Report: Lessons learned from Russia’s cyberattacks targeting Ukraine
Russian tanks crossed the Ukrainian border on February 24, but the Kremlin’s first shots at Ukraine’s critical infrastructure were fired a few days before. The attack wasn’t on the ground — it was in cyberspace.
Since the beginning of the full-scale war, Russia has carried out nearly 800 cyberattacks against Ukraine, according to Ukraine’s top cybersecurity official Yuriy Shchygol — three times more than in the same period last year. However, few of the attacks caused significant economic damage and mostly had a psychological effect, according to a report released Wednesday by the European Cyber Conflict Research Initiative.
In the report, cybersecurity specialists, academics, and government officials analyzed Russia’s approach to cyber warfare in Ukraine. Here are some of their biggest findings:
Russia may not have “reserve” cyber capability
Before the outbreak of the war in Ukraine, UK and U.S. officials warned about Russia's vast cyber capabilities. But with the war now in its fourth month, some are questioning if their abilities were overestimated, according to the report.
From the beginning of the conflict, Russian cyber operations have been relatively unsophisticated, sometimes just reworking known malware. The report concludes that if Russia had the ability to attack more aggressively, they would have done so at the start of the invasion. Therefore, Russia may not have any “reserve” capabilities, the report finds.
This does not imply, however, that more destructive cyberattacks will not occur in the future, as Russia continues to access Ukraine’s information infrastructure, the report says.
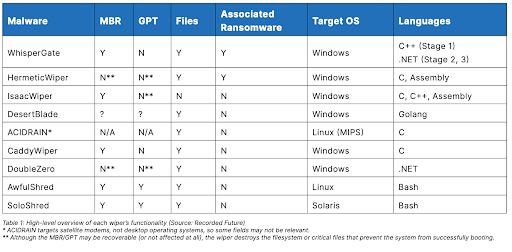
Strategic value of cyber operations
Some of Russia’s high-profile cyber operations in Ukraine – including the Industroyer 2 attack, the Viasat hack and frequent compromises of the Ukrainian Ministry of Foreign Affairs – have had a significant psychological effect. There is little evidence that cyberattacks caused significant damage to Ukraine's political, economic, and social interests.
Ukraine may not be a good “test case” to see how a cyber war with Russia could play out elsewhere in the world: Since Russia's 2014 invasion, all major cyber attacks in Ukraine have occurred during a war, meaning that cyberspace took a secondary role next to the use of conventional military weapons.
Hackers may experience burnout
Russia has rapidly advanced into Ukraine's cyberspace, developing, deploying, detecting, and mitigating its cyber capabilities “at an unprecedented pace,” according to the report.
The high operational tempo could have potential effects on Russia’s exhausted cyber forces, however. Experts expect high levels of Russian employee burnout due to the difficulty in maintaining and motivating sufficiently skilled personnel over longer periods of time.
According to a 2018 survey by Josiah Dykstra and Celeste Lyn Paul from the U.S. Department of Defense, fatigue and frustration mount when a cyber operation lasts more than five hours due to the required cognitive efforts.
Non-state actors play a big role
Several non-state hacking groups have played an important role during the cyber war between Ukraine and Russia.
For example, the Conti team, responsible for numerous ransomware attacks, announced its full support of Russia.
Ukraine has used the help of its volunteer IT Army, whose members have mostly conducted coordinated DDoS attacks on Russia.
Another group is the Belarusian Cyber Partisans. It has claimed responsibility for several major cyber attacks, including the one against the Belarusian railway system that reportedly halted Russian ground artillery and troop movement into Ukraine.
There have also been reports of Chinese espionage activities in Ukraine and the region.
For example, Google’s Threat Analysis Group discovered an ongoing cyber operation in Ukraine from a Chinese hacking group, known as APT31, targeting Gmail users affiliated with the U.S. government. It is still not clear, however, how Chinese cyber actors are able to exploit the war in Ukraine.
Daryna Antoniuk
is a reporter for Recorded Future News based in Ukraine. She writes about cybersecurity startups, cyberattacks in Eastern Europe and the state of the cyberwar between Ukraine and Russia. She previously was a tech reporter for Forbes Ukraine. Her work has also been published at Sifted, The Kyiv Independent and The Kyiv Post.



