Organizations slow to patch GoAnywhere MFT vulnerability even after Clop ransomware attacks
Dozens of organizations are still exposed to cyberattacks through a widely-abused vulnerability in GoAnywhere MFT — a web-based tool that helps organizations transfer files — according to new research.
Since February, the Clop ransomware group has exploited dozens of the world’s largest companies and governments through a zero-day vulnerability GoAnywhere tracked as CVE-2023-0669. The governments of Toronto and Tasmania were affected by the incident alongside corporate giants like Proctor & Gamble, Virgin and Hitachi.
A patch for the vulnerability was released in February but the ransomware group said it was able to compromise more than 130 organizations.
This week, researchers with cybersecurity firm Censys said there are even more victims that are still vulnerable to the issue.
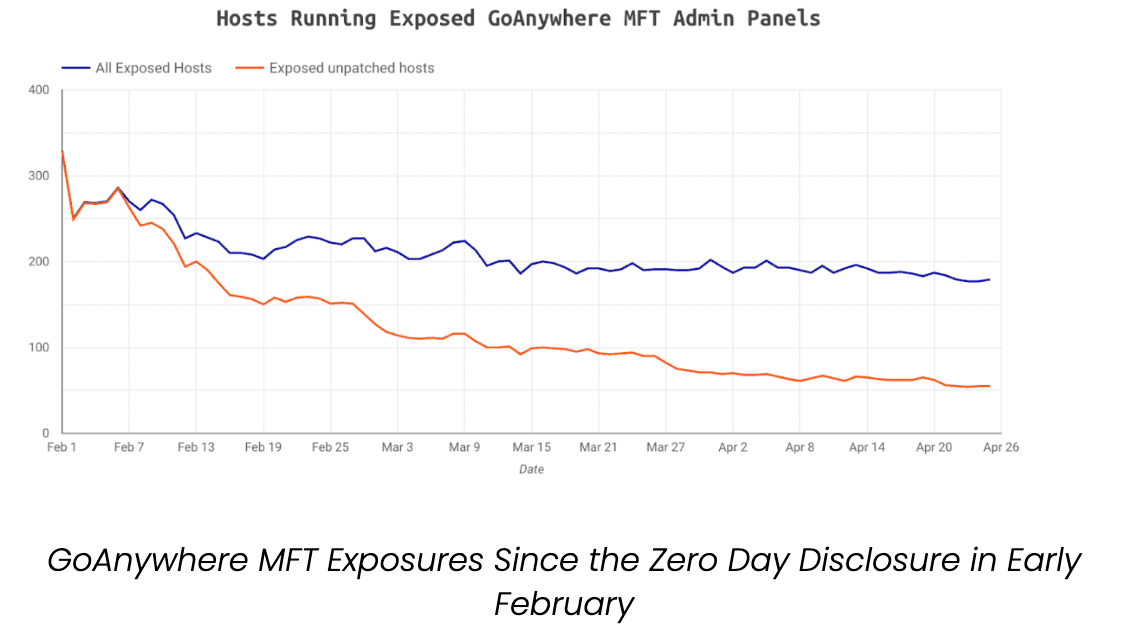 Image: Censys
Image: Censys
“Over 2 months after this zero day was disclosed, Censys continues to observe almost 180 hosts running exposed GoAnywhere MFT admin panels, with 30% of these showing indications of remaining unpatched and potentially vulnerable to this exploit,” Censys security researcher Himaja Motheram said.
“A single vulnerable instance has the potential to serve as a gateway to a data breach that could potentially impact millions of individuals.”
The findings have alarmed security experts because other ransomware groups have now been seen exploiting the vulnerability.
Security company At-Bay confirmed last week that the BlackCat/AlphV group attacked an unnamed U.S. business in February 2023 using the vulnerability. At-Bay said ransomware groups are targeting the vulnerability because GoAnywhere MFT, designed by security company Fortra, is designed to handle the secure transfer of sensitive data for organizations.
“Executing a ransomware attack by targeting the GoAnywhere MFT vulnerability is extremely easy — with the exfiltration of data near certain, and the fast delivery of the payload also guaranteed,” At-Bay explained.
“It is strongly recommended that users — especially those whose admin portals are accessible from the internet — install the patch as soon as possible.”
Censys’ Motheram said their experts have seen a “slow and steady patch response” since the fix was released on February 6.
They saw a 46% decrease in the number of exposed GoAnywhere panels since the patch was released. As of April 25, more than 179 hosts are still running exposed instances, with 55 of these “showing indications of running vulnerable versions of the software.”
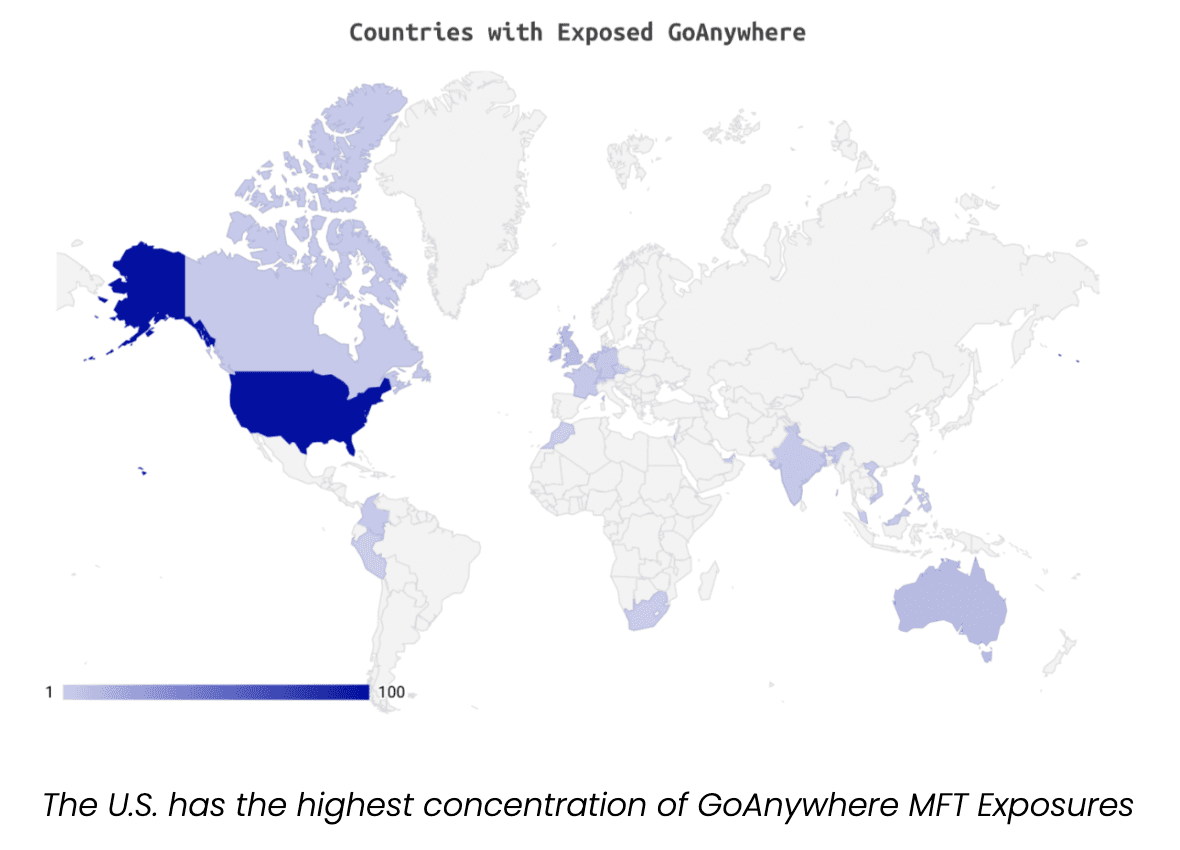 Image: Censys
Image: Censys
“Just one exposed unpatched instance can be a potential entry point for a threat actor to exploit this zero day,” she said, urging organizations to not only apply the patch but avoid exposing administration panels to the internet.
When asked about these findings, a Fortra spokesperson told Recorded Future News that a blog they published on April 17 about the issue is their “official statement on the incident and we have no further comment.”
The blog post from Fortra said that while they were first notified of the vulnerability on January 30, customers reported facing issues as early as January 18.
“We determined that customers running an admin portal exposed to the internet, which represents a small minority of customers, were at an increased risk and promptly communicated with those customers regarding mitigation of this risk,” Fortra explained.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



