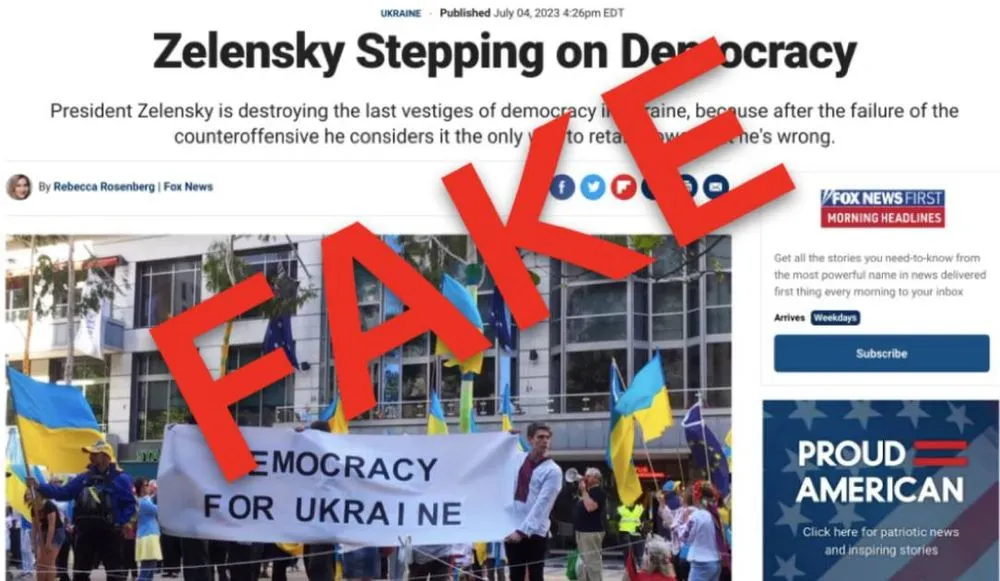
Russians impersonate Washington Post and Fox News with anti-Ukraine stories
Fake articles masquerading as legitimate stories from The Washington Post and Fox News were spread online by a Russian disinformation campaign attempting to undermine Western support for Ukraine, according to Meta’s latest threat report.
The relatively new moves to spoof media organizations in the United States expands upon the campaign's previous concentrated targeting of Germany, France and Ukraine itself.
The social media giant says the two companies behind the operation — Structura National Technology and Social Design Agency, both of which were previously sanctioned by the European Union after being exposed by Meta — have engaged in “the largest and most aggressively persistent covert influence operation from Russia that we’ve seen since 2017.”
This operation, named Doppelgänger, has persevered in its attempts to influence Western opinion despite numerous disruptions by Meta and “continuous scrutiny by platforms and researchers.”
The influence operation has been spoofing the domains for news sites and publishing false stories that are critical about Ukraine’s President Volodymyr Zelensky, or U.S. President Joe Biden and the White House’s policy on Ukraine, before spam-posting links to these stories across social media platforms.
“Some of these spoofs were particularly elaborate,” noted Meta, with one Washington Post article based on “a faked Russian-language video which purported to show President Zelensky admitting that he was a puppet of the CIA.”
This article, and another purporting to be published by Fox News, used the bylines of real journalists employed by those organizations. The journalists and their employers declined to comment about the impersonations when contacted by Recorded Future News.
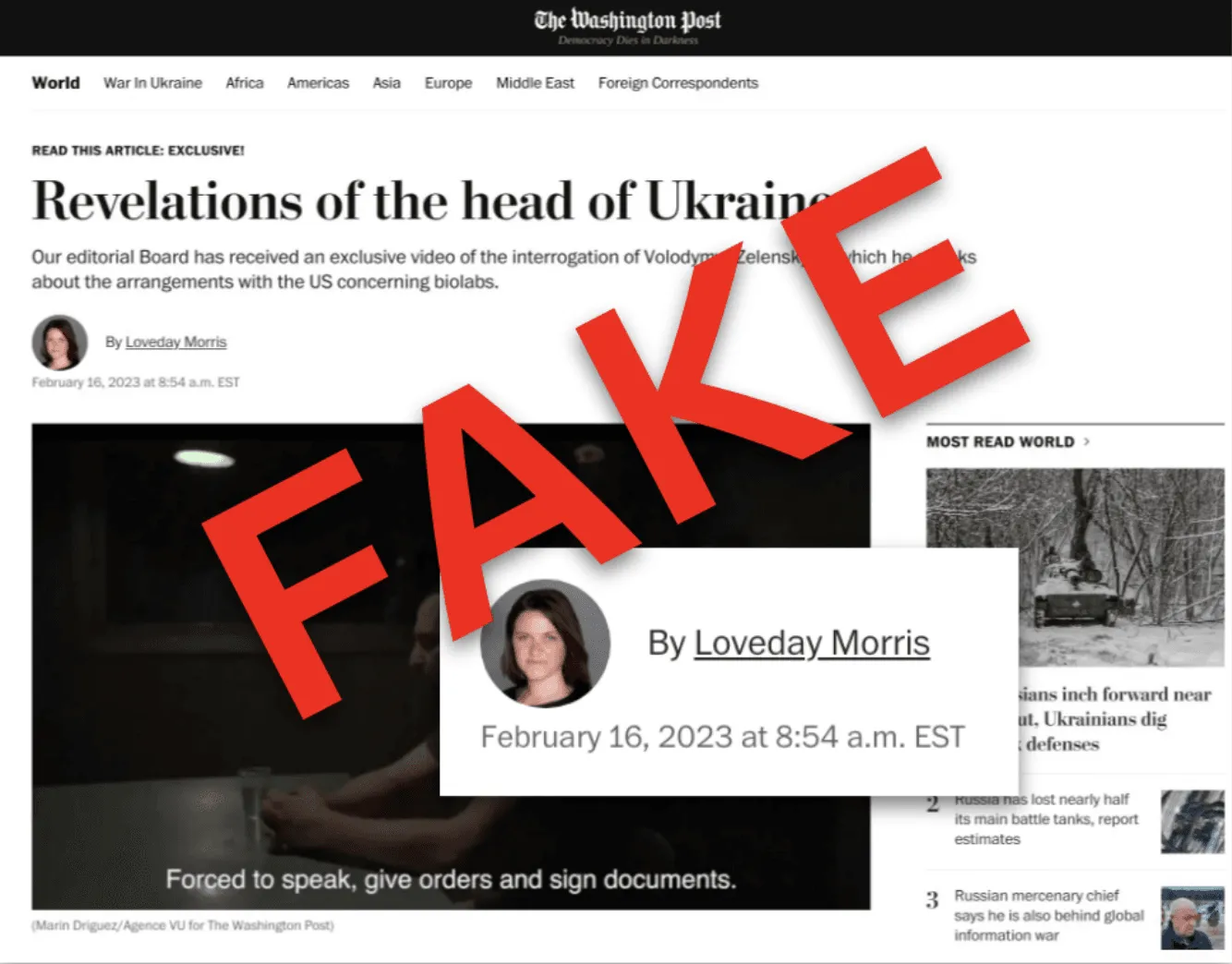
Image: An example of a fake article purporting to be from The Washington Post. Credit: Meta
Meta says the companies behind the campaign may be “incentivized to exaggerate their own effectiveness, engaging in client-facing perception hacking to burnish their credentials with those paying them.”
The covert influence campaign was launched shortly after Russia’s full-scale invasion of Ukraine last year, as previously identified by Meta, when Western media outlets including The Guardian, Der Spiegel and Italy's ANSA news agency were impersonated to run fake stories.
In one fake news story, based on an original report in The Guardian regarding a massacre of civilians in the Ukrainian city of Bucha, the operation claimed that Ukraine had staged the killings. The mass murder of civilians in Bucha by the Russian armed forces has been documented by the UN High Commissioner for Human Rights.
Back in June, before the Russian companies behind the operation were sanctioned, officials from France’s Vigilance and Protection Service against Foreign Digital Interference, also known as VIGINUM, accused the Russian actors of launching “a digital information manipulation campaign against France,” with the assistance of Russian state entities.
Russian embassies and cultural centers were accused by the French Foreign Affairs Ministry of having “actively participated in amplifying this campaign,” which involved the creation of fake websites impersonating French government departments and national media outlets. The French officials did not specifically allege that the operation had been sponsored by the Russian government.
Domain name abuse
Meta said the operation provides a good example “of how bad actors use malicious domains to insulate themselves from enforcement.” The company also offered a number of policy recommendations regarding domain name abuse.
“We’ll continue disrupting this large-volume but low-impact activity on our platform, monitoring for further developments and sharing our findings with our industry peers, researchers and the public,” Meta wrote.
In particular, the company complained that its inability to access domain name registration information (known as WHOIS) has inhibited its capacity to swiftly investigate abusive domains, which are increasingly prevalent and have led to a rise in attempts to dispute abusive domains.
The problem is that the fees to initiate a “domain name dispute administrative procedure” at the World Intellectual Property Office (WIPO) can stretch into thousands of dollars to recover just 10 domain names, in addition to legal fees.
“While some brands, like ours, opt to pursue this effort, many may not,” Meta warned. “This means that imposters continue to operate online, knowing that the costs of taking abusive domains down is prohibitively high for many organizations – including news outlets, civil society organizations, or governments.”
The company called for registrars and registries to be required to take proactive steps to address domain registration abuse, including suspending customers that are known bad actors and requiring verification for domain names that use famous brands and words suggestive of fraud, like “login,” “password,” “security,” “help center,” or “verification.”
It acknowledged that domain impersonation was “far from” the only cross-platform tactic used by threat actors to trick people into either “visiting fictitious news outlets, falling for phishing schemes, installing malware, or losing money to scammers.”
However, the existing mechanisms to redress abuse “are not sufficient to have material impact at scale,” Meta said, adding that “industry-wide action is needed to protect people against these tactics and raise our collective defenses.”
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79