Ransomware gangs are abusing a zero-day in EntroLink VPN appliances
Multiple ransomware gangs have weaponized and are abusing a zero-day in EntroLink VPN appliances after an exploit was released on an underground cybercrime forum at the start of September 2021.
The zero-day is believed to impact EntroLink PPX-AnyLink devices, popular with South Korean companies, and used as user authentication gateways and VPNs to allow employees remote access to company networks and internal resources.
An exploit targeting these devices was released last month, on September 13, 2021. The exploit, initially sold on another forum for $50,000, was released for free by the administrator of a newly-launched cybercrime forum in what appears to be a promotional stunt meant to raise the site's profile among other cybercrime groups.
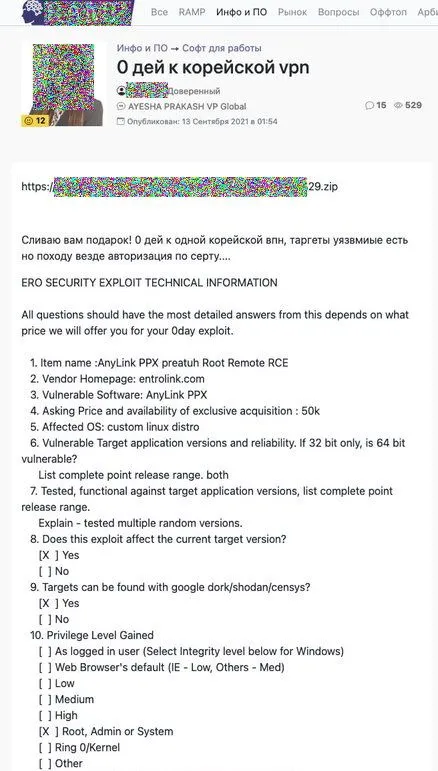
According to the forum post, the exploit is still unpatched, exploits a network protocol, and grants remote code execution with root-level access to PPX-AnyLink devices.
The post also describes the bug as an input validation issue and that the exploit is self-contained and only needs a few seconds to compromise a device.
Since the exploit's release, affiliates for the BlackMatter and LockBit ransomware operations have been linked to possible intrusions where this exploit might have been used, according to a researcher who is currently tracking and investigating ransomware attacks.
EntroLink, the South Korean networking vendor, was notified of the exploit's release by the security researcher.
The company did not engage with the researcher, and it also did not return a request for comment sent via email by The Record last week. During a phone call, a company spokesperson also refused to connect this reporter to a company representative responsible for product security.
The EntroLink PPX-AnyLink exploit now becomes the 54th zero-day vulnerability that ransomware gangs are currently known to abuse, according to a tracker managed by security researchers Allan Liska and Pancak3.
Updates include $MSFT Office CVE-2021-38646 and @billquick’s web suite CVE-2021-42258.
— pancak3 (@pancak3lullz) October 25, 2021
Also, I feel enough time has passed since continuously trying to reach the company with no response to uncensor the EntroLink PPX-AnyLink 0day item.
Cc: @uuallan pic.twitter.com/l6vetBONVu
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.


