On hacking forums, even the scammers aren’t safe
Cybercriminals use a range of techniques to steal victims’ money — from developing malicious software to siphon financial data to old-fashioned "rip-and-runs" — but that doesn’t mean they’re immune to falling for these scams themselves.
Scammers scamming scammers, including sometimes the scammers who have scammed them, is “an entire sub-economy” on darknet marketplaces, according to Matt Wixey, a senior threat researcher at Sophos.
In a presentation at Black Hat Europe on Wednesday, to be followed by a four-part series of online posts over the coming weeks, Wixey detailed Sophos’ in-depth investigation into roughly 600 scams across three major criminal forums.
Wixey said the research offers defenders more than just schadenfreude, it also provides “insights into forum culture; how threat actors buy and sell; their tactical and strategic priorities; their rivals and alliances; their susceptibility to deception” and, crucially, “specific, discrete intelligence” about the actors themselves.
The team focused on “two of the oldest and most prominent Russian-language cybercrime forums, Exploit and XSS,” as well as BreachForums, the successor to the English-language RaidForums which was shut down in April by law enforcement.
Scams are not unheard of among criminals and all three of these sites have arbitration mechanisms to deal with them. Exploit, which is described as “relatively exclusive” and a popular marketplace for initial access brokers, has “approximately 2,500 reported scams” in its arbitration room — bespoke locations on the forum where users can report scams and both alert others while also trying to get redress — while XSS has around 760.
"As with virtually every scam report we read, the irony of this situation was apparently lost on the victim."
— Matt Wixey, senior threat researcher at sophos
Claims about these scams are decided by the forum’s moderators. “Pretty much how all those forums work is that the moderator’s word is final,” explained Wixey to The Record.
“That is pretty much the only option they’ve got, that form of justice, because there’s no regulatory body they can go to, there’s no ombudsman or anything like that… they could potentially try and do something more democratic, maybe, but that opens them up to all sorts of influence,” he said.
The results of scamming can be significant. In one case, Sophos found an XSS user doxing a scammer, revealing not only their name, address, mobile number and social media profiles, but also the same details for the alleged scammer’s mother.
Sophos was able to spot more than $2.5 million in losses from scams across the three forums over the last 12 months.. Some scams netted into the six figures, but the median amount that claims were made for is usually quite low: $600-$500 on Exploit; $500 on XSS; and $200 on BreachForums.
“Victims have filed scam reports for as little as $2,” found Wixey. “Threat actors seem to be as indignant about having their money stolen as anyone else, no matter the amount.”
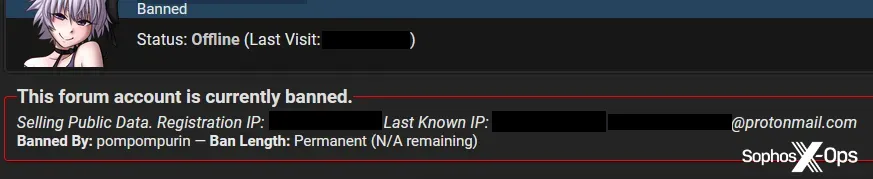
The result of these complaints is usually a ban. BreachForums, as an apparent deterrence, also publishes the offenders' sign-up email addresses and both their registration and last-seen IP addresses. Rarely some kind of compensation payment is made. In one case, the BreachForums admin even appeared to personally compensate a victim out of their own pocket due to a dispute.
Sophos discovered some prominent threat actors involved in the arbitration processes. One user, who has been accused of being the leader of the Conti and BlackBasta ransomware groups, had a complaint raised against them on the grounds that they failed to pay someone’s salary. The All Word Cards group, a prominent carding fraud operation, also claimed on XSS to have been duped by someone selling a fake vulnerability for $2,000.
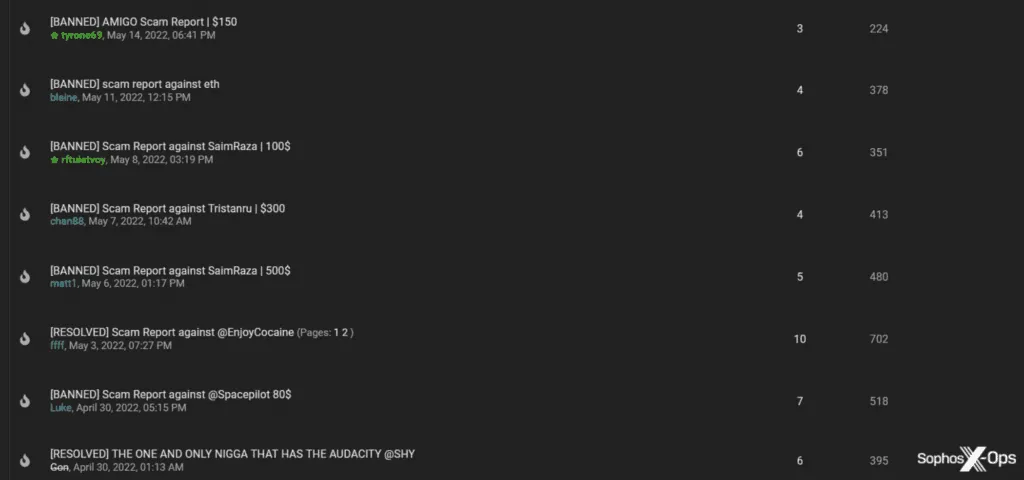
Types of scams
The most common type of scam is a “rip-and-run,” according to Sophos, where either the buyer disappears after receiving the goods or the seller runs away after receiving the payment. The forums use a couple of mechanisms to address this — accounts earn reputation points based on a history of delivery, and exchanges can often involve some form of trusted escrow.
Refusing to use such a guarantor, a middleman who holds the funds in trust and then only releases them after the buyer confirms receipt of the product, is a bannable offense on some forums, but there were cases where scammers impersonated the guarantors themselves. The administrators of the Exploit marketplace introduced a "fake Jabber checker" service for users to ensure the addresses they are speaking to are authentic.
Sophos also found a poster on XSS complaining that they had purchased a Remote Access Trojan which itself was actually a trojan designed to steal data from the purchaser’s system. “As with virtually every scam report we read, the irony of this situation was apparently lost on the victim,” wrote Wixey.
One of the most curious and successful scams the research uncovered involved 20 fake sites masquerading as legitimate marketplaces which charged a registration fee to be paid in either Bitcoin or Monero, seemingly “to take advantage of inexperienced researchers, would-be threat actors, and the genuinely curious.”
After collating information from all of the Bitcoin addresses linked to these sites, the Sophos team found the network had been lucrative, receiving more than $130,000. The researchers were also able to tie the scams to an individual threat actor, a self-described darknet methamphetamine dealer based in the United States. These findings were passed on to law enforcement, said Wixey.
Scam report posts “are a rich, and underexplored, source of intelligence,” argues Wixey.
Although generally the cybercriminals know that the forums are being monitored by law enforcement “and so often employ good operational security,” when they are “victims of crime themselves” these security measures are regularly dropped.
“Because forum rules demand proof to support scam allegations, wronged threat actors will often happily post screenshots of private conversations and source code, identifiers, transactions, chat logs, and blow-by-blow accounts of negotiations, sales, and troubleshooting,” found Sophos.
The research said that of the most recent 250 scam reports on all three forums, 39% contained screenshots, while 53% went into considerable text-only detail of the scams. The reports including screenshots often accidentally ended up revealing details of cryptocurrency addresses and links to transactions.
They leaked email addresses — sometimes visible in a browser tab in a screenshot posted by the criminals — alongside information about other individuals they were talking to on Telegram, and details about the other applications installed on their system. Sophos even observed one instance of a scam complainant sharing malware source code.
Wixey told The Record he particularly enjoyed pursuing the more niche areas of cyber threat intelligence collection: “It’s really important to look beyond the typical identifiers that you get from threat actors. Not that they’re not of value, but I think there is definitely stuff out there that we’re less aware of that could be really valuable. These arbitrations are a key example of that.”
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and is also a fellow at the European Cyber Conflict Research Initiative.



