RedCurl hacking group returns with new attacks
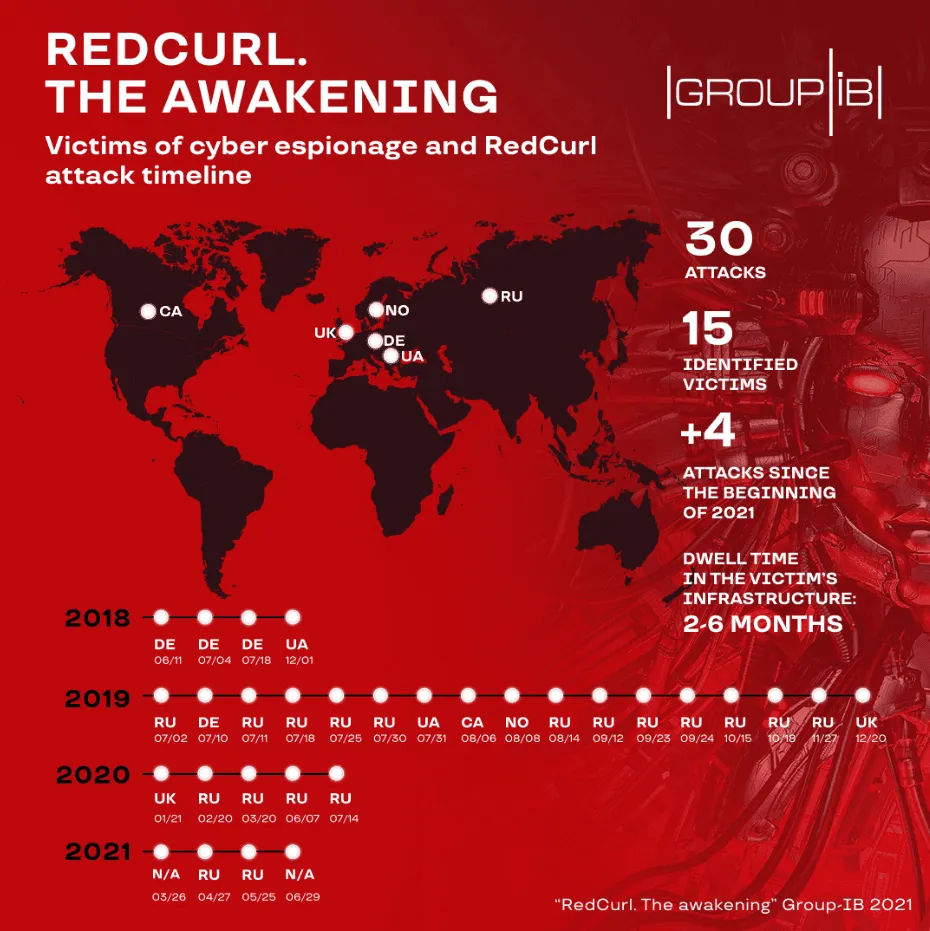
Even after its operations were publicly exposed in August 2020, the RedCurl hacking group has continued to carry out new intrusions and has breached at least four companies this year, according to a new report from security firm Group-IB.
Targets hacked this year included two companies based in Russia, along with two others that Group-IB researchers said they couldn't identify.
All in all, the group has now been linked to at least 30 intrusions since 2018, when it began operating, with victims located in the UK, Germany, Canada, Norway, Russia, and Ukraine.
Group-IB, which it previously detailed the group's modus operandi in a report last year, said RedCurl consists of Russian-speaking members who have primarily engaged in corporate espionage, targeting companies across the world to steal documents that contain commercial secrets and employee personal data.
Besides discovering new attacks, Group-IB's latest report also notes that RedCurl operators have done little to change their tactics besides a few updates to the tools they used during intrusions.
However, researchers did find one interesting tidbit in one of their investigations, notably that RedCurl operators had changed the time on a compromised system to UTC+3, the timezone for regions like Minsk, Moscow, Turkey, and many countries in the Middle East, where hacking groups have often been discovered to operate.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



