Ransomware gang exploited a zero-day in Microsoft security feature, Google says
Financially motivated hackers are using a previously undocumented bug in Microsoft’s SmartScreen security feature to spread the Magniber ransomware, according to a new report.
The cybercriminals have been able to exploit the zero-day vulnerability in SmartScreen since December, researchers from Google’s Threat Analysis Group (TAG) said. The Google team reported its findings about the bug and the ransomware group’s exploitation of it to Microsoft on February 15. Microsoft released a patch for the bug — CVE-2023-24880 — on Tuesday.
SmartScreen is intended to catch phishing attempts and malware as part of Windows versions 10 and 11, as well as the company’s Edge web browser. A Microsoft spokesperson said customers who have applied the most recent patch are protected.
TAG analysts said they have seen over 100,000 downloads of malicious MSI files used in the ransomware campaign since January 2023, with 80% of those downloads by users in Europe. MSI files are similar to the familiar .EXE files, in that both types are used to install and launch Windows programs.
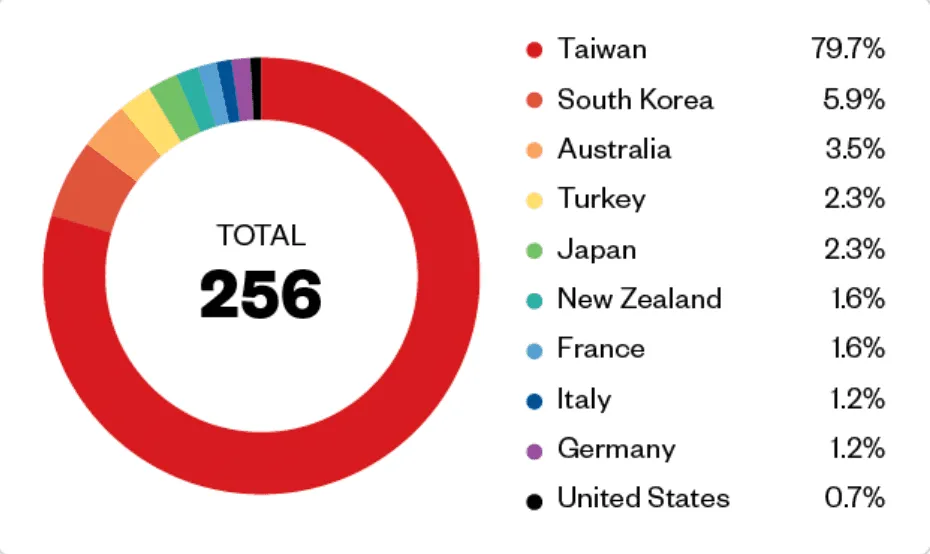
The researchers noted that typically the Magniber ransomware has been aimed at organizations in South Korea and Taiwan. Cybersecurity companies began tracking it about six years ago.
TAG’s discovery marks the second time in about six months that the operators of Magniber have used zero-days to dodge SmartScreen and trick computer users into downloading the disguised ransomware from infected websites.
The Google team’s research builds on previous work done by experts at HP, which found in October that Magniber campaigns involved the exploitation of CVE-2022-44698 — a separate vulnerability affecting SmartScreen. Other hackers began to exploit that bug before Microsoft released a patch in December 2022.
During that campaign, the Magniber actors used JScript files with a malformed signature to force SmartScreen to return an error, eventually allowing the hackers to bypass a security warning and send their malware.
When Microsoft blocked that avenue, the Magniber group found a similar way to disrupt SmartScreen. The TAG researchers found that the infected MSI files caused SmartScreen to behave the way the JScript files did: The Microsoft feature returned an error, allowing attackers to bypass a security warning. In this case, it was a dialog box that displays when a file runs afoul of Mark-of-the-Web (MotW), another browser feature that guards against malicious files.
“Because the root cause behind the SmartScreen security bypass was not addressed, the attackers were able to quickly identify a different variant of the original bug,” the Google researchers said. The goal, they said, should be to “correctly and comprehensively” fix such problems.
“This security bypass is an example of a larger trend Project Zero has highlighted previously: vendors often release narrow patches, creating an opportunity for attackers to iterate and discover new variants,” the researchers said. “When patching a security issue, there is tension between a localized, reliable fix, and a potentially harder fix of the underlying root cause issue.”
First spotted in late 2017, the Magniber ransomware was exclusively active in South Korea for many years before expanding to Taiwan.
The cybercriminals were previously implicated in attacks exploiting several other Microsoft bugs, including CVE-2022-41091, which was also a MotW bug, as well as the infamous PrintNightmare vulnerability, CVE-2021-34527.
The Magniber group has previously used the Magnitude exploit kit — a web-based app designed to infect users by exploiting browser vulnerabilities — to distribute malicious payloads since at least 2018.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



