Praying Mantis APT targets IIS servers with ASP.NET exploits
A new advanced persistent threat (APT) group has been seen carrying out attacks against Microsoft IIS web servers using old exploits in ASP.NET applications in order to plant a backdoor and then pivot to companys' internal networks.
Tracked as Praying Mantis or TG1021, the group's attacks have been documented in a report published earlier today by Israeli security firm Sygnia.
"These attacks targeted prominent organizations and compromised their networks by exploiting internet-facing servers," the Sygnia team said today.
For these attacks, Praying Mantis relied on exploits to get a foothold on IIS servers running outdated ASP.NET apps and then used a malware framework that Sygnia said was custom-made to target IIS servers.
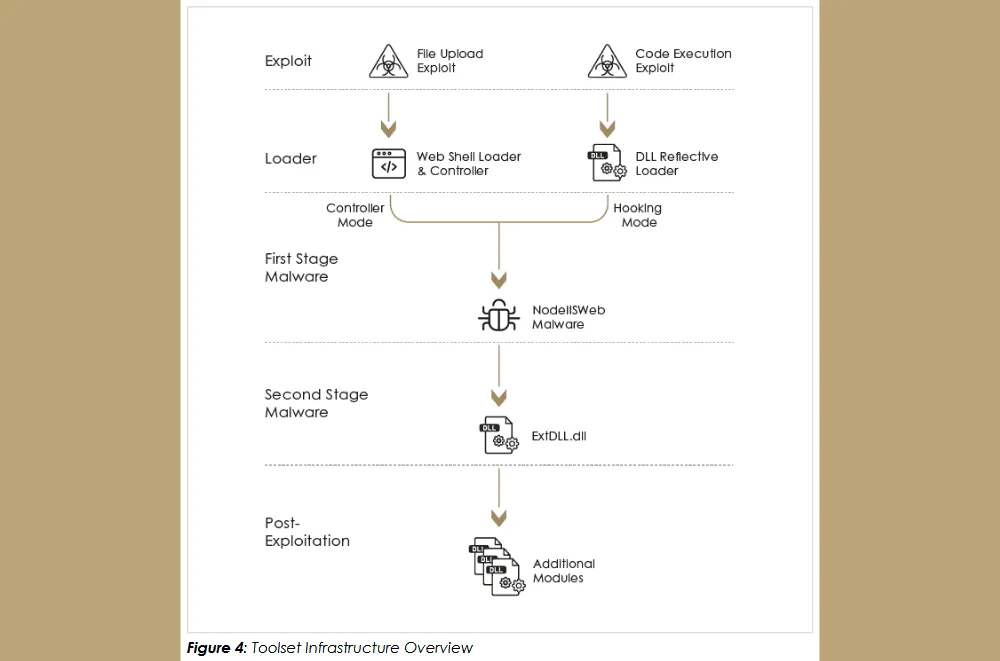
This framework, which consisted of fileless malware strains that executed inside the server's memory to avoid detection, was split into two subgroups.
The first stage group, which consisted of the NodeIISWeb malware, was designed to backdoor the IIS server and contained functionality to intercept and handle HTTP requests received by the server.
The second stage malware was designed to help Praying Mantis spread to the internal network and included several post-exploitation modules to perform network reconnaissance, elevate privileges, and move laterally within networks.
To gain their initial foothold on IIS servers, Praying Mantis typically relied on four deserialization exploits targeting Windows IIS servers and web applications, listed below:
- Checkbox Survey RCE exploit (CVE-2021-27852)
- VIEWSTATE Deserialization exploit (technical analysis)
- Two exploits targeting Telerik-UI for ASP.NET AJAX component (CVE-2019-18935, CVE-2017-11317)
Sygnia said the nature of the activity and general modus-operandi suggest Praying Mantis is an experienced threat actor highly aware of
OPSEC (operations security) procedures.
The malware used by [Praying Mantis] TG1021 shows a significant effort to avoid detection, both by actively interfering with logging mechanisms, successfully evading commercial EDRs and by silently awaiting incoming connections, rather than connecting back to a C2 channel and continuously generating traffic. Furthermore, the threat actor actively removed all disk-resident tools after using them, effectively giving up on persistency in exchange for stealth.
Sygnia Praying Mantis report
"Sygnia has identified and linked malicious activities to this group starting from mid-2020. Initial identification was through our response to a potential compromise. This gradually unfolded the attack and toolset, which made it more trackable," the Sygnia team told The Record today in an interview.
"Our belief is that the group is associated with a particular state-sponsored entity, according to its highly stealthy modus operandi and victimology. The victims were prominent companies in the US private sector," the security firm added.
In its report, Sygnia said the group's tactics, techniques, and procedures (TTPs) are similar to those described in a June 2020 security alert [PDF] from the Australian Cyber Security Centre, which detailed a series of attacks against Australian government and private organizations by a group the agency nicknamed Copy-Paste, due to its tendency to use open source public exploits.
However, some of the same exploits have also been abused by a crypto-mining gang tracked as Blue Mockingbird.
However, Sygnia has not yet made a formal attribution of the Praying Mantis attacks besides highlighting the TTP overlaps.
TG1021 (Praying Mantis) indicators of compromise (IOCs) are available in Sygnia's report.
Article updated shortly after publication with Sygnia comments.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



