PoC released for Microsoft Exchange ProxyLogon vulnerabilities
A Vietnamese security researcher has published today the first functional public proof-of-concept exploit for a group of vulnerabilities in Microsoft Exchange servers known as ProxyLogon, and which have been under heavy exploitation for the past week.
The proof-of-concept code was published on GitHub earlier today. A technical write-up (in Vietnamese) is also available on blogging platform Medium. The Record will not be linking for the time being to neither of the two.
PoC verified and deemed dangerous
Over the past few days, several ProxyLogon proof-of-concept (PoC) exploits have been published on GitHub, yet, most have been trolling attempts or did not work as intended.
Security researchers like Marcus Hutchins of Kryptos Logic, Daniel Card of PwnDefend, and John Wethington of Condition Black, have confirmed the validity of the new PoC in interviews with The Record earlier today.
According to all three, the PoC combines the CVE-2021–26855 and CVE-2021–27065 vulnerabilities to authenticate on an Exchange server and run malicious code.
The code is not usable out of the box, Card and Hutchins told The Record, but can be easily adjusted to obtain what security researchers call a "remote code execution" state.
The PoC's release today also comes after security firm Praetorian published a detailed write-up on the ProxyLogin vulnerabilities a night before but refrained from publishing a working PoC.
Several security researchers warned and showed their dismay yesterday and today that the write-up could accelerate the development of a working PoC that could invite even more threat actors to launch their own attacks.
This is a good write up, but could have waited a week...https://t.co/aB8p2Wh4BE
— nluedtke (@nluedtke1) March 10, 2021
At least ten threat actors are already exploiting Exchange servers
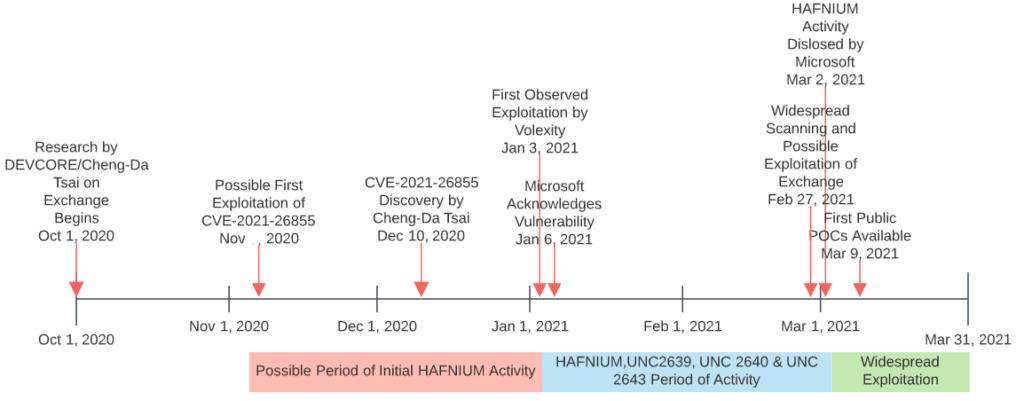
Attacks on Microsoft Exchange servers using the ProxyLogon bugs began at the start of the year, but for almost two months, they remained under the radar and only exploited by a Chinese state-sponsored hacking group named Hafnium that installed web shells on Exchange email servers around the world to spy on targets.
Mass-exploitation began last week after Microsoft made the attacks public and released patches.
In a blog post today, cybersecurity firm ESET said that at least ten threat actors are currently exploiting the ProxyLogon bugs to install backdoors on Exchange servers across the world.
According to a scan conducted by a Dutch non-profit, more than 46,000 of a total of 250,000 Exchange servers are still unpatched and exposed to attacks.
Even before today, security experts have warned that these attacks will very likely expand and also include less sophisticated but more dangerous threat actors like ransomware gangs once a public PoC is released.
"I'm hoping enough people have patched," Card told The Record. "This was inevitable but you know there will be more impact."
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.