Report: Pro-China influence operation targeted U.S. midterms
A new report from cybersecurity firm Mandiant says researchers recently observed a pro-China influence campaign targeting the U.S. midterm elections.
The campaign launched by the group known as DRAGONBRIDGE, which Mandiant said is likely operating “in support of the political interests of the People’s Republic of China,” included “aggressive attempts” to discredit the U.S. political system and discourage voting in the 2022 midterms — now just days away.
The campaign also pushed claims the U.S was behind the Nord Pipeline explosion and that the “China-nexus threat group APT41 is instead a U.S. government-backed actor,” according to Mandiant, which was acquired by Google earlier this year.
Recent tactics involved impersonating Intrusion Truth — a group known for exposing Chinese hackers — online, sharing plagiarized and altered news articles, and using fake accounts impersonating Americans.
But it’s not necessarily been effective.
“As with DRAGONBRIDGE activity we have previously observed, the campaign continues to fail to garner significant engagement by seemingly real individuals, and its effectiveness remains encumbered by poor execution,” the Mandiant researchers said.
What is DRAGONBRIDGE?
Mandiant has been tracking DRAGONBRIDGE since mid-2019, when the campaign’s activity involved very basic tactics, like spamming the same messages across accounts.
But it grew rapidly.
In 2021, the company reported the campaign was active ”on at least 30 social media platforms and dozens of additional websites and forums, and in languages including not just English and Chinese, but also German, Russian, Spanish, Korean, and Japanese.”
Accounts within DRAGONBRIDGE unsuccessfully attempted to physically mobilize people in the U.S. in response to the Covid-19 pandemic, according to Mandiant.
Earlier this year, the campaign also mobilized against the planned expansion of rare earths processing within the U.S., a challenge to Chinese dominance of that market.

Midterm mischief
The DRAGONBRIDGE campaign amped up efforts to sow political discord within the U.S. in recent weeks.
“Most notably, in September 2022, DRAGONBRIDGE accounts posted an English-language video across multiple social media platforms containing content attempting to discourage Americans from voting in the upcoming U.S. midterm elections,” according to Mandiant.
The video argues "the solution to America's ills is not to vote for someone," but instead "root out this ineffective and incapacitated system."
The larger influence campaign also pushed narratives about political division and a coming U.S. “civil war,” according to the report.
A recent report from Recorded Future’s Insikt team noted that China’s state-sponsored influencers were “almost certainly conducting malign influence operations targeting English and Chinese speaking US audiences with divisive political multimedia content on social media” — a shift from previous elections where the country was “less active in attempts to influence U.S. voters.”
However, James A. Lewis, Senior Vice President and Director of the Strategic Technologies Program at the Center for Strategic and International Studies, told The Record Chinese midterm efforts haven’t seemed very effective.
“The Chinese are getting better at online manipulation, but a lot of this is defensive, to deflect blame from China for hacking,” he added.
Fake news
On that front, DRAGONBRIDGE accounts shared a plagiarized, altered news article about Mandiant’s research into other hacking groups connected to China.
In March 2022, Mandiant published research about apparent efforts by the group they track as APT41 — a cybercriminal group with a history of engaging in alleged cyberespionage contracting on behalf of Chinese interests as well as hacking for personal gain — to hack into U.S. state government networks. That research was covered by the Hong Kong-based news outlet, Sing Tao Daily.
DRAGONBRIDGE accounts shared a copy of that article, but with “direct replacements” of words including China with the U.S., and states with countries, to make it seem as though the report was blaming the U.S. government for APT41’s work, according to Mandiant. The accounts also shared memes suggesting various U.S. government agencies were behind the group — including one based on a 2014 The Nib political cartoon about National Security Agency surveillance.
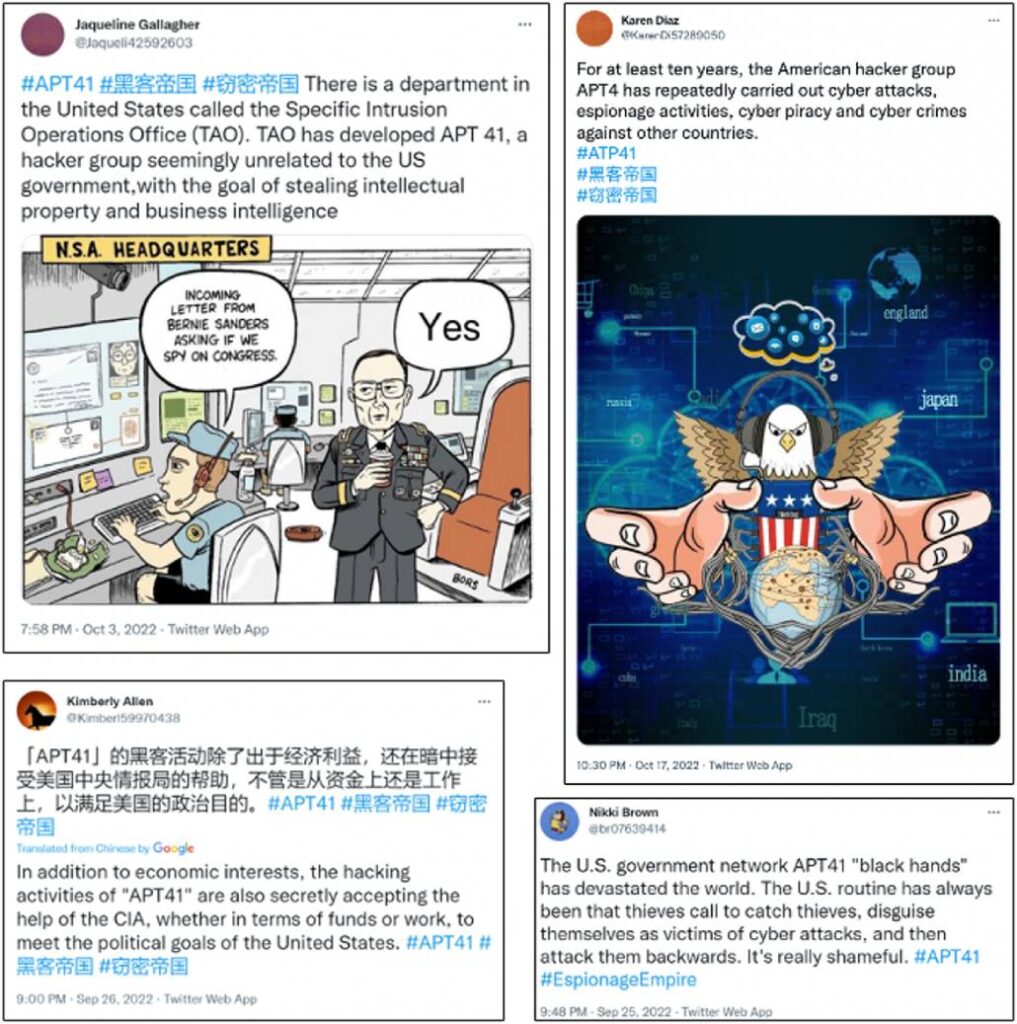
Mandiant researchers also assessed with “moderate to high confidence” that a series of eight Twitter accounts created in September that impersonated Intrusion Group, sharing plagiarized and altered tweets about APT41, were part of DRAGONBRIDGE.
Andrea Peterson
(they/them) is a longtime cybersecurity journalist who cut their teeth covering technology policy at ThinkProgress (RIP) and The Washington Post before doing deep-dive public records investigations at the Project on Government Oversight and American Oversight.



