Ransomware gang leaks data from US military contractor the PDI Group
A major supplier of military equipment to the US Air Force and militaries across the globe appears to have fallen victim to a ransomware attack.
The victim is the PDI Group, an Ohio-based company that manufactures a wide range of ground support equipment for military needs, such as dollies, trollies, and platforms for transporting weapons, engines, and airplane parts during servicing operations.
On Tuesday, the criminal group behind the Babuk Locker ransomware created a page on their "leak site" under the company's name threatening to leak more than 700 GB of data they claim to have stolen from PDI's internal network unless the company gave in to its ransom demands.
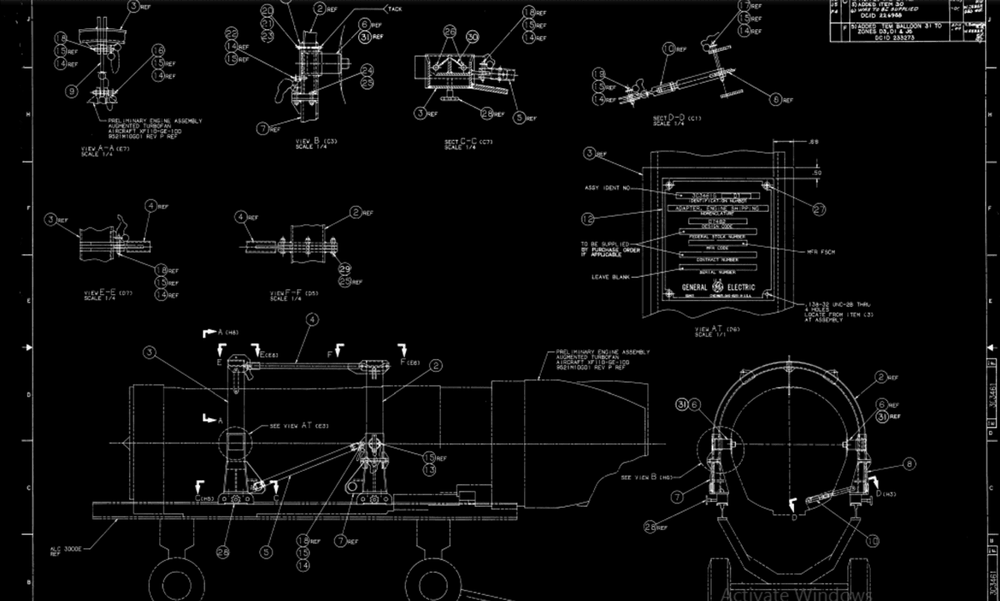
To prove their claims, the Babuk Locker operators posted a series of screenshots of several internal documents they claim to have stolen from PDI's internal network, including schematics, one of which appears to describe one of PDI's aircraft engine trailers.

Web pages like the one above are a common tactic today. More than 20 different ransomware groups currently operate leak sites, as attackers slowly evolved to also stealing data before encrypting it.
This stolen data is then leveraged to put additional pressure on companies that may want to restore from backups but might not want to have proprietary and customer data leaked online, which would expose them to fines and class-action lawsuits.
Today, these encrypt-or-leak extortion schemes usually take place across four stages:
Ransomware gang encrypts files and demands a fee for the decryption key in private.Ransomware gang creates a page on their leak site as a warning for the victim that they plan to leak files.Ransomware gang leaks a partial set of files.Ransomware gang leaks all stolen files if victims still refuse to pay.
Earlier today, the PDI Group incident went into the third stage of this type of extortion scheme after the Babuk Locker gang published a 120 MB archive file containing purchase orders for more than 350+ of PDI's past customers.
The files, provided in an archive labeled cc.zip, also contained clear text, full credit card details for some of the company's past customers, but the vast majority of card numbers seen by The Record appear to have been for cards that have long expired.
Reached out for comment on Wednesday, a PDI spokesperson hanged up the call when we mentioned we were seeking comment about its ransomware incident.
Spokespersons for the US Department of Defense and the Cybersecurity and Infrastructure Security Agency deferred to the PDI Group in regards to the incident and were unable to confirm if the company had reported the attack to its customers.
The PDI Group now joins a long list of military contractors that have been hit by ransomware gangs in recent years. Previous companies include the likes of:
Electronic Warfare Associates (EWA), which provides electronic weapons systems.Fighter jet maker Dassault Falcon.Airplane maker Bombardier.Airplane parts maker Asco.Swiss helicopter maker Kopter.Brazilian airplane maker Embraer.
In an interview with The Record this month, the public spokesperson for the REvil ransomware said their operators often gain access to military-related targets.
"I know at the very least that several affiliates have access to a ballistic missile launch system, one to a US Navy cruiser, a third to a nuclear power plant, and a fourth to a weapons factory," the REvil spokesperson said.
As for the group behind the PDI intrusion, the Babuk Locker is one of the newest ransomware cartels active today, having begun operations at the start of the year, with PDI being their biggest target to date. Details about the group's modus operandi are available in this PDF report from cybersecurity firm McAfee.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.