RedLine Stealer identified as primary source of stolen credentials on two dark web markets
The vast majority of stolen credentials currently sold on two dark web underground markets have been collected using the RedLine Stealer malware, Insikt Group, the cybersecurity research arm of Recorded Future, has discovered.
First spotted in March 2020, the RedLine Stealer is part of the infostealer family, a type of malware that once it infects a computer, its primary purpose is to collect as much user data as possible and then send it to the attackers, who typically put it up for sale online.
Data collection capabilities included with the RedLine Stealer include the ability to extract login credentials from web browsers, FTP clients, email apps, instant messaging clients, and VPNs.
In addition, RedLine can also extract authentication cookies and card numbers stored inside browsers, chat logs, local files, and cryptocurrency wallet databases.
Initially developed by a programmer named REDGlade, the malware has been sold on several underground hacking forums since March 2020. After the stealer received positive reviews in a hacking forum thread, pirated versions of the RedLine Stealer were also released on hacking forums a few months later, in August this year, allowing it to spread to even more threat actors who didn't have to pay for it.
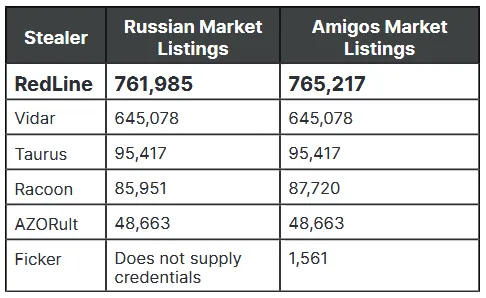
But even prior to the release of the cracked version, RedLine had undeniably found a loyal customer base. According to an Insikt Group report published last week, the vast majority of stolen credentials that are being offered for sale on two underground markets originate from systems that were infected with the RedLine Stealer.
"Both Amigos Market and Russian Market were identified by Insikt Group (June 2021) posting identical listings regularly that contained the same timestamps, infostealer variants used, geographical locations of affected machines, and ISPs," Insikt Researchers said.
The Insikt team's findings come after a similar report from threat intelligence firm KELA from February 2020, which found that around 90% of stolen credentials sold on the Genesis Market came from infections with the AZORult infostealer.
The two reports show that underground cybercrime markets are fragmented and typically work with their own separate suppliers, similar to how legitimate markets have their own preferences for certain business partners.
This fragmentation opens the door to crippling the supply of several underground markets by going after the makers and sellers of these infostealers.
The perfect example of what this disruption could achieve came in February 2020 when a Chrome update (that changed how credentials were stored inside the browser) stopped the flow of new stolen credentials on Genesis Market for months until the AZORult stealer was updated to handle the new format.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.