Ransomware revenue fell by $300 million in 2022 as more victims refuse to pay: report
Revenues brought in from ransomware attacks fell from $765.6 million in 2021 to $456.8 million in 2022, according to a new report.
Experts from blockchain research firm Chainalysis attributed the drop to a variety of factors, most notably that more victims are simply refusing to pay up when threatened by criminal groups.
The company tracks the data based on cryptocurrency addresses known to be controlled by ransomware actors, but they noted that the totals are likely far greater because there are many addresses that they have yet to identify. As an example, when they released their 2021 report, they had only identified $602 million in ransomware payments before revising that figure throughout 2022 as more addresses were discovered.
“Still, the trend is clear: Ransomware payments are significantly down,” the researchers said.
“However, that doesn’t mean attacks are down, or at least not as much as the drastic dropoff in payments would suggest. Instead, we believe that much of the decline is due to victim organizations increasingly refusing to pay ransomware attackers.”
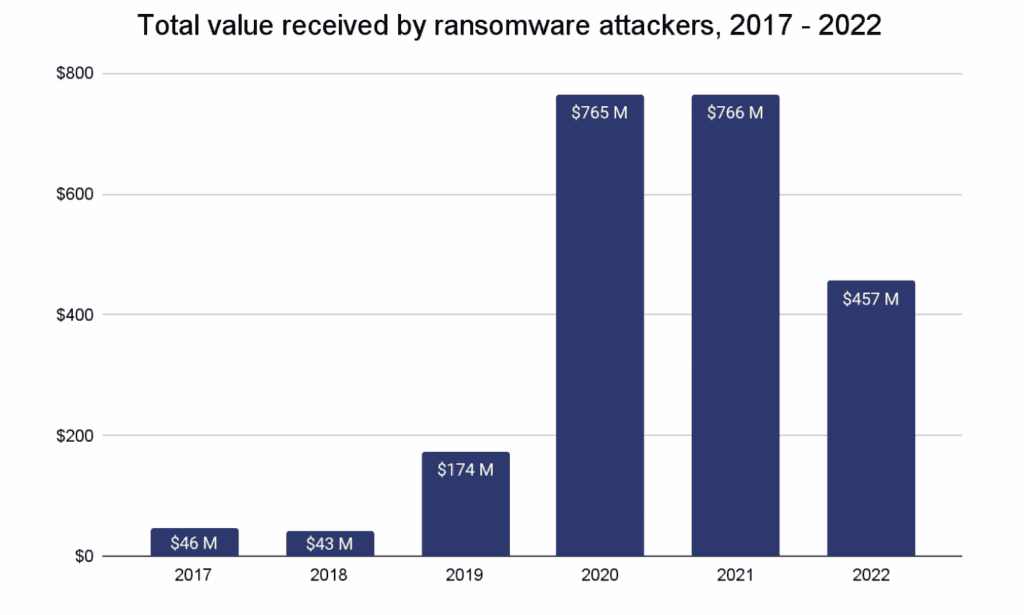
Image: Chainalysis
Chainalysis researchers spoke with several ransomware experts to check whether their theory was correct. Michael Phillips, chief claims officer of cyber insurance firm Resilience, confirmed that several “meaningful disruptions” were driving the downturn in ransomware revenue.
These disruptions included Russia’s invasion of Ukraine and law enforcement actions against ransomware gangs that included arrests and the seizure of ransoms.
Recorded Future intelligence analyst and ransomware expert Allan Liska shared some of his own data with Chainalysis, explaining that his examination of data leak sites showed that ransomware attacks decreased by 10.4% in 2022 – from 2,865 attacks in 2021 to 2,566 in 2022.
The researchers asked Coveware’s Bill Siegel for further explanation on the steep drop in ransomware revenue and he provided them with client data from the last four years.
Since 2019, victim payment rates fell from 76% to 41% – in large part because paying ransoms now carries the added risk of violating U.S. sanctions.
In September 2021, the U.S. Department of the Treasury’s Office of Foreign Assets Control published an advisory explaining that they would begin issuing civil penalties to companies and organizations that violated sanctions on ransomware groups and their leaders.
Even companies that did not know they were violating the sanctions would be liable for penalties under the order.
“With the threat of sanctions looming, there’s the added threat of legal consequences for paying [ransomware attackers],” said Liska, echoing Siegel's comment that his firm refuses to pay a ransom if there is any concern it may violate sanctions.
“Cyber insurance has really taken the lead in tightening not only who they will insure, but also what insurance payments can be used for, so they are much less likely to allow their clients to use an insurance payout to pay a ransom,” Liska added.
Insurance companies have also forced companies and organizations to meet stringent cybersecurity and backup measures in order to qualify for coverage in the first place, according to Phillips, who attributed the drop in payments to the increased ability of organizations to recover from attacks.
"An increased focus on underwriting against factors that contribute to ransomware has led to lower incident costs for companies and contributed to a decreasing trend in extortion payment,” he told Chainalysis.
Siegel explained that many insurance firms now demand companies have backup systems, endpoint detection and response systems as well as multi-factor authentication.
The features don't stop the attacks but prepare organizations and give them the option not to pay “unless the payment is economically justified due to the severity of the impact being experienced,” all three experts said.
Theresa Le, chief claims officer at cyber insurance firm Cowbell, told The Record that they now provide incentives to encourage policyholders to improve their cybersecurity.
"Policyholders have tightened their cybersecurity controls driven by cyber insurers' underwriting requirements," Le said.
"With controls such as viable and tested backups, employees training on phishing emails, and the systematic deployment of MFA, many businesses have either thwarted ransomware attacks or significantly reduced the severity of a ransomware incident by having a recovery strategy that does not include making the extortion payment."
Explosion in ransomware strains
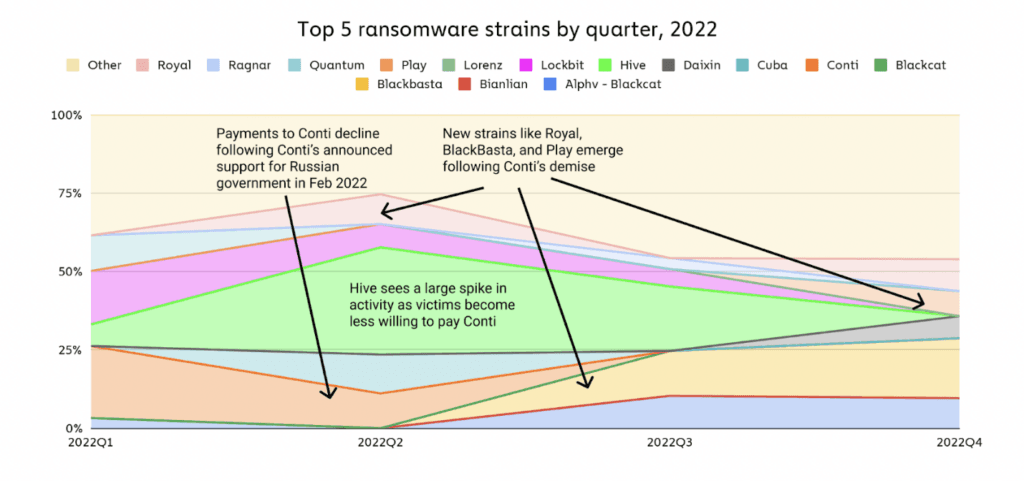
Image: Chainalysis
The drop in revenue coincided with a steep increase in the number of unique ransomware strains that emerged in 2022.
While Fortinet claimed in early 2022 that there are over 10,000 active ransomware strains, revenue is concentrated on a select group.
But Chainalysis data showed that there has been significant turnover amongst the leading groups as law enforcement action took major players off the board.
“In 2022, the average ransomware strain remained active for just 70 days, down from 153 in 2021 and 265 in 2020. This activity is likely related to ransomware attackers’ efforts to obfuscate their activity, as many attackers are working with multiple strains,” the researchers said.
But despite the increase in strains, most are operating with a ransomware-as-a-service model, allowing actors to use multiple strains in attacks. Chainalysis compared it to taxi drivers who use both Uber and Lyft, switching between whichever offers the highest return at any given moment.
The report references one example shared by Microsoft where they found one actor carrying out attacks using Hive, Conti, Ryuk, and BlackCat ransomware strains.
Chainalysis data showed multiple cryptocurrency wallets that received large payments from the Dharma, Conti, and BlackCat ransomware strains at different times.
Another example of this trend was Conti – one of the most prolific ransomware groups operating for several years. The group’s support for Russia’s invasion of Ukraine caused alleged internal strife that led to the leak of internal communications.
The leaks revealed that there were connections between the group and Russia’s Federal Security Service (FSB). Those ties made victims and incident response firms wary of paying ransoms and by May, the group announced that it was shuttering.
The group quietly splintered into several smaller groups and Chainalysis found Conti affiliates working with the Suncrypt, Hive, Monti, and Lockbit strains.
“But it isn’t just Conti affiliates who have rebranded. On-chain data shows that core administrators have also begun to work with and launch other strains, including the group’s leader, who goes by the alias Stern,” the researchers said.
Stern, according to Chainalysis data, began working with strains like Quantum, Karakurt, Diavol, and Royal in 2022 following the group's closure. Blockchain data shows that the ransomware ecosystem can be boiled down to a small group of hackers essentially rotating between dozens of ransomware strains.
“The number of core individuals involved in ransomware is incredibly small versus perception, maybe a couple hundred,” Siegel told Chainalysis. “It’s the same criminals, they’re just repainting their get-away cars.”
Siegel added that affiliates and core actors are now switching between different strains more frequently than before in recent months.
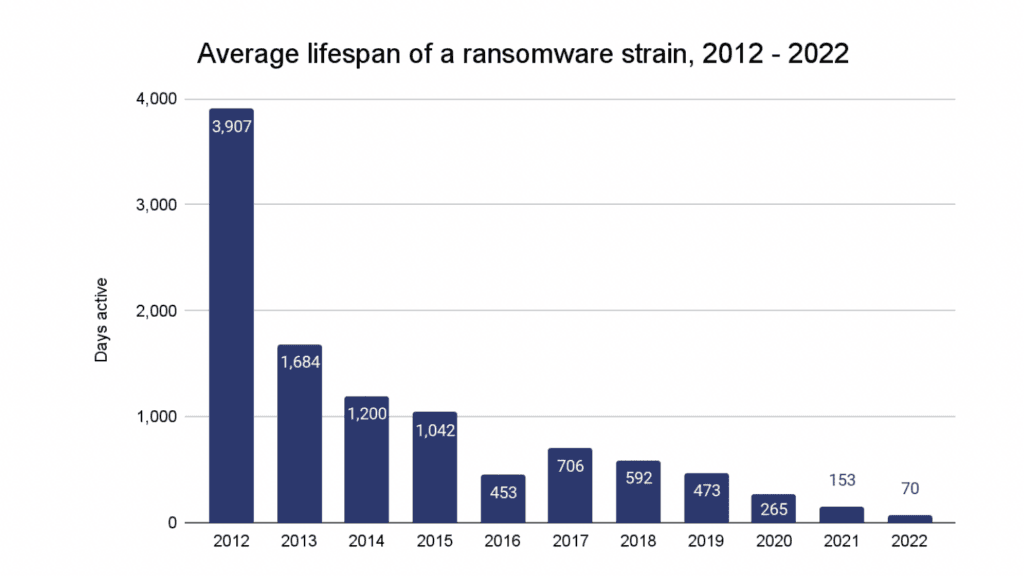
Image: Chainalysis
One other notable finding from the report was the shift in where ransomware groups send the money they have extorted from victims.
Due to law enforcement action against several cryptocurrency exchanges and mixing services, groups are increasingly turning to mainstream exchanges to launder their stolen funds.
The share of ransomware revenue sent to mainstream exchanges — which Chainalysis would not name — grew to 48.3% in 2022.
“The exchanges that receive ransomware funds are mostly concentrated at a few offshore exchanges. But ransomware groups’ use of legitimate exchanges to cash out ransoms represents an opportunity for law enforcement to work with those exchanges to freeze and seize funds,” Jackie Koven, head of cyber threat intelligence at Chainalysis, told The Record.
“The decreased use of darknet markets to launder funds is connected to this year’s shutdown of Hydra, which was previously the largest darknet market.”
When pressed on why governments and legitimate exchanges were allowing hundreds of millions of dollars in ransom payments to flow through their platforms, Koven said that what matters is what exchanges do after they have detected the illicit activity.
"All exchanges will receive illicit funds. What you can't see on the blockchain is whether they freeze them and report it if they are known to be illicit at the time of transaction, or report them if their illicit nature becomes known later," Koven explained.
"Most ransomware funds go to offshore exchanges — with different regulatory regimes and due process. Tracking funds and international law enforcement collaboration can lead to fantastic outcomes like what we just saw with Bitzlato — which happens to be one of the unnamed services laundering ransom payments in our report."
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



