thought, with examples of SAP vulnerabilities being weaponized in less than 72 hours since the release of patches, and new unprotected SAP applications provisioned in cloud (IaaS) environments being discovered and compromised in less than 3 hours.
SAP and Onapsis
According to the two companies, attacks weren't simple one-shot attempts but sometimes also involved multiple moving parts, including vulnerability chaining.
Furthermore, attackers used proof-of-concept code to attack SAP systems, but also brute-force attacks to take over high-privileged SAP user accounts. The goal of these attacks was to take full control of an SAP deployment in order to modify configurations and user accounts to exfiltrate business information.
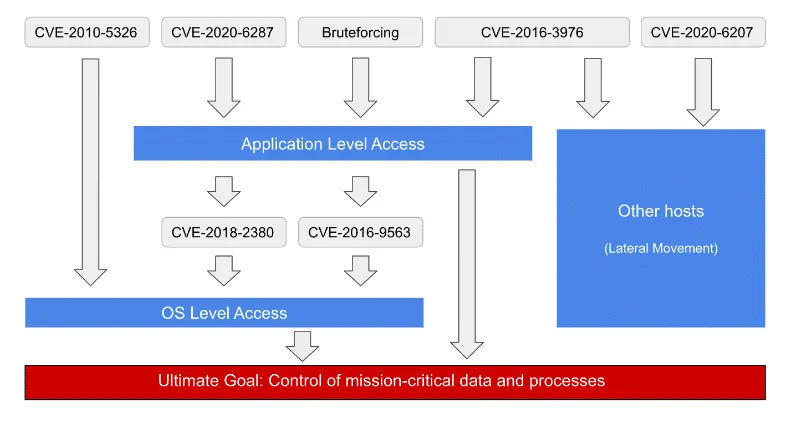
"It is important to note that while most of the observed threat activity is related to the use of publicly-available exploits released following SAP patches, Onapsis researchers have detected indicators of custom/private exploits not available in the public domain," the two companies said.
Onapsis says that while the scope of this recent report was to study internet exposed on-premises SAP systems, which are more likely to be exploited, the security firm also stressed that many of these vulnerabilities could be exploited inside corporate systems where SAP systems aren't exposed online, but attackers gained access through other vectors.
A list of vulnerabilities that Onapsis saw attackers use against its SAP honeypots is available in the table below.
To highlight the importance of its findings and the need for companies to apply patches for old SAP vulnerabilities, Onapsis said it is making its security solution —the Onapsis Platform for Cybersecurity and Compliance— available for free via a three-month subscription on the SAP Store, so companies can scan their internal networks to find and patch systems.
The US Cybersecurity and Infrastructure Security Agency (CISA) has also issued a security alert about the threats to SAP systems today, picking up on the report's findings and the need to update systems to their latest patch levels.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



