Ransomware gang targets Microsoft SharePoint servers for the first time
Microsoft SharePoint servers have now joined the list of network devices being abused as an entry vector into corporate networks by ransomware gangs.
SharePoint now joins a list that also includes Citrix gateways, F5 BIG-IP load balancers, Microsoft Exchange email servers, and Pulse Secure, Fortinet, and Palo Alto Network VPNs.
New Hello (WickrMe) ransomware targets SharePoint servers
The group behind the attacks targeting SharePoint servers is a new ransomware operation that was first seen at the end of 2020.
The group is tracked by security vendors under the codenames of Hello or the WickrMe ransomware—because of its use of Wickr encrypted instant messaging accounts as a way for victims to reach out and negotiate the ransom fee.
Typical Hello/WickrMe attacks usually involve the use of a publicly known exploit for CVE-2019-0604, a well-known vulnerability in Microsoft's SharePoint team collaboration servers.
The bug allows attackers to take control over the SharePoint server to drop a web shell, which they later use to install a Cobalt Strike beacon (backdoor) as a way to run automated PowerShell scripts that eventually download and install the final payload—the Hello ransomware.
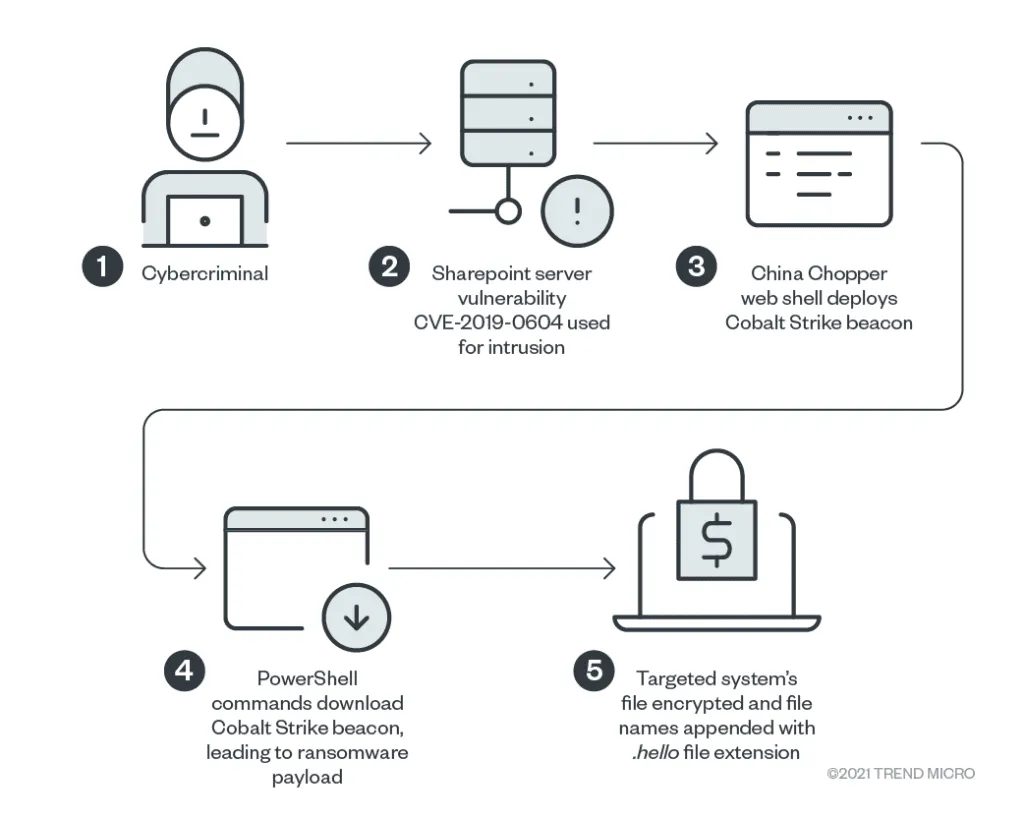
The first Hello/WickrMe attacks where attackers used SharePoint as the entry vector into a company's network were detected in January by security firm Pondurance, but in a report published this week, Trend Micro said the attacks are still ongoing.
Microsoft warned companies last year
While the Hello/WickrMe attacks mark the first time that a ransomware gang targeted SharePoint servers, the attacks did not come as a surprise.
In the midst of an epidemic of ransomware gangs using networking devices as entry points for their attacks, Microsoft published a blog post in April 2020 urging administrators to patch a collection of vulnerabilities, including CVE-2019-0604, which the OS maker believed would soon be targeted by ransomware groups.
The inclusion of the SharePoint bug in Microsoft's blog came after both cybercrime operators and state-sponsored espionage groups targeted SharePoint systems with exploits for the CVE-2019-0604 bug since at least May 2019, when exploits for the bug were posted online.
While it took a few months for Microsoft's foreshadowing to come true, SharePoint server owners don't have any more excuses to avoid patching their systems, if they haven't done so already.
In a conversation with The Record earlier today, Troy Mursch, chief research officer and co-founder of threat intelligence firm Bad Packets said that with the exception of April 4, there haven't been any significant upticks in SharePoint internet scans.
However, while threat actors aren't scanning and exploiting SharePoint systems right now, it may be possible that the Hello/WickrMe gang is using web shells that were planted on SharePoint servers months before.
(It is currently unclear if the Hello/WickrMe ransomware is hacking SharePoint servers itself, or just renting access to already hacked systems from so-called "initial access broker," a common practice with ransomware gangs today.)
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



