Ransomware Gang Threatens To Launch DDoS Attacks, Call Reporters and Business Partners
The operators of the REvil (aka Sodinokibi) ransomware said they plan to expand their arsenal of extortion tactics against victims who refuse to pay ransom demands.
New tactics will include calling journalists or business partners to expose a victim's breach and launching DDoS attacks against a company's IT infrastructure in order to delay recovery efforts.
The new "capabilities" were announced this week by Unknown, the public spokesperson of the REvil Ransomware-as-a-Service (RaaS), in a post on a publicly accessible forum dedicated to Russian-speaking cybercriminals.
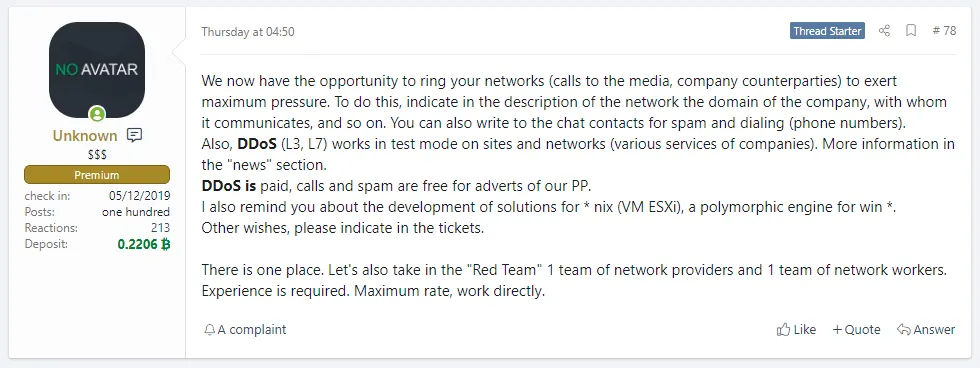
The REvil gang has been using this and other forum threads to advertise their service's capabilities to other cybercrime operators, hoping they could partner with groups specialized in breaching corporate networks.
In addition, the forum post also claimed the REvil gang was working on developing capabilities for infecting VMware ESXi systems (to attack corporate networks where virtual machines are often deployed) and a polymorphic engine (to allow the REvil ransomware strain to mutate on its own and better avoid antivirus checks).
None of the capabilities announced this week are truly original or exclusive to the REvil gang, which appears to be copying what other ransomware operations had already implemented last year.
For example, the Avaddon, SunCrypt, and Ragnar Locker ransomware gangs have been known to use DDoS attacks to put additional pressure on their victims.
On the other side, gangs like Sekhmet, Maze, Conti, and Ryuk have previously called victims to make threats or harass employees. The tactic of calling journalists and business partners is a new variation, but one that is likely to work, as some companies would want to avoid publicly disclosing breaches that would open them to fines and regulatory scrutiny.
And last but not least, gangs like Darkside and RansomExx have been seen since at least late last year targeting ESXi systems with great success.
Encryption feels like it is less important than then extortionAllan Liska, Recorded Future
In a conversation with The Record on Saturday, Allan Liska, a security researcher at Recorded Future, said these new additions fit in with the general trend observed on the ransomware scene where "encryption feels like it is less important than then extortion."
The best and most recent example of this trend is the cooperation between FIN11, a threat actor who exploited a zero-day in Accellion FTA devices, and the Clop ransomware gang.
As pointed out by security firm FireEye in a recent report, after FIN11 breached tens of companies across the globe and stole sensitive files from their FTA appliances, samples of the data were then posted on the Clop ransomware's leak site as a way to put pressure on victims and have them pay extortion demands to prevent full —and likely very damaging— leaks.
As ransomware gangs continue to target corporate environments, the line between a classic ransomware attack and a data breach will continue to blur, and ransomware may only be the public face of such incidents that often are more complicated than getting a decryption key.
The Record would like to thank @3xp0rtblog for the tip!
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



